Networking concepts
OSI vs TCP/IP Model
Network, host and Subnet mask
IP address is a Layer 3, has Network and Host with 4 bytes in IPv4 (32 bits)
Understanding IP address of the host 192.168.132.161/24
192.168.132 is the network
161 is the host
/24 or 255.255.255.0 is the subnet mask
(/24 means there are 24 bit with 1's and remaining 8 bits are 0's out of 32 bits) 11111111 11111111 11111111 00000000
The subnet mask helps to determine the host address of the machine i.e. the values with all 1's or octaves in the subnet mask will give the network address and all under the 0's gives the host address.
IP address: 192 168 132 161
IP 11000000 10101000 10000100 10100001
Subnet mask: 255 255 255 0
11111111 11111111 11111111 00000000
So the number of networks will be 2^24 and each network can have 2^8 (0-255) hosts.
Usually but not necessary hosts .1 or .254 are reserved for the default gateway and .0 or .255 to the broadcast. So 254 are available for assigning hosts.
IP packet IPv4
IP packet has a header and data sections. Header section can be from 20 t0 60 bytes and data section can be upto 65536 bytes (usually averages around 1500bytes because some are limited by MTU)
show an example of a datagram containing options:
0 1 2 3
0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
|Ver= 4 |IHL= 8 |Type of Service| Total Length = 576 |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Identification = 111 |Flg=0| Fragment Offset = 0 |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Time = 123 | Protocol = 6 | Header Checksum |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| source address |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| destination address |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Opt. Code = x | Opt. Len.= 3 | option value | Opt. Code = x |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Opt. Len. = 4 | option value | Opt. Code = 1 |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Opt. Code = y | Opt. Len. = 3 | option value | Opt. Code = 0 |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| data |
\ \
\ \
| data |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| data |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
ref: https://datatracker.ietf.org/doc/html/rfc791#section-3.3
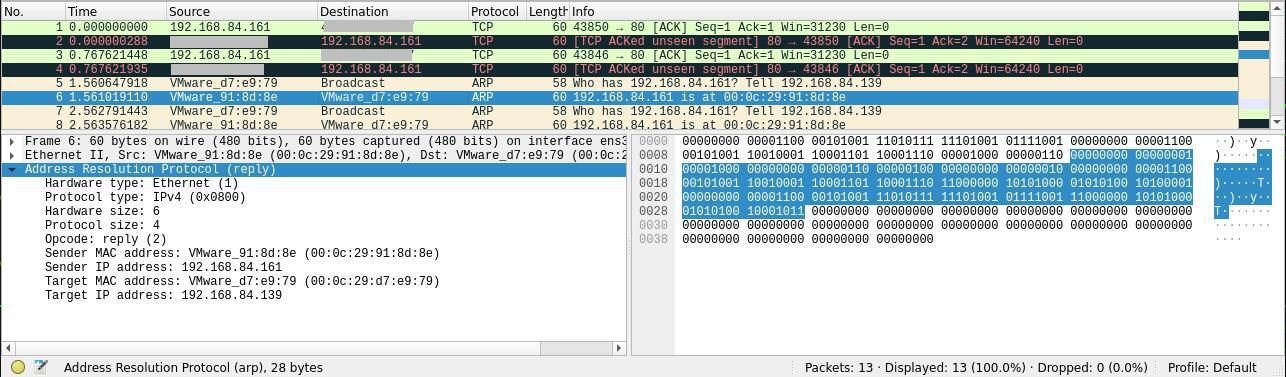
Sample data captured with wireshark and investigate IP packet.
ICMP
ICMP stands for Internet Control Message Protocol and its a layer 3 protocol. It is designed to communicate information about host and port reachability, fragmentation needs and packet expiry.
Tools like ping and traceroute use icmp to probe the machines.
example: Destination Unreachable Message
0 1 2 3
0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1 2 3 4 5 6 7 8 9 0 1
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Type | Code | Checksum |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| unused |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Internet Header + 64 bits of Original Data Datagram |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
IP Fields:
Destination Address
The source network and address from the original datagram's data.
ICMP Fields:
Type
3
Code
0 = net unreachable;
1 = host unreachable;
2 = protocol unreachable;
3 = port unreachable;
4 = fragmentation needed and DF set;
5 = source route failed.
ref: https://datatracker.ietf.org/doc/html/rfc792
ARP Address Resolution Protocol
The primary objective is to resolve the IP address into MAC address on a network (layer 2).
How does it work
When any machine needs to communicate with any device on the network:
- First checks its ARP cache (ARP cache contains mapping of IP -> MAC) for the IP, if it exist then it communicate
- Else it broadcasts the ARP request
- The device with the IP address requested ARP will recognize and respond with its MAC in its ARP reply
- The requested device will do ARP reply and updates it cache with the IP-MAC mapping
ARP Request Packet Format
0 7 15 23 31
+--------+--------+--------+--------+
| HT | PT |
+--------+--------+--------+--------+
| HAL | PAL | OP |
+--------+--------+--------+--------+
| S_HA (bytes 0-3) |
+--------+--------+--------+--------+
| S_HA (bytes 4-5)|S_L32 (bytes 0-1)|
+--------+--------+--------+--------+
|S_L32 (bytes 2-3)|S_NID (bytes 0-1)|
+--------+--------+--------+--------+
| S_NID (bytes 2-5) |
+--------+--------+--------+--------+
|S_NID (bytes 6-7)| T_HA (bytes 0-1)|
+--------+--------+--------+--------+
| T_HA (bytes 3-5) |
+--------+--------+--------+--------+
| T_L32 (bytes 0-3) |
+--------+--------+--------+--------+
| T_NID (bytes 0-3) |
+--------+--------+--------+--------+
| T_NID (bytes 4-7) |
+--------+--------+--------+--------+
ref: https://datatracker.ietf.org/doc/html/rfc6747
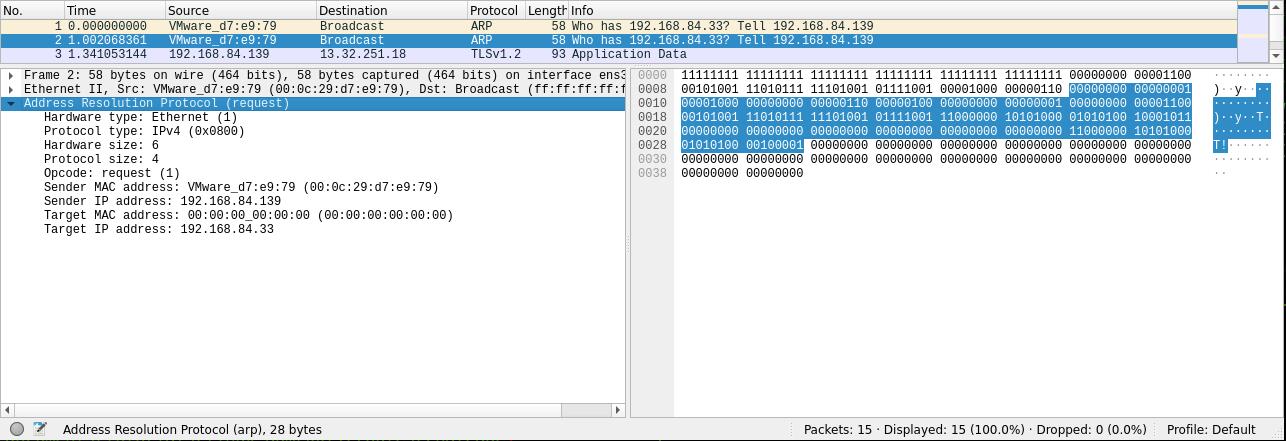
Using tools like arping we can send 3 apr requests to find the host .33 on the network and get no response.
sudo arping -c 3 192.168.84.33
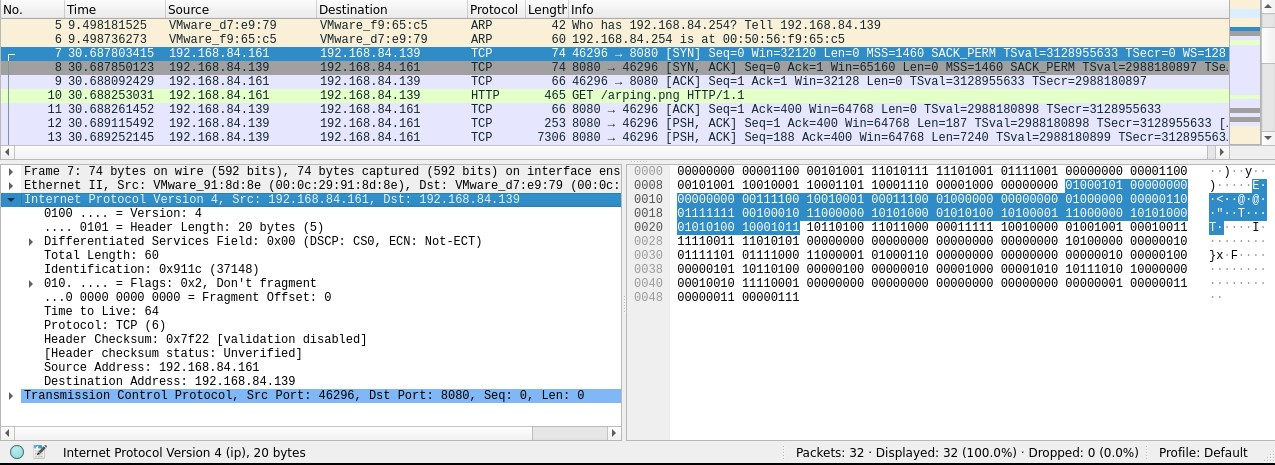
Capture the network packets and investigate with wireshark.
Now sending the arp for the host .161 which we know the host exist on the network and we can see the response from the host with arp reply.
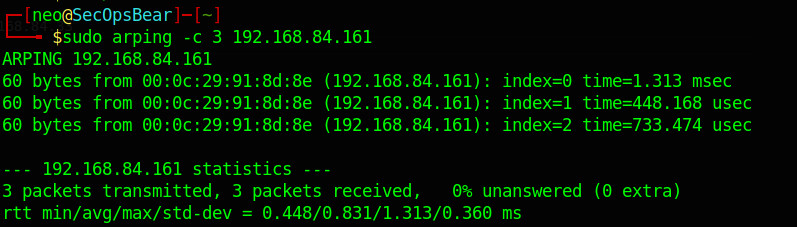
ARP Broadcast packet
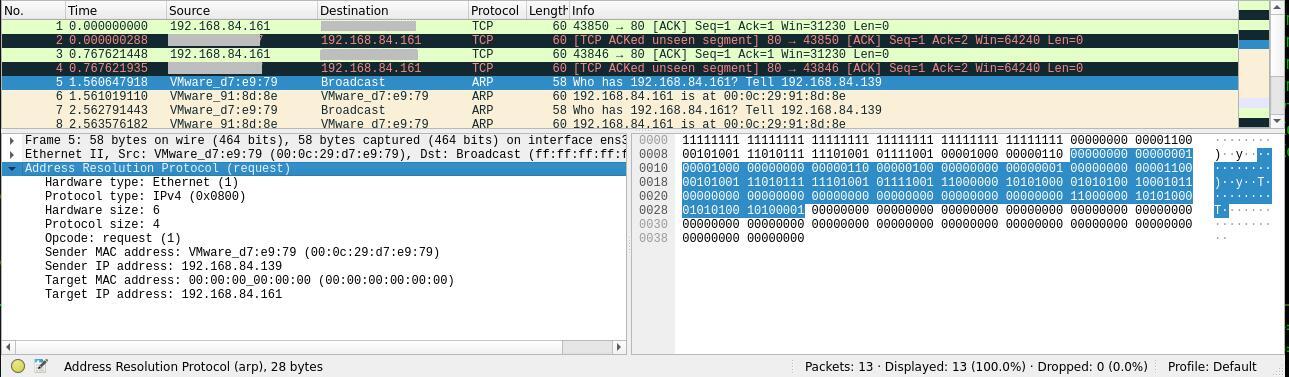
Now we can see the ARP reply from the host .161